Evil Twin Phishing: Detection and Prevention
You’re sitting at your favorite coffee shop, scrolling through social media on your laptop. You connect to what appears to be the café’s Wi-Fi network, and everything seems normal, until your bank account gets compromised. Welcome to the world of evil twin phishing, one of the most deceptive cyber threats facing everyday internet users.
What Is Evil Twin Phishing?
Evil twin phishing is a cyberattack where hackers create a fake Wi-Fi network that mimics a legitimate one. These fraudulent networks have names nearly identical to trusted hotspots, tricking you into connecting. Once connected, cybercriminals can intercept your data, steal passwords, capture credit card information, and monitor your online activity without your knowledge.
Unlike traditional phishing emails, evil twin attacks exploit your trust in public Wi-Fi networks. The fake access point acts as a “man-in-the-middle,” sitting between you and the internet, recording everything you transmit.
How Evil Twin Attacks Work
Attackers use portable devices and readily available software to broadcast a wireless network signal. They often position themselves near popular public locations like airports, hotels, libraries, or restaurants. The rogue access point typically uses the same name (SSID) as the legitimate network, sometimes with a stronger signal strength to ensure your device connects to theirs first.
Recognizing Evil Twin Wi-Fi Networks
Warning Signs to Watch For
Spotting an evil twin network requires vigilance. Look for these red flags:
Duplicate network names: Multiple networks with identical or very similar names appearing in your Wi-Fi list often indicate an evil twin attack. Legitimate businesses rarely broadcast multiple networks with the same SSID.
No password requirement: Cybercriminals frequently set up open networks without encryption to make connecting easier and faster for unsuspecting victims.
Unusual connection behavior: If you’re suddenly disconnected from a trusted network and reconnected to what appears to be the same one, this could signal an evil twin takeover.
Security certificate warnings: Browser alerts about invalid security certificates or HTTPS errors when visiting familiar websites suggest someone is intercepting your connection.
Weaker encryption: Networks using outdated WEP security or no encryption at all pose serious risks compared to modern WPA2 or WPA3 standards.
