How do Hackers Use DLL Files? Useful to Know
Are you concerned about the security of your computer systems? You should be. One of the most insidious techniques hackers use to compromise systems is through DLL files. This guide will delve deep into how hackers exploit Dynamic Link Library (DLL) files to gain unauthorized access, steal data, and much more. We’ll also discuss how you can protect yourself from such attacks.
What are DLL Files?
DLL stands for Dynamic Link Library. These files serve as a repository of functions and procedures that multiple programs can access and use. They are essential for the smooth functioning of Windows operating systems.
How do Hackers use DLL files?
Hackers often exploit DLL files through a technique known as DLL hijacking. In this method, they replace legitimate DLL files with malicious ones. When a program tries to access a DLL file, it ends up executing the malicious code, thereby compromising the system.
Double DLL Sideloading
An advanced form of DLL hijacking is double DLL sideloading. In this technique, hackers use multiple layers of DLL files to evade detection. They often use clean applications as initial vectors, which then sideload malicious DLL files.
The Stealth Factor
What makes DLL hijacking particularly dangerous is its stealthy nature. The attack often goes unnoticed, making it a potent tool for hackers to steal sensitive information, escalate privileges, and even take control of the system.
How Does DLL Hijacking Work?
- Identification: Hackers identify a program that dynamically loads DLL files.
- Search Order: They determine the search order the program uses to locate DLL files.
- Malicious Placement: A malicious DLL file is placed in a location that the program will search before finding the legitimate file.
- Execution: When the victim runs the program, it loads the malicious DLL, executing any code the hacker wishes.
Preventive Measures
1. Use Fully-Qualified Paths
Specify the full path when loading DLLs to prevent Windows from searching in unexpected locations.
How to do it? Pretty simple: instead of using a simple path such as:
C:\Program Files\Google to prevent random searches from all over your system you can specify the full path C:\Program Files\Google\Chrome\Application\1615.02.55638.1649 which is also known as a Fully-Qualified Path or Absolute path.
To find the path you can use the search function and then to copy and paste it where it is needed.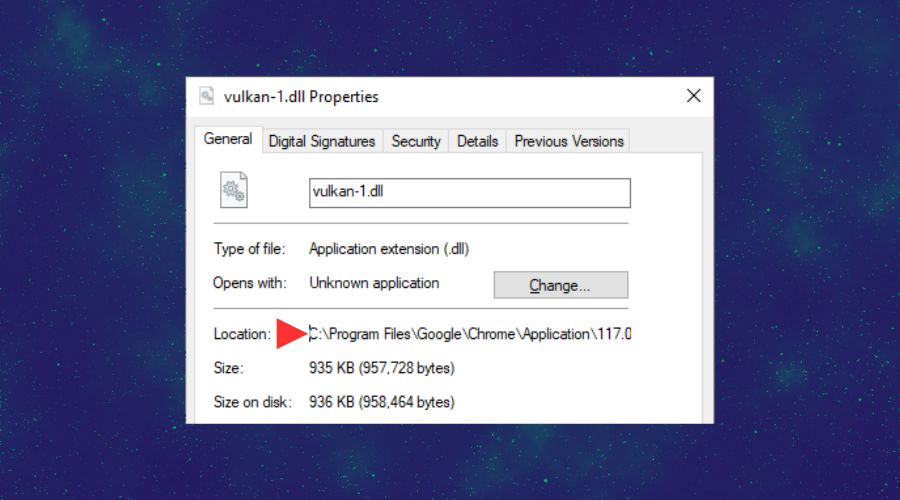
2. Trust Only Verified Software
Use software that is digitally signed and verified by trusted sources to fix your DLL problems.
For example, you can use Fortect to perform a series of checks, detect and remove malware, and fix your errors and DLLs. It helped me a lot with various things, as you can see from the image below.
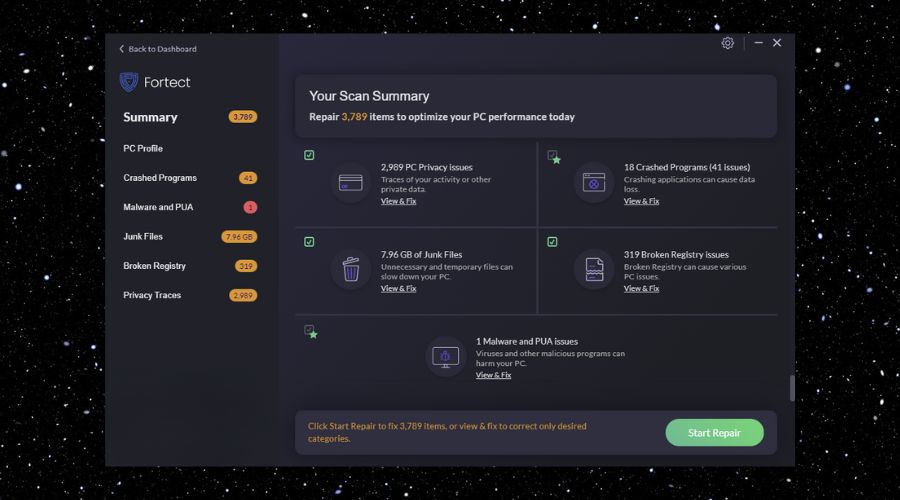
One of the great aspects of this tool is that it fixes broken registry issues and device privacy issues, aside from possible malware.
