2025 Guide: Protect Your PC from Cyborg Ransomware
Cyborg ransomware encrypts your files and demands payment for their release. This malware primarily spreads through phishing emails disguised as Windows updates and can devastate your system in minutes. Here’s how to protect your PC and remove infections.
What Is Cyborg Ransomware?
Cyborg ransomware is file-encrypting malware that locks documents, photos, videos, and databases, making them completely inaccessible. Attackers demand cryptocurrency payments to restore access, but payment doesn’t guarantee file recovery.
How Cyborg Ransomware Infects Your Computer
Fake Windows Update Emails: The most common method involves spam emails impersonating Microsoft, urging you to download “critical security updates” that are actually ransomware executables.
Phishing Attachments: Fraudulent emails from fake banks, shipping companies, or government agencies contain malicious attachments that install ransomware when opened.
Compromised Websites: Visiting infected websites can trigger automatic downloads without your knowledge.
Outdated Software: Unpatched vulnerabilities in Windows and applications provide easy entry points for attackers.
Warning Signs of Infection
- Files suddenly become inaccessible with changed extensions
- A ransom note appears demanding payment
- Severe performance slowdown
- Unknown processes in Task Manager
- Unusual network connections
How to Remove Cyborg Ransomware from Windows 10/11
Step 1: Disconnect from the Internet
Windows 10: Click the Network icon in the system tray > Click your connection > Select “Disconnect”
Windows 11: Click Network in Quick Settings > Toggle off your Wi-Fi/Ethernet connection
Step 2: Boot into Safe Mode with Networking
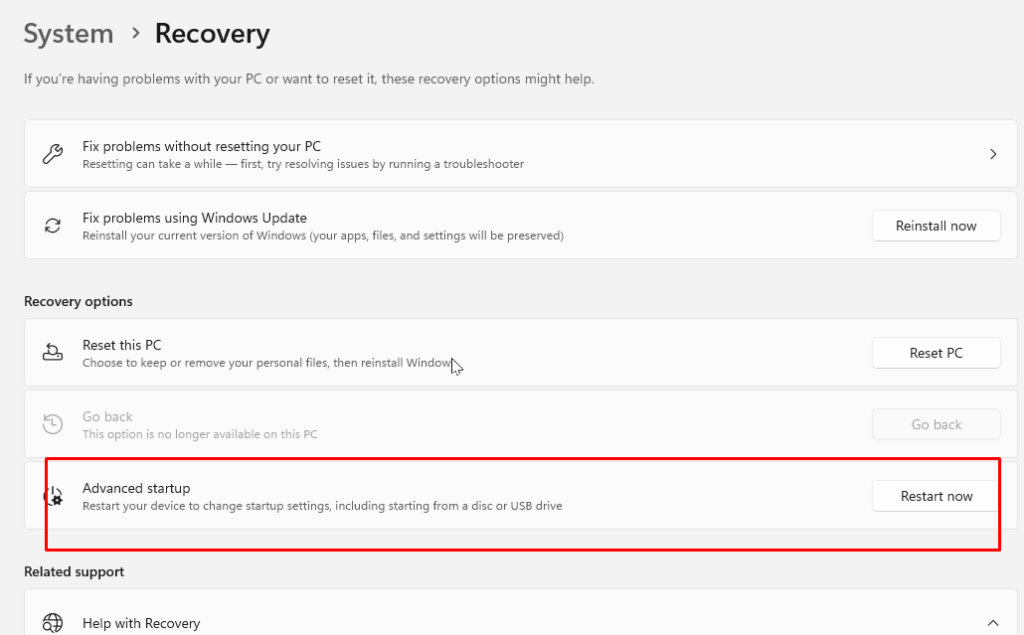
Windows 10:
- Press Windows + I > Update & Security > Recovery or System > Recovery > Advanced startup
- Under “Advanced startup,” click “Restart now”
- Select Troubleshoot > Advanced options > Startup Settings > Restart
- Press 5 or F5 for Safe Mode with Networking
Windows 11:
- Press Windows + I > System > Recovery
- Next to “Advanced startup,” click “Restart now” > Restart now again
- Select Troubleshoot > Advanced options > Startup Settings > Restart
- Press 5 or F5 for Safe Mode with Networking
Step 3: Run a Full System Scan
- Press Windows + I > Privacy & Security > Windows Security (Win 11) or Update & Security > Windows Security (Win 10)
- Click “Virus & threat protection” > “Scan options”
- Select “Full scan” > Click “Scan now”
- Quarantine or remove detected threats
Step 4: Use Decryption Tools
Download the free Emsisoft Decryptor for STOP Djvu from the official Emsisoft website, run as Administrator, and follow instructions to attempt file recovery.
