Real-World Examples of Script-Based Attacks
Script-based attacks are among the most deceptive and difficult threats to detect in cybersecurity. Unlike traditional malware, which leaves files on the disk, fileless malware and script-based attacks operate in memory, using legitimate system tools like PowerShell, WMI, or JavaScript to carry out malicious actions. This makes them stealthy, persistent, and dangerous, especially for Windows users.
We’ll break down real-world examples, explain how these attacks work, and show how to protect your Windows 10/11 PC from such threats.
What Are Script-Based Attacks?
Script-based attacks use scripting languages (such as PowerShell, JavaScript, VBScript, or Batch) to execute malicious code. They often don’t write files to disk, making them harder for antivirus software to detect. These attacks are commonly referred to as fileless malware.
Common Entry Points for Script-Based Attacks
- Phishing emails with malicious links or attachments
- Compromised websites running malicious JavaScript
- Infected macros in Microsoft Office documents
- Abuse of legitimate Windows tools like PowerShell and WMI
Real-World Examples of Script-Based Attacks
1. Emotet Malware Using PowerShell
Originally a banking Trojan, Emotet evolved into a fileless malware delivery system. It often arrived via phishing emails with malicious Word documents. Once opened, a macro would run PowerShell commands to download additional payloads, all without leaving traces on the disk.
2. Kovter: A Fully Fileless Trojan
Kovter is a classic fileless malware that resides in the Windows registry. It uses JavaScript and PowerShell to execute commands from memory. Kovter often spreads through fake software updates or infected websites.
3. Cobalt Strike Beacon
Although Cobalt Strike is a legitimate penetration testing tool, cybercriminals use its Beacon component to execute malicious scripts, establish persistence, and exfiltrate data, all while avoiding detection.
4. APT29 (Cozy Bear) Attacks
Associated with Russian state-sponsored hackers, APT29 used WMI (Windows Management Instrumentation) and PowerShell scripts to create backdoors on compromised systems during the 2020 U.S. government cyberattacks.
How to Protect Your Windows PC from Script-Based Attacks
Here’s a practical guide to minimize your exposure to these threats on Windows 10/11:
1. Restrict Script Execution
You can limit PowerShell access for non-admin users.
Steps to restrict PowerShell:
- Press Windows + X, then click Windows PowerShell (Admin).
Run the command: mathematica - Set-ExecutionPolicy Restricted.
- Type Y and press Enter to confirm
This disables the ability to run scripts unless explicitly allowed.
2. Keep Windows Updated
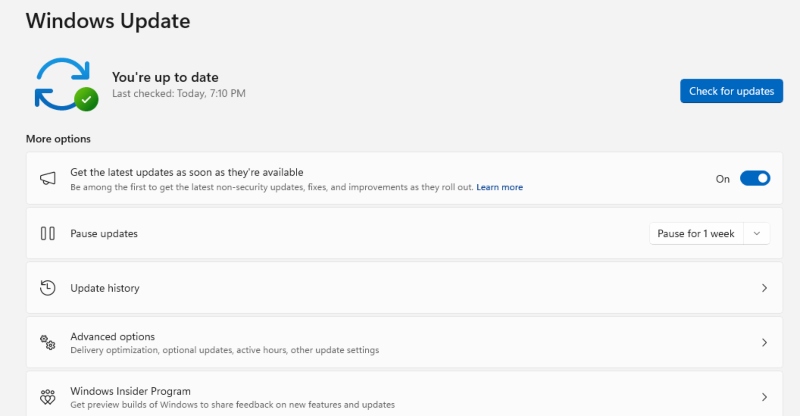
Microsoft frequently patches vulnerabilities exploited by these attacks.
To update Windows 10/11:
- Press Windows + I to open Settings.
- Go to Update & Security > Windows Update.
- Click Check for updates, then install available updates.
3. Disable Macros in Office Documents
Malicious macros are often used to launch script-based payloads.
Steps to disable macros:
- Open any Office app (e.g., Word).
- Go to File > Options > Trust Center.
- Click Trust Center Settings, then select Disable all macros with notification.