Protecting Yourself on Windows 10/11
Configure Your Wi-Fi Settings for Maximum Security
Step 1: Click the Start menu and select “Settings” (gear icon)
Step 2: Navigate to “Network & Internet” and click “Wi-Fi” in the left sidebar
Step 3: Toggle off “Connect to suggested open hotspots” and “Connect to networks shared by my contacts”
Step 4: Under “Manage known networks,” review your saved networks and remove any you don’t recognize or no longer use
Step 5: Enable “Random hardware addresses” for each network to prevent tracking across different Wi-Fi connections
Enable Windows Firewall Protection
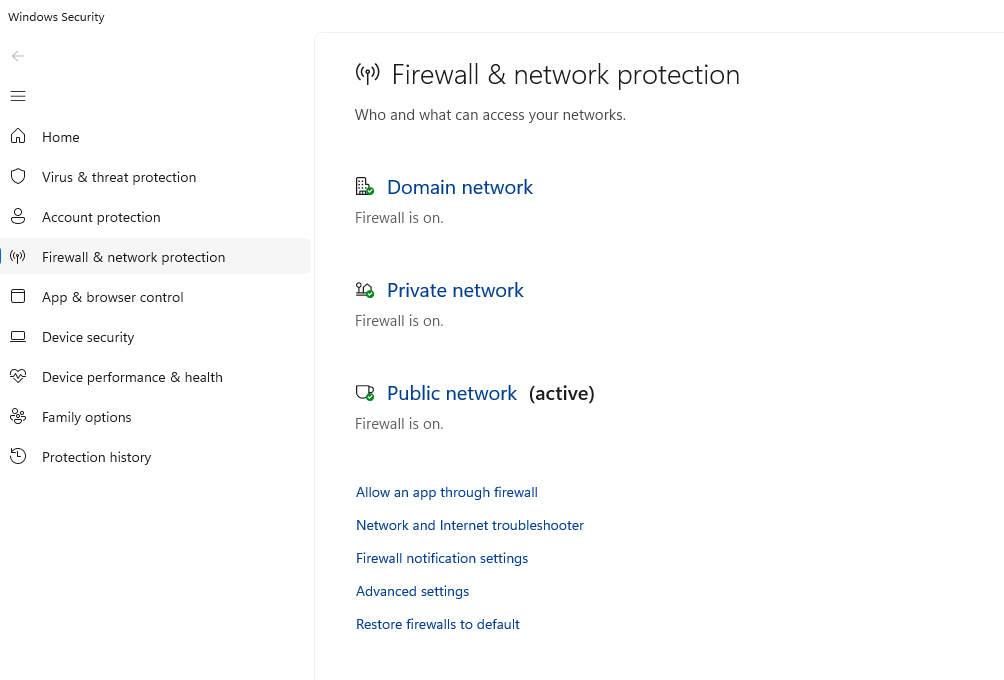
Step 1: Open Settings and go to “Privacy & Security”
Step 2: Click “Windows Security” and select “Firewall & network protection”
Step 3: Ensure the firewall is turned on for all three network types: Domain, Private, and Public
Step 4: Click “Public network” and verify “Windows Defender Firewall” is switched on. This is crucial when connecting to any public Wi-Fi
Keep Windows Updated Against Threats
Step 1: Press Windows key + I to open Settings
Step 2: Click “Windows Update” in the left panel
Step 3: Select “Check for updates” and install any available updates
Step 4: Click “Advanced options” and enable “Receive updates for other Microsoft products”
Step 5: Turn on “Download updates over metered connections” if you want protection even when using mobile hotspots
Essential Prevention Strategies
Strengthen Your Defense with Fortect
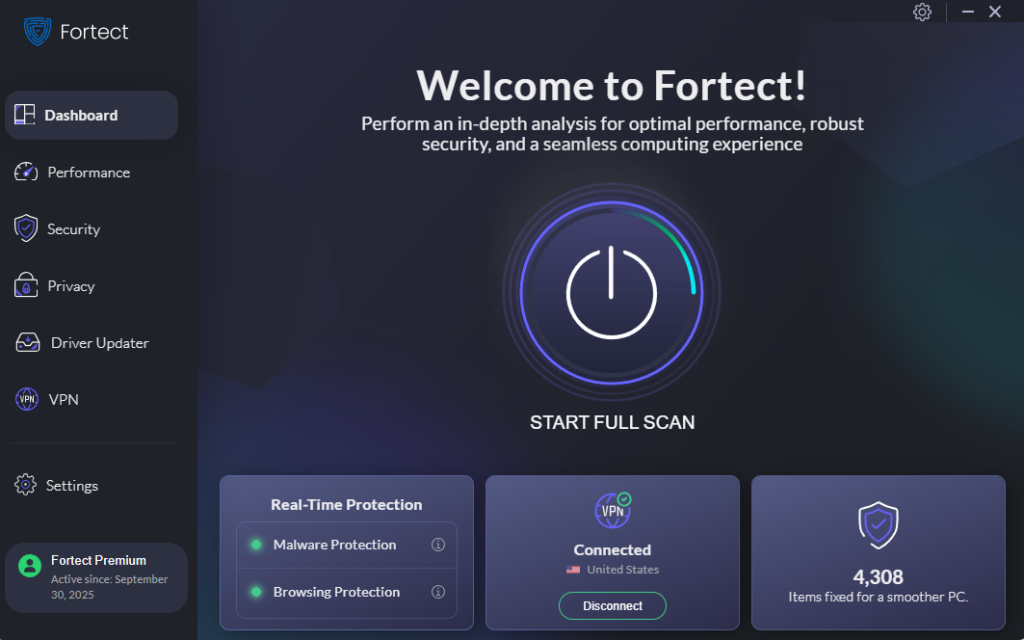
Fortect is a powerful and advanced anti-virus solution with real-time malware protection designed to safeguard Windows users against evil twin phishing and other cyber threats. This comprehensive security tool automatically scans your Windows PC for any threats, including malicious software that attackers may install through compromised Wi-Fi networks, then fixes them while optimizing your computer’s performance.
Beyond malware detection, Fortect Premium includes a built-in Driver Updater that plays a crucial role in defending against evil twin attacks. When you connect to a malicious Wi-Fi network, attackers often target vulnerabilities in outdated network and wireless drivers to gain deeper access to your system. These compromised drivers can allow cybercriminals to maintain persistent access even after you disconnect from the rogue network.
