What is Adaptive Malware and How to Stay Ahead
As cybersecurity threats continue to evolve, a particularly dangerous type of malware has emerged: adaptive malware. Unlike traditional threats, adaptive malware can change its behavior, appearance, and tactics to avoid detection, making it significantly harder to remove. If you’re a Windows user, staying ahead of these intelligent threats is critical to maintaining system integrity and performance.
How to Stay Ahead of Adaptive Malware?
1. Keep Windows Updated
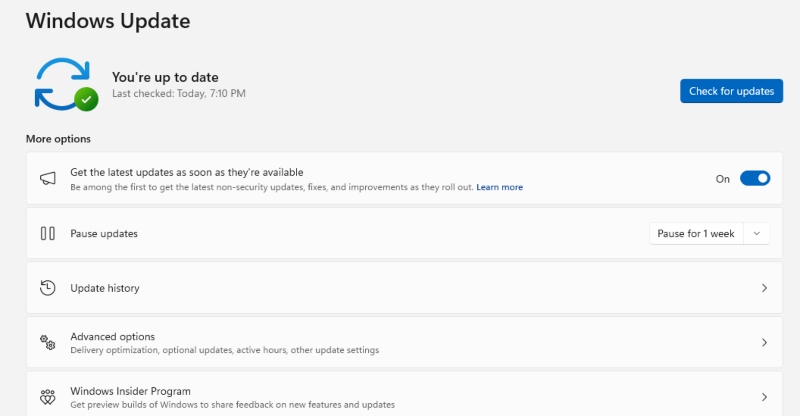
Updating your system is one of the easiest yet most overlooked defenses.
How to update Windows 10/11:
- Press Windows + I to open Settings.
- Go to Update & Security (Windows 10) or Windows Update (Windows 11).
- Click Check for updates.
- Install all available updates and restart if prompted.
2. Restrict User Permissions
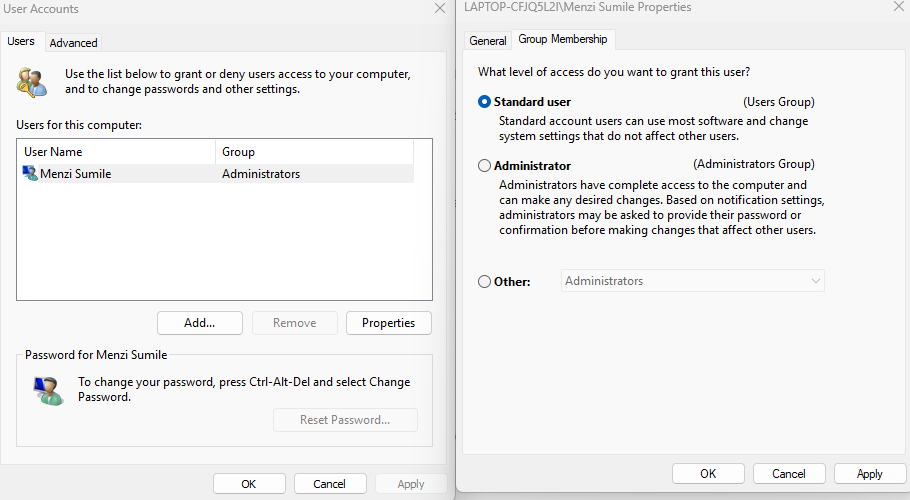
Avoid using administrator accounts for daily activities.
How to restrict user access:
- Press Windows + R, type netplwiz, and press Enter.
- Select the user account.
- Click Properties > Group Membership.
- Choose Standard user, then Apply.
3. Enable Controlled Folder Access
This feature prevents unauthorized apps from modifying protected files.
Steps:
- Go to Windows Security > Virus & Threat Protection.
- Scroll down to Ransomware protection.
- Click Manage ransomware protection.
- Turn on Controlled folder access.
