Securing Your Windows Hosts File from Redirection Attacks
The Windows hosts file is a small but powerful system file that maps domain names to IP addresses. While it’s often used for troubleshooting or local testing, attackers can exploit it to perform redirection attacks, sending you to malicious websites without your knowledge. Protecting this file is critical to keeping your system safe from phishing, malware, and data theft.
What Is a Hosts File Redirection Attack?
A host file redirection attack happens when malware or an unauthorized user modifies the Windows hosts file to reroute traffic. For example, when you try to visit your bank’s website, the altered hosts file might redirect you to a fake lookalike site designed to steal your login credentials.
Why Attackers Target the Hosts File
- Bypasses DNS security – Hackers can control domain resolution locally.
- Phishing opportunities – Redirects to malicious or spoofed websites.
- Malware persistence – Some malware uses host file changes to block antivirus updates.
Signs Your Hosts File Has Been Compromised
- You’re redirected to suspicious websites even when typing the correct URL.
- Your antivirus or security tools cannot update.
- The hosts file shows unfamiliar entries when opened in Notepad.
How to Protect the Hosts File on Windows
Restrict User Permissions on the Hosts File
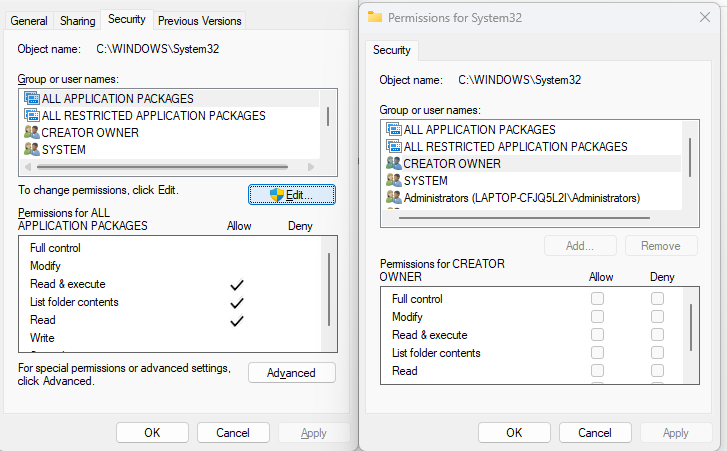
By default, the hosts file is located at:
C:\Windows\System32\drivers\etc\hosts
Restricting permissions makes it harder for malware or unauthorized users to edit it.
Steps (Windows 10/11):
- Press Win + E to open File Explorer.
- Navigate to C:\Windows\System32\drivers\etc\.
- Right-click the hosts file → select Properties.
- Go to the Security tab → click Edit.
- Select Users and set Read-only permission (remove Write access).
- Click Apply and OK.
Enable Windows Defender Real-Time Protection
Windows Defender helps block unauthorized modifications to system files like hosts.
- Go to Settings > Update & Security > Windows Security.
- Open Virus & threat protection.
- Ensure Real-time protection is turned ON.
Regularly Check the Hosts File
- Open Notepad as Administrator.
- Go to File > Open and paste the path: C:\Windows\System32\drivers\etc\hosts.
- Look for suspicious entries that redirect common websites (e.g., google.com, microsoft.com).
Keep Windows Updated
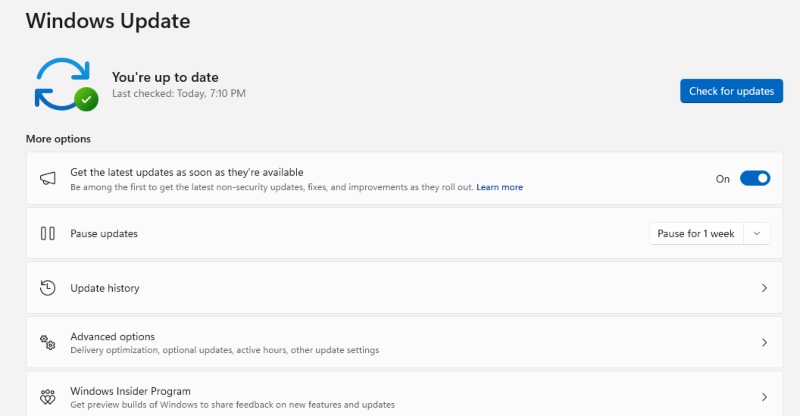
Microsoft frequently releases patches to prevent malware from exploiting security weaknesses.