Step 5: Protect Your PC from Cyborg Ransomware with Automated Security
Fortect provides powerful, real-time protection against Cyborg ransomware and other malware threats. This advanced antivirus automatically detects and removes infections while optimizing your system performance. Fortect Premium includes a smart driver updater that replaces corrupted and outdated drivers from verified sources, eliminating vulnerabilities that ransomware exploits to infiltrate your system.
Key benefits:
- Real-time scanning prevents ransomware before encryption
- Automatic threat removal and system repair
- Driver maintenance closes security vulnerabilities
- Complete system optimization improves performance
Download and install Fortect today.
Cyborg Ransomware Prevention
1. Update Windows to Patch Security Vulnerabilities
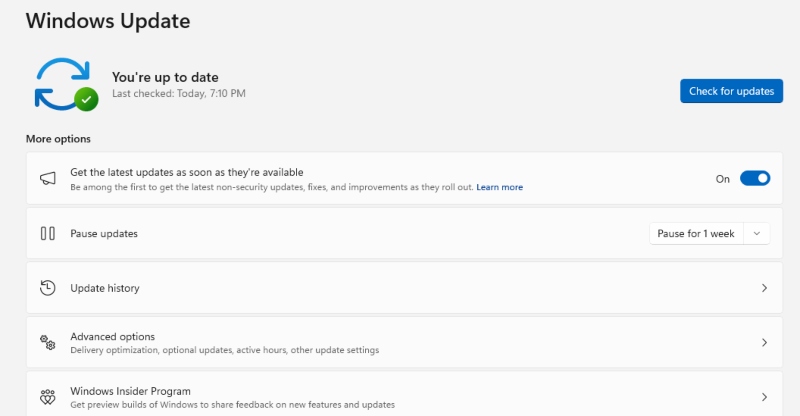
Windows 10:
- Press Windows + I > Update & Security > Windows Update
- Click “Check for updates” > Download and install available updates
- Go to “Advanced options” > Enable “Receive updates for other Microsoft products”
- Restart when prompted
Windows 11:
- Press Windows + I > Windows Update
- Click “Check for updates”
- Go to “Advanced options” > Enable “Get the latest updates as soon as they’re available”
- Restart to apply updates
2. Create Regular Backups
Using File History:
Windows 10:
- Connect external hard drive
- Press Windows + I > Update & Security > Backup
- Click “Add a drive” > Select your drive
- Toggle “Automatically back up my files” to On
- Click “More options” > Set frequency to “Every hour”
Windows 11:
- Connect external drive
- Press Windows + I > System > Storage > Advanced storage settings