How Fortect Helps You Combat Adaptive Malware?
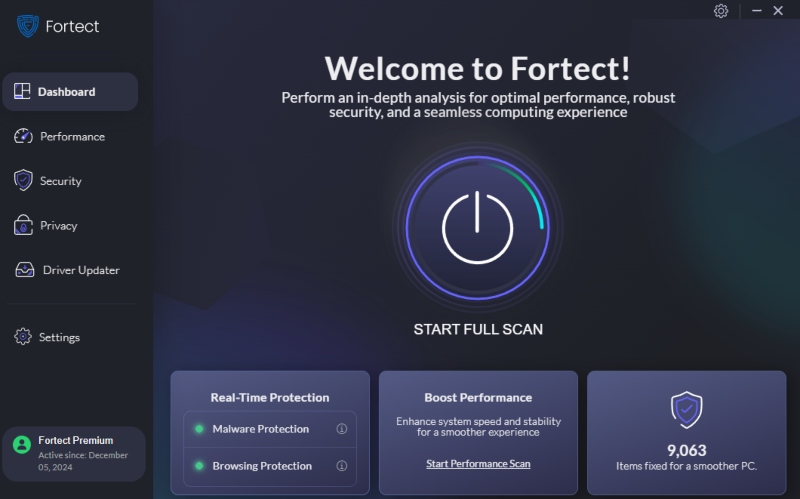
Fortect is more than just another antivirus; it’s more than any traditional defense that only knows the known threats. This tool provides real-time malware protection that protects and avoids adaptive threats. It actively scans your system for evolving threats, such as polymorphic malware, and then automatically repairs any damage and optimizes system health.
Beyond its well-known real-time malware protection, Fortect offers three standout features that make it a complete security solution.
Fortect’s Best Features for Security and Optimization
Fortect Browsing Protection
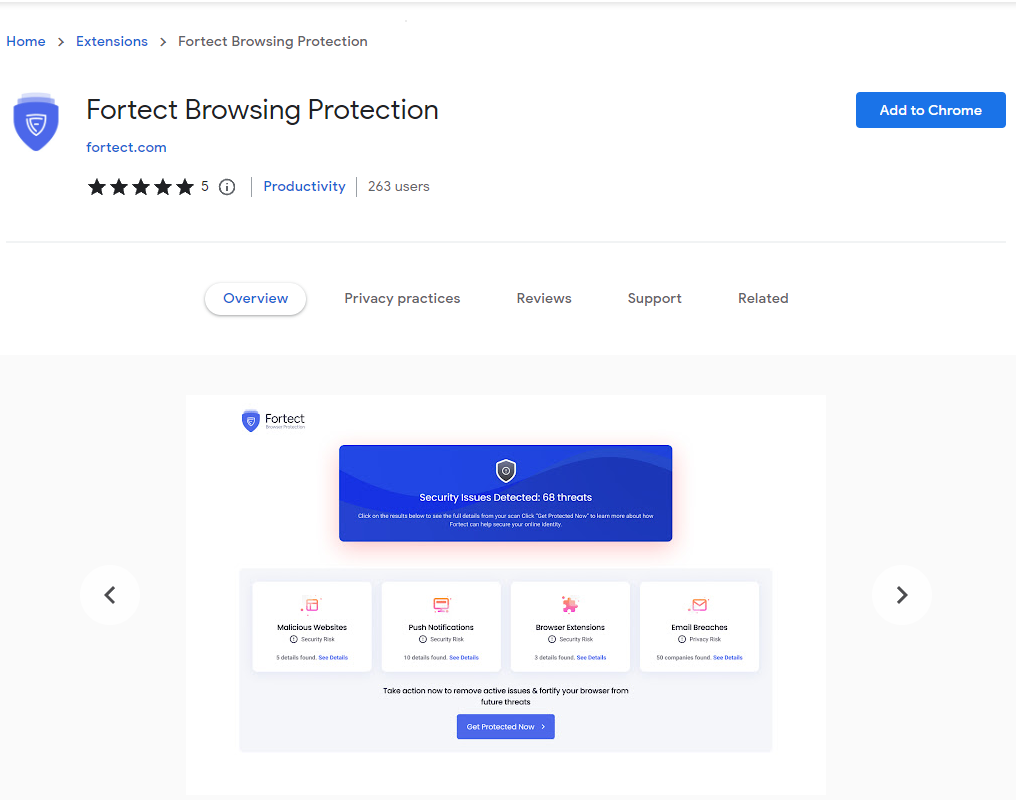
Fortect Browsing Protection blocks malicious websites and script-based threats in real-time.
