SOLVED: VPN Data Logging Scandals on Windows
VPN data logging scandals have shaken user trust, with several providers caught secretly recording browsing histories, connection timestamps, and IP addresses despite “no-logs” promises. Windows users face unique vulnerabilities since many VPNs exploit system permissions to collect more data than necessary. This guide reveals how to protect yourself from deceptive logging practices and verify your VPN’s actual behavior on Windows 10 and 11.
Understanding VPN Logging Practices
What VPNs Actually Log
Most VPNs collect three types of data: connection logs (timestamps, bandwidth usage), usage logs (websites visited, DNS queries), and metadata (device information, IP addresses). While connection logs help maintain service quality, usage logs compromise privacy entirely. Several high-profile providers marketed as “zero-log” were exposed for storing complete browsing histories, which later surfaced in data breaches and legal proceedings.
Why Windows Users Are More Vulnerable
Windows grants VPNs extensive system access through TAP adapters and network drivers. These permissions allow legitimate traffic routing but also enable covert data collection. Third-party VPN applications can monitor all network activity, access Windows Event Logs, and transmit data before encryption occurs. Unlike mobile platforms with stricter app sandboxing, Windows provides VPNs nearly unrestricted access to your digital footprint.
Identifying Untrustworthy VPN Providers

Red Flags in Privacy Policies
Examine privacy policies for vague language like “minimal logging” or “anonymous usage statistics.” Legitimate no-log VPNs specify exactly what they don’t collect. Warning signs include jurisdictions with mandatory data retention laws, the absence of independent audits, and ownership by data analytics companies. Cross-reference policy claims with third-party audits from firms like Deloitte or PwC.
Recent VPN Logging Scandals
Multiple providers have been exposed for false advertising. Some incidents involved VPNs storing unencrypted user credentials, selling bandwidth to third parties, and maintaining databases linking user accounts to specific websites. Court documents and server seizures revealed extensive logging despite explicit no-log marketing claims. These revelations highlight the gap between privacy promises and actual practices.
How to Verify VPN Logging on Windows 10/11
Step 1: Check Network Activity
Windows 10:
- Press Win + X and select “Task Manager”
- Click the “Performance” tab
- Select “Ethernet” or “Wi-Fi” from the left panel
- Click “Open Resource Monitor” at the bottom
- Navigate to the “Network” tab
- Monitor active connections while VPN is connected with no browsing
- Look for suspicious data transfers to unknown IP addresses
Windows 11:
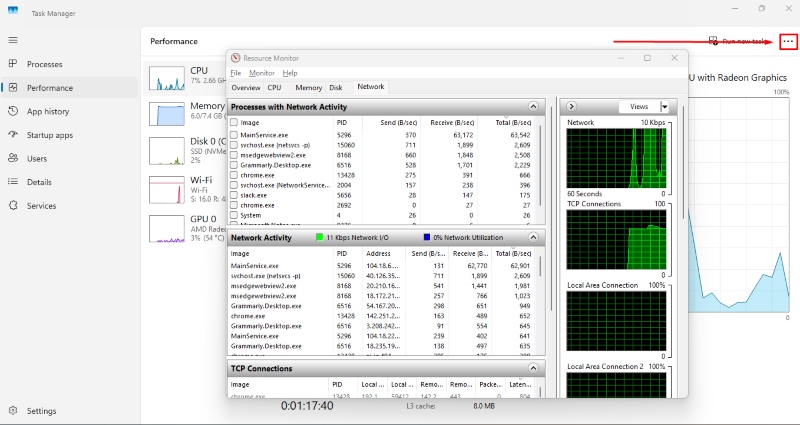
- Press Win + X and choose “Task Manager”
- Click the “Performance” section
- Select your active network adapter
- Click “Open Resource Monitor”
- Review the “Network Activity” list for your VPN process
- Identify any unexpected connections to servers beyond your chosen VPN location
Step 2: Analyze DNS Queries
- Press Win + R, type cmd, and press Enter
- Type ipconfig /displaydns and press Enter
- Review the DNS cache for entries your VPN shouldn’t be resolving
- Clear DNS cache with ipconfig /flushdns
- Connect to VPN and visit only one specific website
- Run ipconfig /displaydns again
- Check if the VPN is making additional DNS queries to analytics or tracking domains
Step 3: Monitor Outbound Connections
- Download Windows Firewall Control (free tool)
- Set filtering to “High” to block all unauthorized connections
- Manually allow only your VPN application
- Browse normally and note any blocked connection attempts from the VPN
- Investigate destination IP addresses using WHOIS lookup tools
- Legitimate VPNs only connect to their server network
Choosing a Verified No-Log VPN
Essential Features for Windows Users
Select VPNs with court-proven no-log policies, not just marketing claims. Prioritize providers that publish transparency reports, undergo annual independent audits, and operate in privacy-friendly jurisdictions. Essential technical features include RAM-only servers (data wiped on restart), built-in leak protection, and open-source clients that allow code verification.