What’s also great about Fortect is that, by using it, you will have a tailor-made application for your system that provides an all-in-one solution to your problems. Additionally, it only takes a couple of minutes to install and run it. If you are wondering how to do it, check the steps below.
- Download Fortect
– Go to the Fortect website and download the application.
2. Install and Run Fortect
– Follow the installation instructions.
– Once Fortect is installed, run it as an administrator to ensure that it works at full capacity. Additionally, you can set it to run as an administrator permanently from the Compatibility tab as seen below. To access it, just right-click on the app and select properties.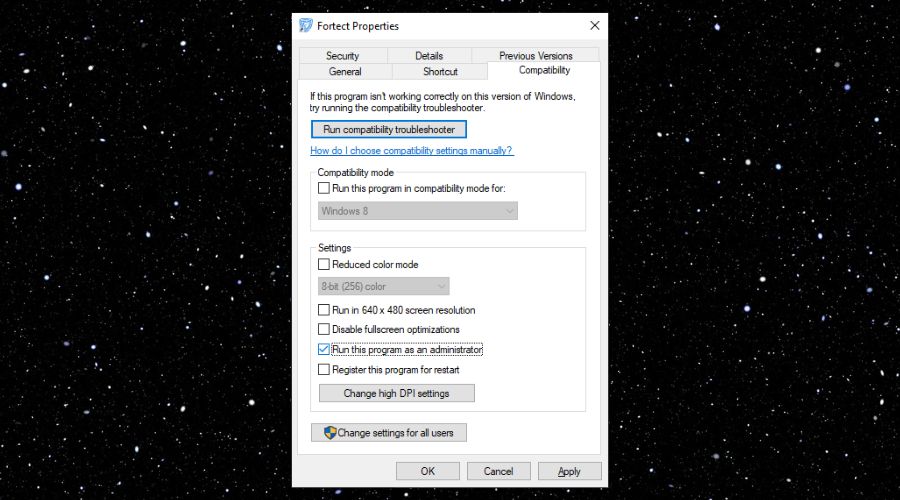
– From now on you will open Fortect as an administrator.
Now that you have installed the application, you are good to go. You can use Fortect to fix your problems in no time and with ease.
3. Implement Access Controls
– Use access controls on directories where DLL files are stored to prevent unauthorized access.
– How to: The easiest way to implement access controls is through Control Panel via the User Controls service as seen below.
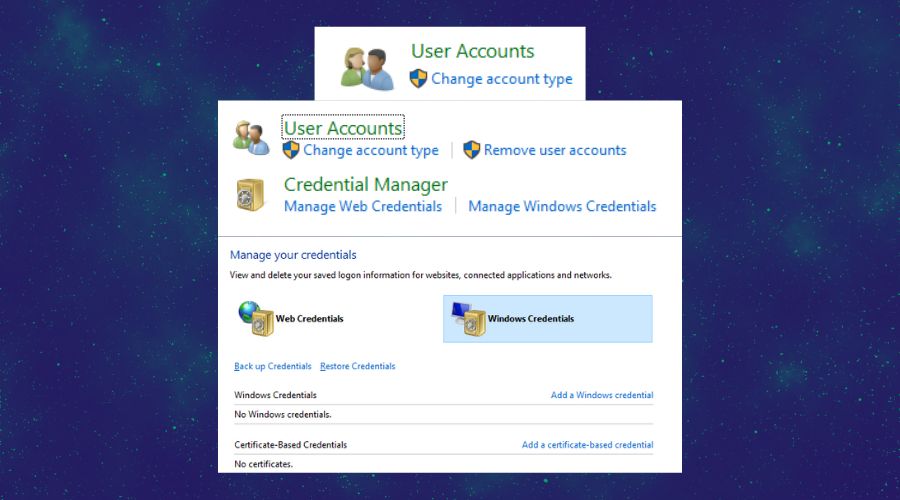
– Once you end up selecting the Windows credentials, you can set some conditions. Additionally, if you decide to use the user account settings, you can change the account type of your system users. This will help you later on because you will be able to set which programs are used by whom.