Steps (Windows 10/11):
- Press Win + I to open Settings.
- Click Update & Security (Windows 10) or Windows Update (Windows 11).
- Select Check for updates.
- Install available updates and restart your PC if required.
Prevent Hosts File Attacks with Fortect
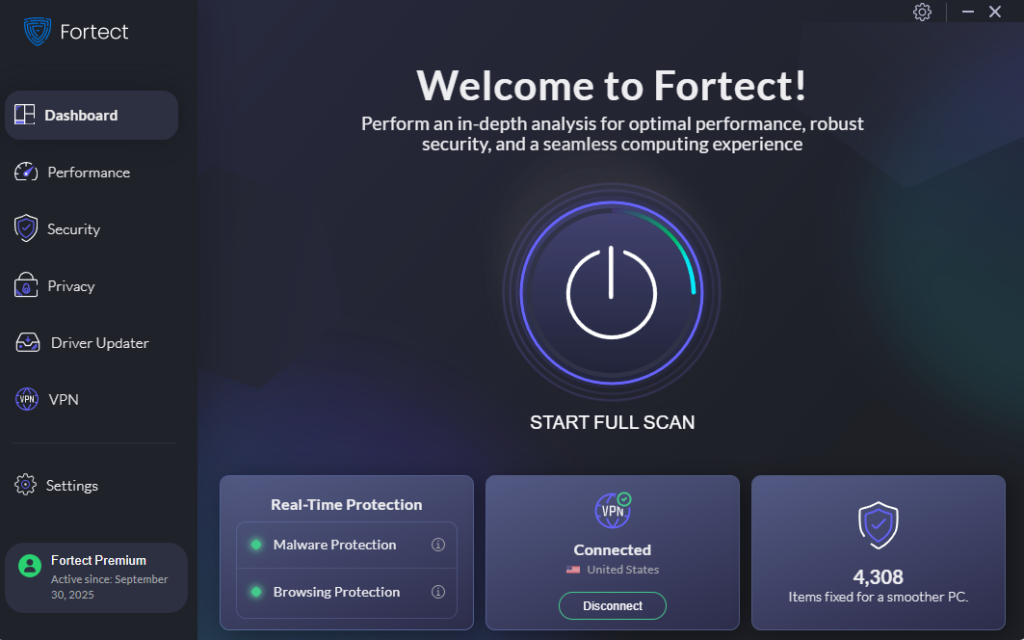
Fortect is a powerful antivirus tool, surpassing any traditional antivirus, with real-time malware protection. It automatically scans your Windows PC for threats such as host file redirection malware, spyware, and unauthorized file changes. If it detects suspicious modifications, Fortect restores your system while also optimizing performance.
Steps to Use Fortect for Extra Protection:
- Download and install Fortect on your Windows PC.
- Launch the app and run a Full System Scan.
- If threats are detected, select Repair All to remove them and restore stability.
- Keep Fortect running in the background for real-time protection.
Redirection Attacks on macOS
Redirection attacks on macOS occur when cybercriminals manipulate the system’s hosts file or install malicious configuration profiles to divert your traffic to fake or compromised websites. These attacks are dangerous because they can lead to phishing scams, identity theft, and unauthorized data access. While macOS includes built-in defenses, attackers are becoming more sophisticated, making extra protection essential.
How Fortect Protects macOS Users
Fortect offers real-time defense against malicious redirection attempts by monitoring system integrity and blocking unauthorized modifications. Its cloud-based intelligence and enhanced antivirus engine ensure threats are detected and resolved before they can cause harm. With features like unsafe Wi-Fi alerts, web protection, and breach detection, Fortect provides a complete security layer for macOS users against redirection attacks and evolving online threats.
How to Prevent Redirection Attacks on macOS
- Keep macOS Updated: Always install the latest Apple security patches to fix known vulnerabilities.
- Avoid Suspicious Profiles: Do not install unverified configuration profiles that may alter system settings.
- Secure DNS Settings: Use trusted DNS providers or enable DNS over HTTPS for encrypted browsing.
- Limit Admin Rights: Avoid using accounts with full admin access for everyday tasks.
- Use Security Tools: Employ robust security software to detect unauthorized changes and block malicious redirects.
Conclusion
The Windows hosts file is a powerful tool, but in the wrong hands, it can be used to trick you into visiting malicious websites. By restricting access, keeping your system updated, and using security software like Fortect, you can defend against redirection attacks and keep your sensitive data safe.



