Windows Script Host Exploits: Script Attacks Return
Script-based attacks have made a strong comeback, with cybercriminals increasingly exploiting Windows Script Host (WSH) to run malicious scripts on Windows 10 and 11 systems. Once seen as an outdated attack vector, WSH has re-emerged as a powerful entry point for delivering malware and executing unauthorized commands.
We will take a look at what WSH is, how attackers exploit it, how to protect your PC, and why regular monitoring is critical.
What Is Windows Script Host (WSH)?
Windows Script Host is a Windows automation tool that allows users to run VBScript and JScript files outside of web browsers. These scripts can automate tasks or execute system-level commands, making WSH useful for IT administrators, but also attractive to hackers.
Common File Extensions Used in WSH Attacks
- .vbs (VBScript)
- .js (JScript)
- .wsf (Windows Script File)
- .wsh (WSH settings file)
SOLVED: Windows Script Host Exploits
Restrict WSH Execution via Group Policy (Windows 10/11 Pro and Enterprise)
- Press Win + R, type gpedit.msc, and press Enter.
- Navigate to: User Configuration > Administrative Templates > Windows Components > Windows Script Host
- Double-click Allow Windows Script Host.
- Select Disabled, then click Apply and OK.
Keep Windows Updated
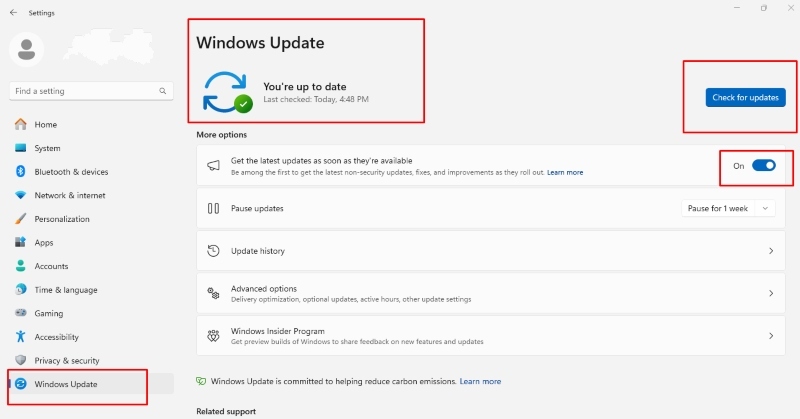
- Open Settings with Win + I.
- Go to Update & Security > Windows Update.
- Click Check for updates and install any available patches.
Use Windows Registry to Disable WSH (Windows 10/11 Home)
- Press Win + R, type regedit, and hit Enter.
- Navigate to: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows Script Host\Settings
- If not present, create a new DWORD (32-bit) value named Enabled.
- Set its value to 0 to disable WSH.
⚠️ Be careful when editing the registry. Back up your data first.
Remove and Prevent WSH Malware with Fortect
Automatically Detect and Fix Script-Based Threats
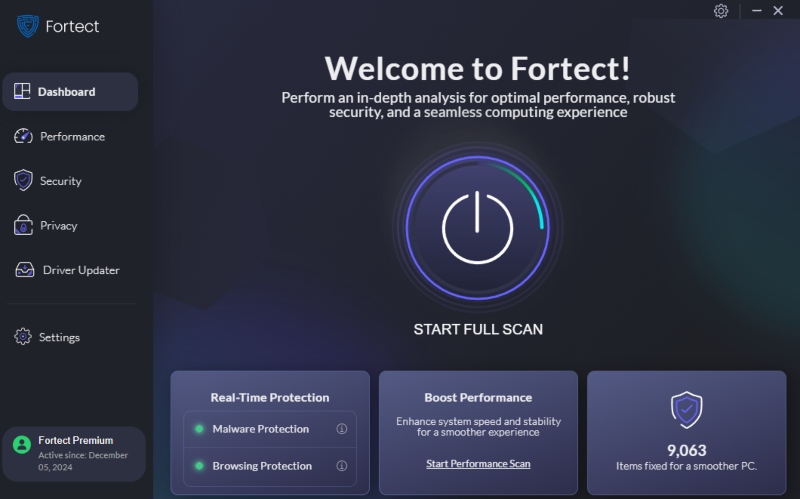
Fortect is a third-party antivirus tool with real-time malware protection. It automatically scans your Windows PC for threats like malicious WSH scripts, hidden trojans, and corrupted system files. Once detected, Fortect removes the threats and optimizes your system for smoother performance.
Steps to Use Fortect:
- Download and install Fortect from the official website.
- Launch the app and run a Full System Scan.
- Let Fortect detect WSH-based or script-related malware.
- Click Repair All to clean your system and apply optimizations.
Download and install Fortect today.
How Cybercriminals Exploit WSH
Attackers exploit WSH by disguising scripts as legitimate files or embedding them in phishing emails and malicious downloads. Once executed, these scripts can:
- Install backdoors or remote access trojans (RATs)
- Steal credentials or sensitive data
- Modify system settings or files
Real-World Examples
In many recent campaigns, attackers used JavaScript or VBScript attachments that download and execute payloads from remote servers. These scripts often avoid detection by using obfuscation techniques and running silently in the background.
Why WSH-Based Attacks Are Rising Again
- Low detection rates: Scripts can evade basic antivirus software.
- Built-in Windows feature: No external installation required.
- Remote execution: Scripts can be run without user interaction once triggered.
Conclusion
The exploitation of Windows Script Host represents a renewed threat in cybersecurity. These attacks are silent, effective, and increasingly sophisticated. By disabling WSH where unnecessary, keeping your system updated, and using real-time protection like Fortect, you significantly reduce your risk of infection. Don’t overlook script-based threats; stay proactive and secure your PC now.