- Select “Backup options” > “Add a drive” > Choose drive
- Click “More options” to set hourly backups
Critical: Store backup drives disconnected from your PC when not backing up. Never keep your only backup permanently connected.
3. Enable Windows Defender Real-Time Protection
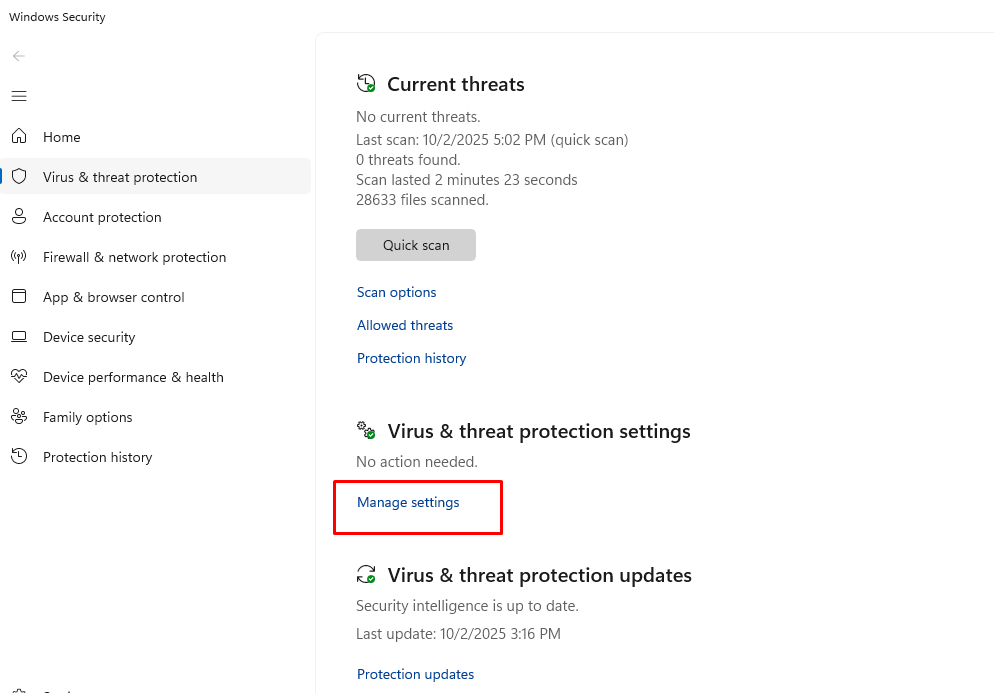
Windows 10:
- Press Windows + I > Update & Security > Windows Security
- Click “Virus & threat protection” > “Manage settings”
- Enable “Real-time protection,” “Cloud-delivered protection,” and “Automatic sample submission”
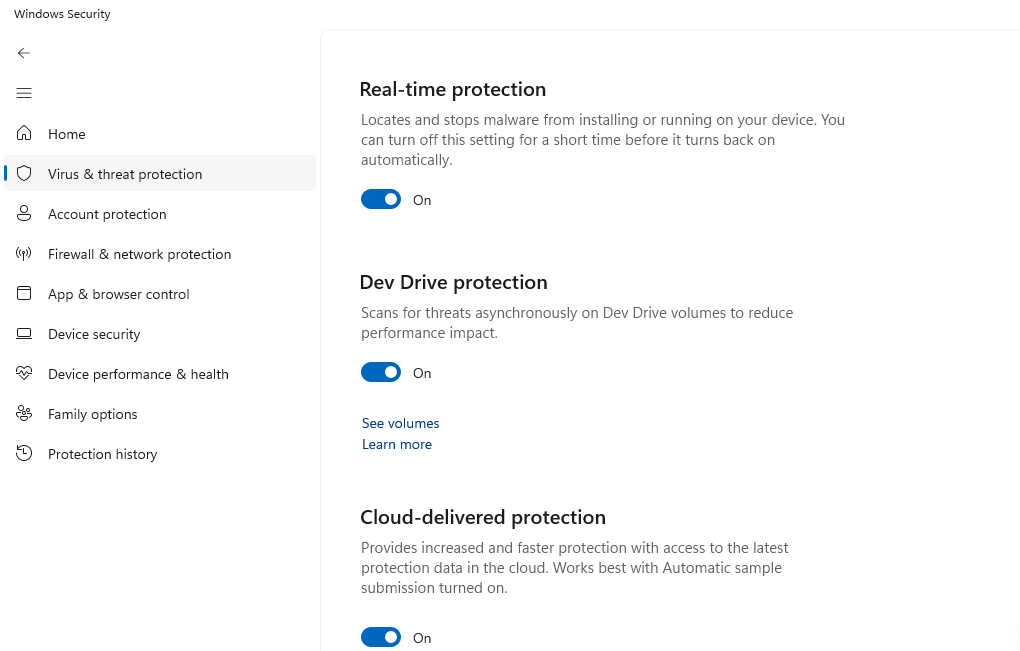
Windows 11:
- Press Windows + I > Privacy & security > Windows Security
- Click “Virus & threat protection” > “Manage settings”
- Enable all three protection options
4. Restrict User Account Permissions
Windows 10:
- Press Windows + I > Accounts > Family & other users
- Click “Add someone else to this PC” to create standard (non-admin) accounts
- For existing accounts: Click account name > “Change account type” > Select “Standard User”
Windows 11:
- Press Windows + I > Accounts > Other users
- Click “Add account” to create standard user accounts
- Modify existing accounts by clicking name > “Change account type” > “Standard User”
5. Configure Windows Firewall
Enable Firewall:
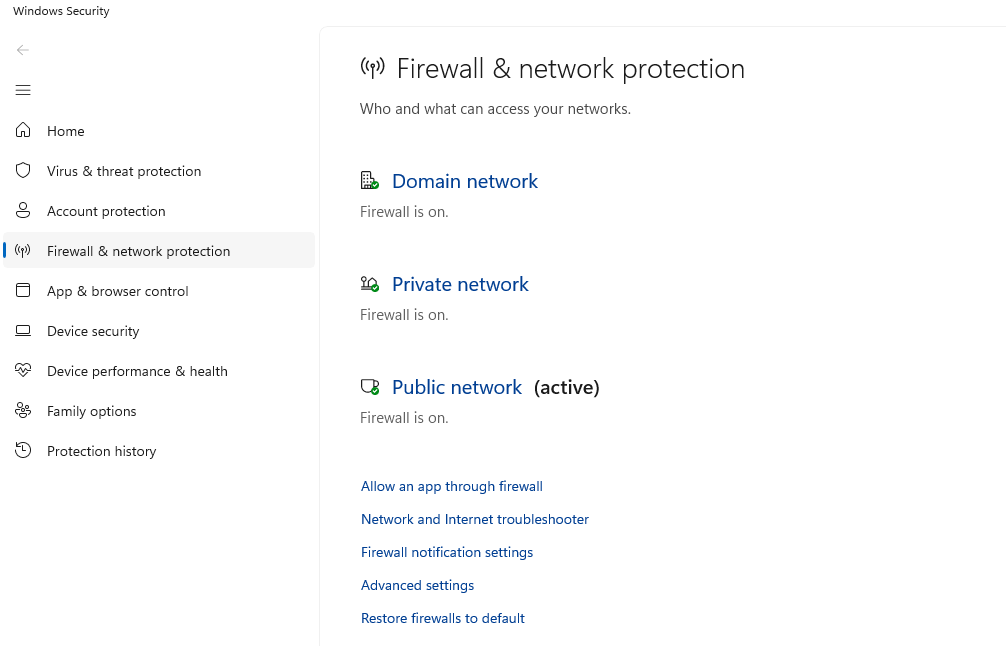
Windows 10: Settings > Update & Security > Windows Security > Firewall & network protection > Enable for all networks
Windows 11: Settings > Privacy & security > Windows Security > Firewall & network protection > Enable for all networks
Advanced Settings:
- Press Windows + R, type wf.msc, and press Enter
- Click “Windows Defender Firewall Properties”
- Set “Firewall state” to On for Domain, Private, and Public profiles
