How to Avoid Fileless Malware on Your Windows PC
With the advancement and demands of the internet, traditional malware attacks are no longer the only threat to your computer. Cybercriminals have evolved their tactics, giving rise to more sophisticated forms of cyberattacks, such as file-less malware. Unlike conventional malware, fileless malware doesn’t rely on files or software installed on your system.
Instead, it operates in the computer’s memory, making it incredibly difficult to detect and remove. We will guide you through fileless malware, explaining how it works and the strategies you can implement to protect your Windows PC from such threats.
What is Fileless Malware and How Does it Work?
Fileless malware is malicious software that doesn’t leave a trace on your hard drive. Instead of being installed like traditional malware, it resides in your system’s memory, making it nearly invisible to standard antivirus programs. Fileless malware exploits legitimate programs and processes to execute its payload, often using scripting languages like PowerShell or exploiting system vulnerabilities.
The malicious code can be injected directly into running processes, which means it doesn’t need to download any files, making it harder to detect and remove.
The stealthy nature of fileless malware allows it to avoid many traditional security measures, leading to potential breaches and data loss if not adequately addressed. Because it’s difficult to trace and remove, understanding how to detect and prevent file-less malware is crucial for protecting your system.
Fileless Malware Detection and Prevention Strategies
Don’t Click on Suspicious Links
One of the most common ways file-less malware is introduced to a system is through phishing emails and malicious links. Cybercriminals often use social engineering tactics to trick users into clicking on a link or downloading an attachment that appears legitimate. Once clicked, these links can initiate the execution of fileless malware in your system’s memory.

To protect yourself:
- Be extremely cautious when receiving emails from unknown sources.
- Even if an email seems to be from a trusted sender, scrutinize the content and avoid clicking on links or downloading attachments unless you are sure they are safe.
- Consider using a web browser that warns you about suspicious websites and links, adding an extra layer of protection.
Keep Your Devices Up-to-Date
Outdated software and operating systems are prime targets for fileless malware attacks. Cybercriminals often exploit known vulnerabilities in un-updated software. You can prevent many of these potential exploits by keeping your Windows PC and all installed software up-to-date.
To check if your Windows is up to date:
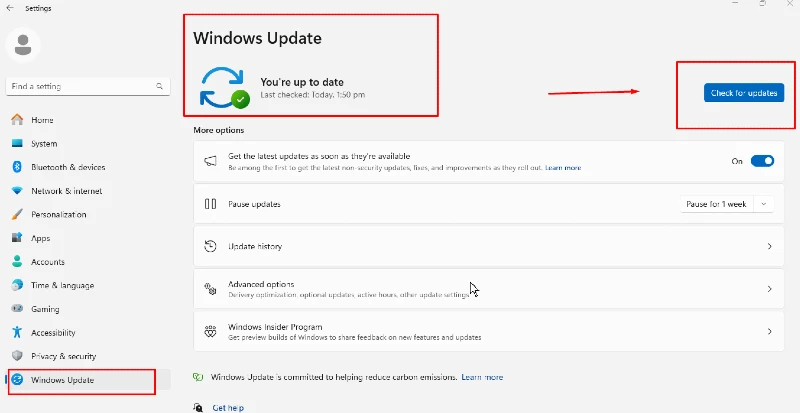
Start > System > Windows Update ( lower left ) > If Windows is up to date, it will show here; if not > Click on the Updates button or Install Update.
Make sure that your system’s automatic update feature is enabled. This will ensure you receive and install the latest patches as soon as they are released. This proactive approach helps reduce the risk of fileless malware exploiting known vulnerabilities in your system.
Disable Non-Essential Programs
Many file-less malware attacks exploit unused or rarely used programs with vulnerabilities. Disabling or uninstalling non-essential software reduces the potential entry points for malware. For instance, if you don’t use PowerShell or other scripting tools, consider disabling them to minimize risk.