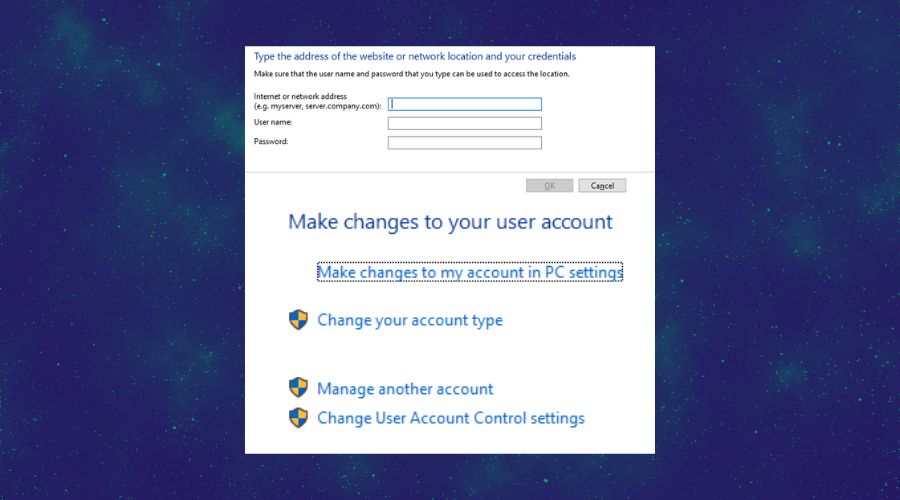
– As you will see below, you can set different rules when it comes to the application security settings. Thus, you can set some limits for the people using your system.
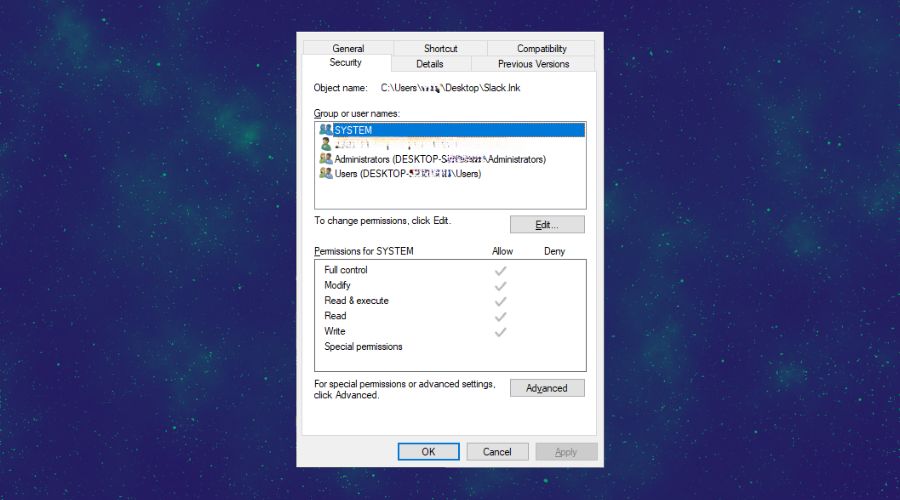
4. Regular Security Audits
Conduct regular security audits to identify vulnerabilities. An auditor will verify several areas to check if there are any vulnerabilities available. The main ones are:
- Network weaknesses: During this process the auditor will check the trafic, emails, files and other communication-related aspects such as messages.
- Security: Besides having an antivirus and an antimalware, the auditor will also check how well the other security policies and procedures are implemented, especially on commonly used devices.
- Encryption: As you might already know, most messaging applications are having encryptions which protect the data from being stolen. An encryption works by coding your text into a mathematical text. Thus a “Good Morning” from a friend will appear as a “425WPE7SXLbrhKmhnx7oNQ==”
- Software Systems: The auditor will check most of the vulnerable applications, which might be targeted by hackers. Also, during this phase, some additional areas are verified, such as the ones storing and processing the data. Additionally, the auditor will check to see if all of the controls meant to protect your information are in place and working.
- Development: While it doesn’t seem as important or potentially harmful, the apps and systems in development are also thoroughly checked by the audit to ensure that they won’t represent a potential threat to your data.
Useful Resources to Prevent Future Problems:
If you are interested in finding out more tools to use to deal with the problems you are facing or to prevent future issues, check out the guides below:
- Best DLL Fixer: If you consider that any of your DLLs are corrupted or faulty, you should try using a fixer, and in this guide, you will find a few of them that have been tested.
- Best Tune-Up Tools for PC: In this guide, you will find some of the best Tune Up Tools for your PC, they are well-reviewed to help you decide which one suits you best.
- Registry Fixer: If you have ever modified registry files or used third-party cleaning apps to uninstall applications, this guide is for you. When I was inexperienced, I tried uninstalling some applications, checked the clean registry option of the software I was using, and ended up having registry-related issues, which are frustrating to deal with.
- Best Software Against Malware: If you are using the internet to download applications frequently or to access a variety of websites, you should make sure that you have something protecting you from malware.
- Best Windows Repair Tools: Besides using the troubleshooters provided by Windows, which are more or less reliable, try to use one of the repair tools featured to decrease the time spent searching every corner of your system.
Understanding how hackers use DLL files helps you take the first step in making your computer system more secure. Follow the preventive measures in this guide to improve your system’s security.




![Why Do DLL Files Get Corrupted? [Causes & Fixes]](https://wp-cdn.fortect.com/uploads/2023/04/20082410/why-are-dll-missing-425x300.jpg)