Recommended Security Settings
Configure your VPN to use OpenVPN or WireGuard protocols for maximum transparency. Enable kill switch functionality to prevent unencrypted connections if the VPN drops. Disable features like “VPN accelerator” or “smart location” that may compromise privacy for convenience. Set DNS servers to your VPN provider’s rather than the automatic Windows defaults.
Protecting Yourself from VPN Data Collection
Use Fortect Premium for Comprehensive Protection
Fortect is a powerful and advanced anti-virus with real-time malware protection. It automatically scans your Windows PC for any threats, including malicious VPN applications and data logging spyware, then fixes them and optimizes your computer.
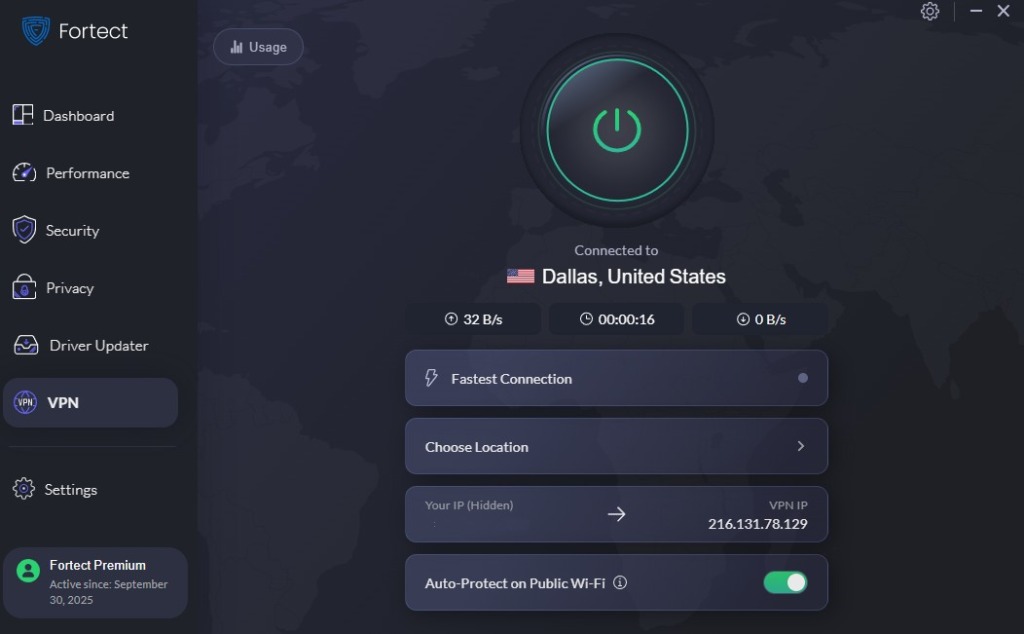
The new Fortect Premium now includes a built-in VPN with Auto-Protect, ensuring your connection stays secure even on public Wi-Fi networks. It encrypts your internet traffic to keep your data private and shield you from hackers who exploit unsecured connections, a common entry point for zero-day attacks and other network-based threats. Unlike standalone VPNs implicated in logging scandals, Fortect’s integrated solution provides verified protection with transparent security practices.
Download and install Fortect today!
Advanced Privacy Measures
Use multi-hop VPN connections that route traffic through multiple servers, making traffic correlation nearly impossible. Enable split tunneling only for non-sensitive applications. Regularly audit Windows Event Viewer for unusual VPN-related entries by searching for Event IDs 20227 and 20226. Consider running VPN software in a virtual machine for complete isolation from your primary Windows installation.
Regular Privacy Audits
Test for DNS leaks monthly using dedicated websites while connected to your VPN. Verify your IP address changes appropriately when switching VPN locations. Review VPN app permissions in Windows Settings under Privacy & Security. Uninstall VPN completely if switching providers, rather than leaving dormant applications with system access.
The Bottom Line
VPN data logging scandals prove that trust must be verified, not assumed. Windows users need proactive monitoring since the operating system grants VPNs extensive access. By following these verification steps and choosing audited providers, you can ensure your VPN protects rather than compromises your privacy. Remember: a VPN that logs your data offers no more protection than your ISP.