- Set “Inbound connections” to Block
- Click “Apply”
6. Identify Phishing Emails

Red flags:
- Generic greetings (“Dear Customer”)
- Urgent threats or deadlines
- Unexpected attachments (.exe, .zip, .scr files)
- Suspicious sender addresses (hover to reveal actual email)
- Poor grammar and spelling
- Requests for passwords or personal information
Safe practices:
- Never open attachments from unknown senders
- Don’t click links in unsolicited emails
- Verify the sender by contacting the organization directly
- Delete suspicious emails immediately
7. Enable Controlled Folder Access (Ransomware Protection)
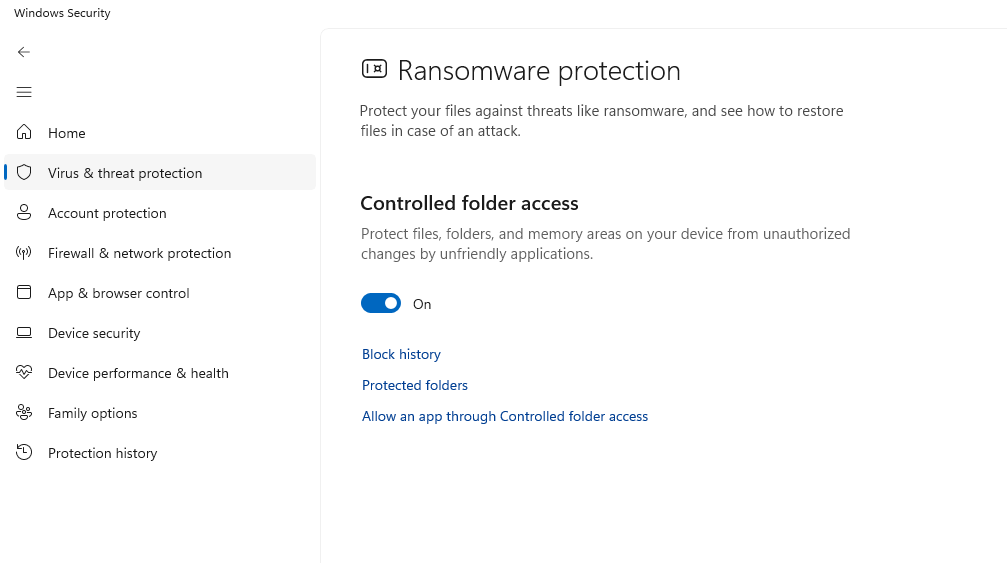
Windows 10/11:
- Open Windows Security > Virus & threat protection
- Click “Manage ransomware protection”
- Toggle “Controlled folder access” to On
- Add protected folders as needed
- Whitelist trusted applications through “Allow an app through Controlled folder access”
What to Do If Infected by Cyborg Ransomware?
- Don’t pay the ransom – Payment doesn’t guarantee recovery
- Disconnect immediately – Remove network cables and disable Wi-Fi
- Report to authorities – File report at IC3.gov
- Check for decryptors – Visit nomoreransom.org and Emsisoft
- Restore from backups – Use offline backups after confirming malware removal
- Change all passwords after completing system cleaning
Conclusion
Protecting against Cyborg ransomware requires layered security: keep Windows updated, maintain disconnected backups, enable Windows Defender and firewall, use standard user accounts for daily work, and stay vigilant against phishing emails. Prevention is far easier than recovery; implement these measures today to safeguard your data.