4. Use Real-Time Protection
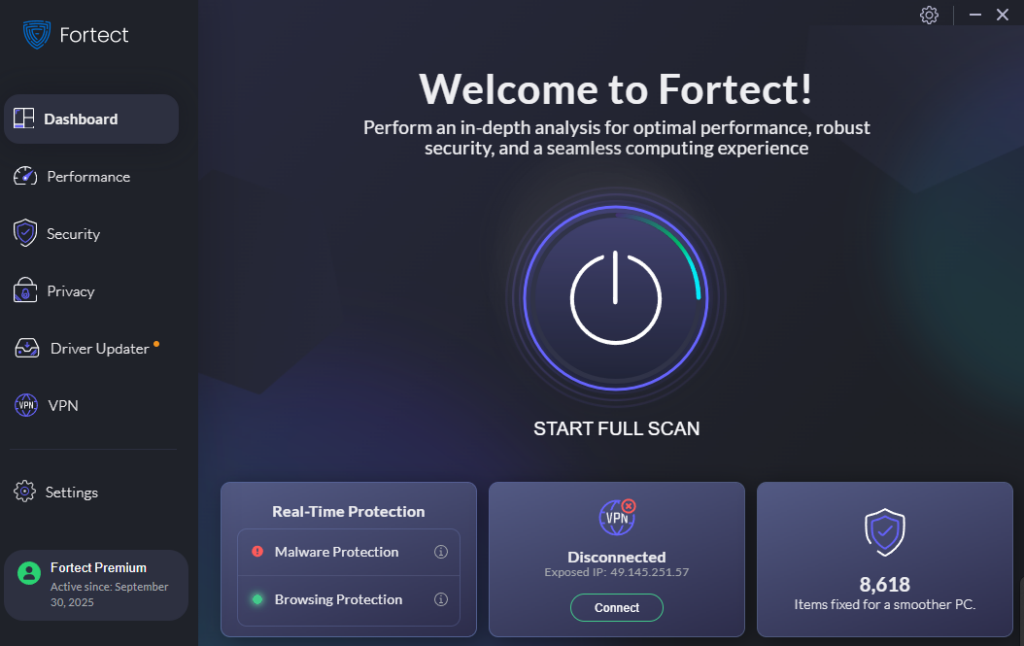
Relying solely on Windows Defender may not be sufficient, especially against advanced script-based threats. Real-time, behavior-based antivirus tools are essential.
How Fortect Helps Defend Against Script-Based Attacks
Fortect is a powerful antivirus and optimization tool with real-time protection specifically designed to detect and prevent threats like fileless malware, script-based attacks, and hidden exploits.
Here’s how Fortect keeps your Windows PC safe:
- ✅ Real-time malware protection that identifies and blocks suspicious PowerShell and JavaScript activity.
- ✅ Automatic threat removal and registry repair, neutralizing infections like Kovter and Emotet.
- ✅ System optimization: Cleans up junk files, repairs corrupted Windows files, and removes crashed program traces.
- ✅ Boosts performance and ensures system stability even after an attack.
Whether you’re recovering from a hidden script-based attack or want to stay protected in real-time, Fortect is the smart defense layer your Windows 10/11 PC needs.
Fortect doesn’t just detect threats, it fixes the damage and restores your PC to peak condition. Fortect also features cross-platform functionality with your Android devices, such as its mobile security and browser extension features:
Fortect Mobile Security: Effortless Protection for Your Android

If you’re using Fortect Premium on your Windows device, you also unlock access to Fortect Mobile Security, a powerful, cross-platform solution that keeps your Android phone secure in real-time.
Built for today’s mobile lifestyle, Fortect Mobile offers seamless, automated protection without sacrificing speed or usability.
Key Features of Fortect Mobile:
- ✅ Real-Time Threat Blocking – Stops malware and suspicious activity before they can harm your device.
- ✅ Smart Malware Detection – Quickly identifies and removes mobile threats like spyware and trojans.
- ✅ Proactive Alerts – Notify you immediately about any unusual activity or risk.
- ✅ Cloud-Powered Scanning – Enables fast, lightweight security checks on demand.
- ✅ Self-Healing System – Automatically fixes detected issues with minimal user input.
- ✅ Scheduled Protection – Set routine scans to ensure your Android stays secure around the clock.
Whether you’re switching between your Windows PC and your Android device, Fortect keeps your entire digital life protected, without slowing you down.
