Protecting Your Windows System from Unauthorized Code Execution
Unauthorized code execution is one of the most dangerous threats facing Windows users today. It occurs when malicious software, scripts, or commands run on your system without your knowledge or approval. Once attackers gain this foothold, they can steal sensitive data, install malware, or even take full control of your PC.
While Windows includes built-in protections like Windows Defender and User Account Control (UAC), cybercriminals have become more advanced. Exploits on remote code execution vulnerabilities, malicious downloads, and unsafe email attachments are just some of the ways attackers slip through. If you handle financial transactions, store personal data, or use your PC for business purposes, you need strong defense measures beyond the basics.
What Is Unauthorized Code Execution?
Understanding the Threat
Unauthorized code execution is a broad term describing any situation where programs or scripts run without your consent. This can include:
- Malware infections from unsafe downloads.
- Exploitation of unpatched Windows vulnerabilities.
- Remote code execution (RCE) attacks which hackers inject code over the internet.
- Malicious macros or scripts hidden in email attachments.
Why It’s Dangerous
Even a single instance of unauthorized code execution can allow attackers to:
- Install spyware to monitor your keystrokes.
- Deploy ransomware to lock your files.
- Create backdoors for long-term system access.
- Steal login credentials, banking details, and personal information.
How Remote Code Execution Vulnerabilities Work
Remote Code Execution Vulnerabilities (RCEs) are specific flaws in Windows or installed applications that let attackers run malicious code from afar, often without you clicking anything. Cybercriminals exploit these vulnerabilities through unpatched software, malicious websites, or compromised network traffic. Once exploited, an attacker can gain the same privileges as the current user, which is especially dangerous if the account has administrator rights. This is why patching Windows and restricting account privileges are critical for protection.
How to Protect Your Windows System
Keep Windows Updated
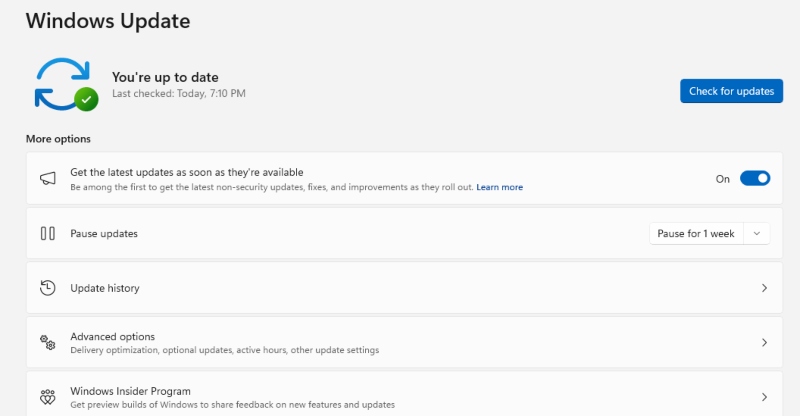
Microsoft regularly releases patches to close security loopholes. To update your system:
- Click Start > Settings > Update & Security.
- Select Windows Update.
- Click Check for updates.
- Download and install all available updates, then restart your PC.
Restrict User Accounts
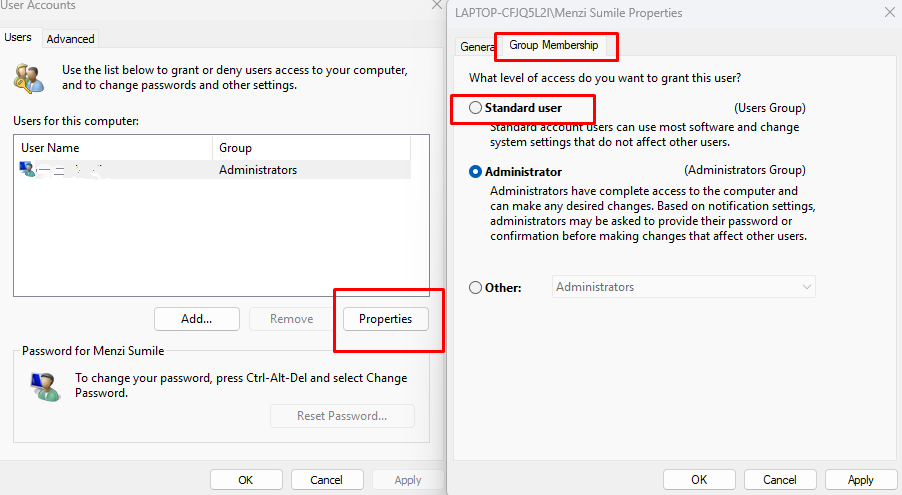
Limiting privileges helps reduce the risk of unauthorized execution.