How to install on Chrome:
- Open Chrome browser.
- Go to Chrome Web Store.
- Search for Fortect Browsing Protection.
- Click Add to Chrome, then confirm.
This browser add-on helps stop AI-generated phishing sites and unsafe downloads before they can do harm.
Fortect Mobile Security

If you’re a Fortect Premium user on Windows, you can extend protection to your Android phone.
Fortect Mobile Security Key Features:
- Real-Time Protection – Stops mobile threats immediately
- Malware Detection – Identifies and removes dangerous apps
- Instant Alerts – Notifies you of real-time threats
- Cloud-Based Scanning – Fast and efficient threat analysis
- Automated Fixes – Repairs issues without user action
- Scheduled Scans – Keeps your Android secure around the clock
Fortect Driver Updater
Fortect’s driver updater is a built-in feature that scans for outdated or corrupted drivers and updates them automatically, reducing vulnerabilities that adaptive malware can exploit.
Examples of Adaptive Malware
Adaptive malware includes a variety of types that modify their behavior or structure to evade detection and persist in systems. These include:
- Trojans – Malicious software disguised as legitimate tools, which adapt based on the system environment.
- Ransomware – Encrypts data and evolves its delivery and evasion techniques.
- Polymorphic Malware – Rewrites its code frequently to bypass signature-based detection.
- Fileless Malware – Operates in memory rather than installing files, making it harder to detect.
- Metamorphic Malware – Rewrites its code entirely with each infection to avoid detection.
- Rootkits – Hide deep within the system and adapt to avoid discovery by altering core OS functions.
- Worms with adaptive spread logic – Change propagation techniques based on network configuration.
- AI-powered Malware – Learns user behavior and system patterns to time its attacks or avoid security measures.
What Makes It “Adaptive”?
Adaptive malware uses AI, machine learning, and behavioral analysis to learn from its environment. Once installed on a system, it observes how the machine operates and adjusts its code or execution strategy to avoid detection by antivirus tools or endpoint protection systems.
How Adaptive Malware Works?
- Dynamic Code Injection: Alters code structure in real-time.
- Polymorphic Techniques: Changes its signature to avoid antivirus definitions.
- Sandbox Detection: Pauses execution if it senses a virtual environment.
- Target-Specific Behavior: Adapts based on OS version, security tools, or user habits.
Why Windows Systems Are at Risk
Windows 10 and 11 are often targeted due to their widespread use and default security features, which many users do not customize or monitor. Adaptive malware exploits unpatched software, user privileges, and predictable behaviors to persist and spread.
Signs Your PC May Be Infected
- Random system crashes or software glitches
- Slow performance even after rebooting
- Suspicious background processes or high CPU usage
- Modified system settings without user action
- Disabled Windows Defender or other security tools
Conclusion
Adaptive malware represents the next frontier of cyber threats, smart, stealthy, and capable of bypassing conventional defenses. But with proactive measures like updating your system, limiting access, and using intelligent tools like Fortect, you can stay a step ahead. Fortect offers a robust defense against ever-evolving malware by combining real-time protection with powerful optimization and repair tools.
Stay prepared, stay protected, and let Fortect handle the rest.