Fortect automatically identifies and updates these vulnerable drivers from trusted sources, eliminating backdoor entry points that evil twin attackers might exploit. With updated drivers, your wireless adapter and network components become more resistant to man-in-the-middle attacks, while your entire system benefits from improved stability and optimized performance that keeps you safer online.
Download and install Fortect today!
Use a Virtual Private Network (VPN)
A VPN encrypts all your internet traffic, making it unreadable even if attackers intercept it through an evil twin network. This creates a secure tunnel between your device and the internet, rendering evil twin attacks largely ineffective.
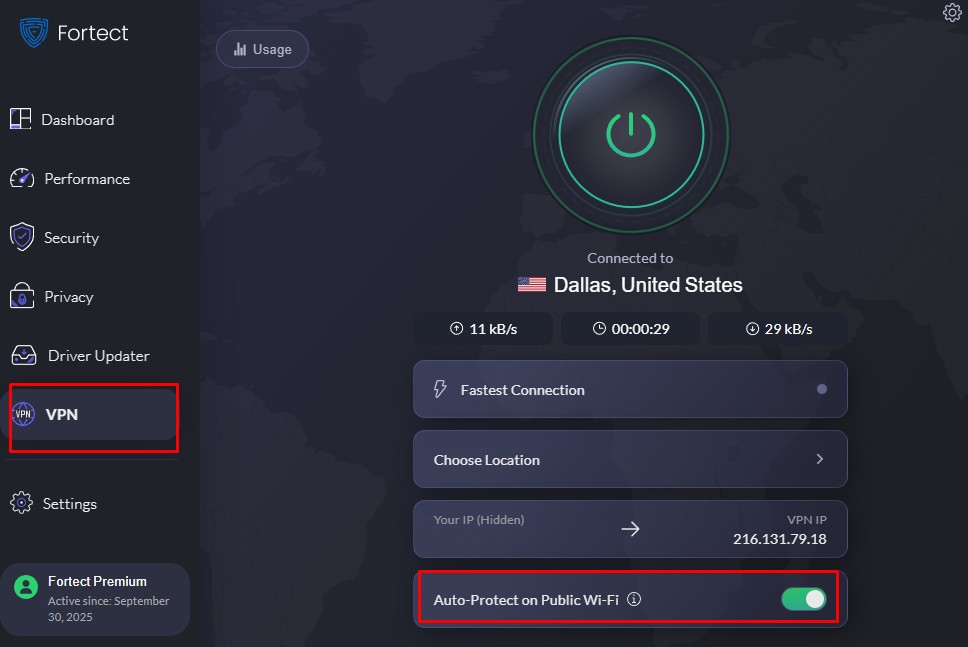
Fortect Premium also includes a built-in VPN feature with auto-protect on public wifi that encrypts your internet connection, making your data unreadable even if intercepted through an evil twin network. This VPN protection keeps your online activity private and secure anywhere in the world, providing comprehensive defense as part of Fortect’s complete system security solution.
Verify Networks Before Connecting
Always confirm the official network name with staff before connecting at hotels, cafés, or public venues. Ask about the exact spelling, including capital letters and spaces, as attackers often create near-identical names with subtle differences.
Disable Auto-Connect Features
Turn off automatic connection to Wi-Fi networks in your Windows settings. This prevents your device from unknowingly connecting to malicious networks that match saved network names.
Stick to HTTPS Websites
Only visit websites with HTTPS in the URL and a padlock icon in the address bar. While not foolproof, this adds an encryption layer that makes data interception more difficult for attackers.
Use Mobile Data for Sensitive Transactions
When handling banking, shopping, or other sensitive activities, switch to your phone’s mobile data connection instead of public Wi-Fi. The cellular network provides better security against evil twin attacks.
Stay One Step Ahead
Evil twin phishing represents a real and growing threat to your personal information and online security. By understanding how these attacks work, recognizing warning signs, and implementing the Windows security configurations outlined above, you can significantly reduce your risk of exposure. Remember: convenience should never come at the cost of security. When in doubt about a Wi-Fi network’s authenticity, it’s always safer to use your mobile data or wait until you’re connected to a trusted network.