- Go to Settings > Accounts > Family & other users.
- Select the account you want to change.
- Click Change account type.
- Switch from Administrator to Standard User when possible.
Enable Controlled Folder Access
This feature blocks suspicious apps from making unwanted changes.
- Open Windows Security from the Start menu.
- Go to Virus & threat protection > Manage ransomware protection.
- Toggle Controlled folder access to On.
Practice Safer Browsing
- Avoid clicking on suspicious email links.
- Download software only from trusted sources.
- Use two-factor authentication for accounts.
- Refrain from connecting to public wifi.
Fortect – Real-Time Protection Against Unauthorized Code Execution
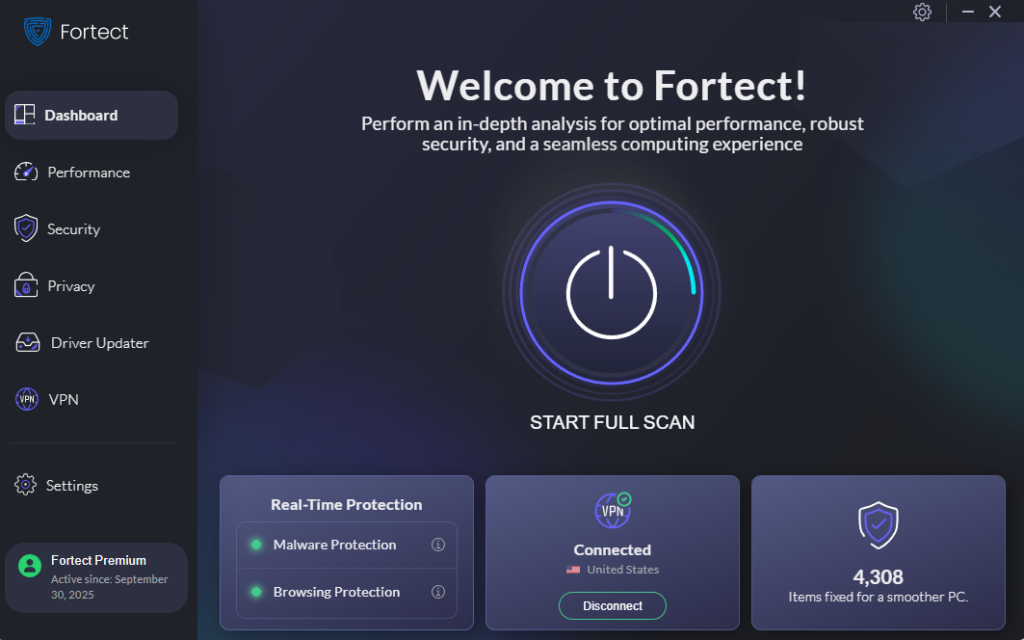
Windows Defender can stop many common threats, but advanced malware and unauthorized execution often slip past. That’s where Fortect comes in. Fortect is a powerful antivirus software with real-time malware protection. It automatically scans your Windows PC for threats such as unauthorized code execution, trojans, ransomware, and spyware. Once detected, it removes the infection, repairs damaged system files, and optimizes your computer for smoother performance.
Download and install Fortect today.
Conclusion
Unauthorized code execution is a serious risk that can compromise your entire Windows system. While built-in tools provide a layer of defense, advanced threats often exploit weaknesses such as remote code execution vulnerabilities, making stronger protection essential. By keeping Windows updated, restricting account privileges, enabling ransomware protection, and practicing good online habits, you significantly reduce your exposure. For full protection against evolving threats, pairing these steps with real-time solutions like Fortect ensures your system stays safe, optimized, and resilient against attacks.



![What Causes Windows Update Failure [How To Prevent It]](https://wp-cdn.fortect.com/uploads/2023/04/12103355/windows-update-failed-2-425x300.jpg)