To reduce the risk of fileless malware on your Windows 10/11 PC:
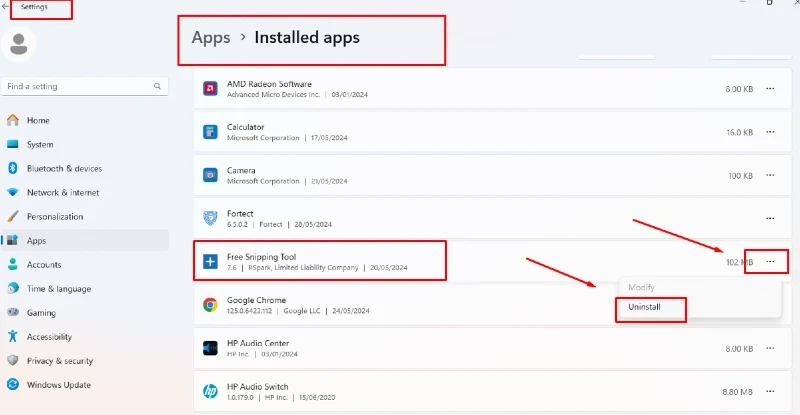
Uninstall Unused Programs: Go to Settings > Apps, select programs you don’t use, and click Uninstall.
Disable Unnecessary Features: Press Windows + R, type optional features, uncheck features like PowerShell and click OK.
Manage Startup Programs: Open Task Manager with Ctrl + Shift + Esc, go to Startup, and turn off unnecessary programs.
Turn off Unnecessary Services: Press Windows + R, and type services. MSc, right-click on services and set the Startup type to Disabled.
Monitor Your Network’s Traffic
Monitoring network traffic helps detect signs of fileless malware. Use monitoring tools to spot unusual activities, like unexpected connections, and review logs regularly to quickly catch and respond to threats.
To monitor your Windows 10/11 PC network traffic:
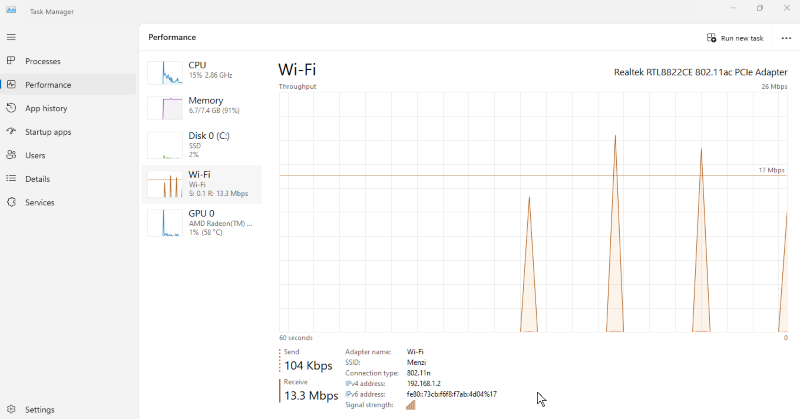
Use Task Manager: Press Ctrl + Shift + Esc, go to the Performance tab, and select Wi-Fi or Ethernet to view essential network activity.
Check Resource Monitor: Press Windows + R, type resmon, and go to the Network tab for detailed traffic analysis.
Review Router Logs: Access your router’s admin panel to check for unusual traffic patterns or unknown devices.
Consider Third-Party Solutions
Given the stealthy nature of fileless malware, traditional antivirus software may not be sufficient to detect and prevent these attacks. Consider investing in third-party security solutions like Fortect to address advanced threats like file-less malware.
Fortect Premium automatically scans and detects any threat, such as file-less malware, provides real-time notification, and removes the malware. It also mitigates threats that might go unnoticed by conventional antivirus programs.
These solutions often use advanced machine learning algorithms to detect abnormal behavior, even if the malware doesn’t leave a traditional footprint on your system.
Download and install Fortect now.
Conclusion
Fileless malware presents a unique challenge due to its ability to evade traditional detection methods. However, by understanding how it works and implementing proactive strategies, you can significantly reduce the risk of infection. Be vigilant about the links you click, keep your software up-to-date, turn off unnecessary programs, monitor your network traffic, and consider using specialized third-party security solutions.
By taking these steps, you can protect your Windows PC from the growing threat of fileless malware and keep your data safe.