Fortect Browsing Protection: Safer Surfing, Real-Time Defense
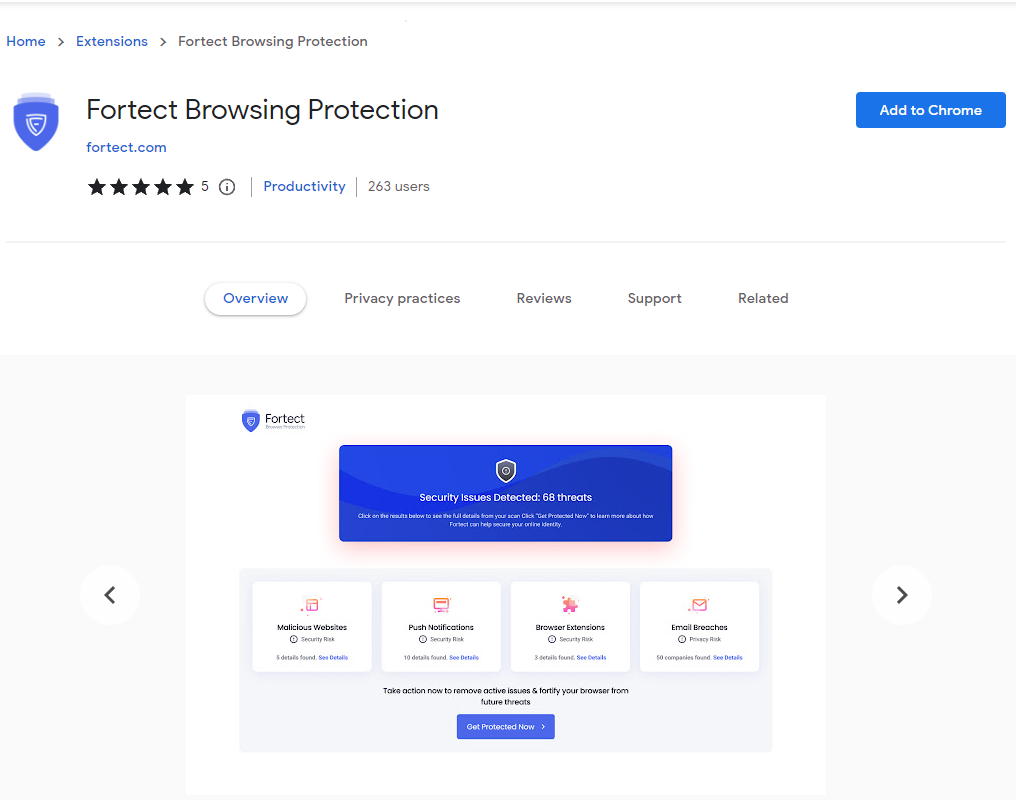
Fortect also includes Browsing Protection, a robust browser extension that safeguards your online activity in real time. It actively blocks access to malicious websites, phishing attempts, and other web-based threats, giving you peace of mind while you browse.
Whether you’re shopping, banking, or researching, this extension adds an essential security layer to your Chrome browser, protecting you from hidden dangers across the web.
How to Install Fortect Browsing Protection on Chrome:
- Open your Google Chrome browser.
- Visit the Chrome Web Store and search for “Fortect Browsing Protection.”
- Click Add to Chrome, then confirm by selecting Add Extension.
- Once installed, you’ll see the Fortect icon in your browser toolbar, and protection starts immediately.
With Fortect Browsing Protection, you can explore the internet confidently, knowing you’re shielded from deceptive websites and dangerous downloads.
Download and install Fortect now to get all the protection you need on the internet.
Why Script-Based Attacks Are So Dangerous
- Fileless attacks evade traditional antivirus detection.
- They abuse built-in Windows tools, making them appear legitimate.
- Often triggered through social engineering tactics like phishing.
- Persist in memory or registry, leaving minimal forensic evidence.
Conclusion
Script-based attacks like fileless malware are evolving fast, and traditional detection methods often fall short. Whether it’s Emotet using PowerShell or registry-resident threats like Kovter, the risks are real and persistent. The key lies in proactive defense: restrict script execution, stay updated, and use behavior-aware protection like Fortect.
By taking these steps, you can outsmart even the most silent and stealthy malware hiding in your system.




