Whale Phishing Attacks: Definition and Prevention for Windows Users
Cybercriminals are getting smarter, and their attacks are more targeted. While you’ve probably heard about phishing emails, there’s a more dangerous variant called whale phishing that specifically targets high-value individuals. If you’re a Windows user with access to sensitive information or financial accounts, understanding whale phishing could save you from devastating losses.
What Is Whale Phishing?
Whale phishing, also known as whaling attacks, is a highly targeted form of spear phishing that focuses on high-value individuals with access to sensitive information or significant financial accounts. Unlike standard phishing attacks that cast a wide net, whale phishing attacks are carefully crafted to deceive specific “big fish.”
How Whale Phishing Differs from Regular Phishing
Regular phishing emails are generic messages sent to thousands of people, often with obvious red flags. Whale phishing attacks are different. Attackers spend time researching their targets through social media, professional networks, and public records. They craft personalized messages that appear legitimate, often impersonating trusted contacts, service providers, or financial institutions.
These sophisticated scams might reference your recent activities or arrive at times when you’re likely to act quickly without scrutinizing details.
Common Whale Phishing Tactics Targeting Windows Users
Email Spoofing and Impersonation
Cybercriminals create emails that look identical to legitimate correspondence. They might impersonate your bank, a service provider, or even a family member. The email address may differ by just one character, making it nearly impossible to spot at first glance.
Malicious Attachments and Links
Whale phishing emails often contain infected Word documents, PDFs, or Excel files designed to exploit Windows vulnerabilities. Some links direct you to fake login pages that steal your credentials, while others download malware directly onto your computer.
Urgent Requests and Social Engineering
Attackers create artificial urgency to bypass your critical thinking. Common scenarios include tax emergencies, account suspensions, urgent payment requests, or security alerts requiring immediate action.
How to Protect Yourself from Whale Phishing on Windows
Keep Your Windows System Updated
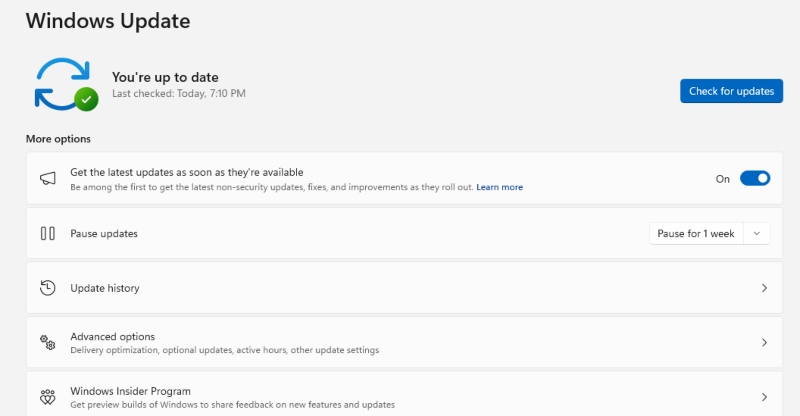
Regular updates patch security vulnerabilities that attackers exploit. Here’s how to ensure your Windows 10/11 stays protected:
For Windows 10:
- Click the Start button and select “Settings” (gear icon)
- Click “Update & Security”
- Select “Windows Update” from the left panel
- Click “Check for updates”
- Install any available updates and restart if prompted
For Windows 11:
- Click the Start button and select “Settings”
- Click “Windows Update” in the left sidebar
- Click “Check for updates”
- Allow all updates to download and install
- Restart your computer to complete the installation
Enable automatic updates to ensure you’re always protected without manual intervention.
Enable Windows Defender and Email Filtering
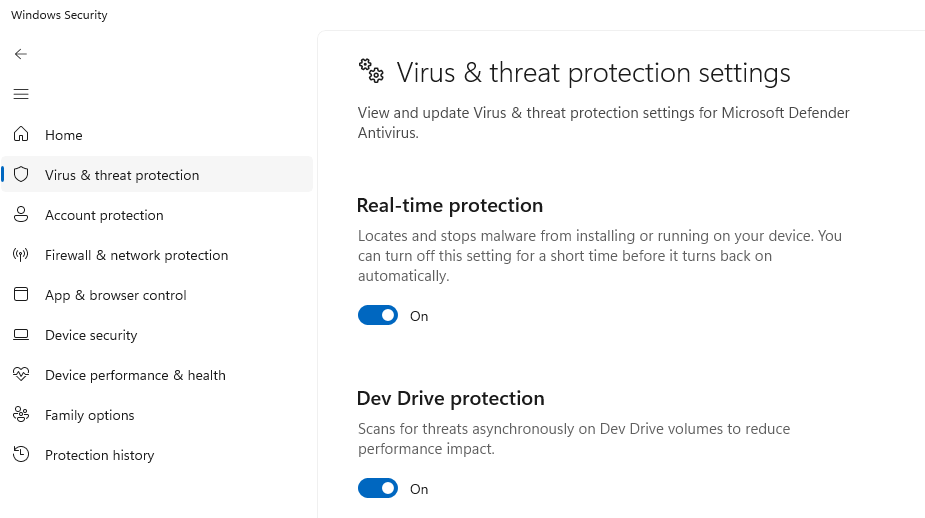
Windows Defender provides robust protection against malware delivered through whale phishing attempts. Ensure it’s active:
- Open Windows Security by searching for it in the Start menu
- Click “Virus & threat protection”
- Verify that “Real-time protection” is turned ON
- Enable “Cloud-delivered protection” for enhanced threat detection
- Turn on “Automatic sample submission” to help Microsoft identify new threats
Configure your email client to filter suspicious messages. Most email providers offer spam filtering and phishing protection that can catch fraudulent messages before they reach your inbox.
Verify Before You Act
Never click links or download attachments from unexpected emails, even if they appear to come from someone you know. Instead:
- Hover over links to preview the actual URL before clicking
- Contact the sender through a different communication channel to verify legitimacy
- Check email headers for discrepancies in sender information
- Look for slight misspellings in email addresses or domain names
Use Multi-Factor Authentication (MFA)
Enable MFA on all important accounts, especially email, banking, and social media. Even if attackers steal your password through a whale phishing attack, they won’t be able to access your accounts without the second authentication factor.
Be Skeptical of Urgent Requests
Legitimate organizations rarely demand immediate action through email alone. If an email creates panic or pressure, take a step back. Verify through official channels before responding to requests involving money, sensitive information, or credential changes.
Strengthen Your Defense with Fortect
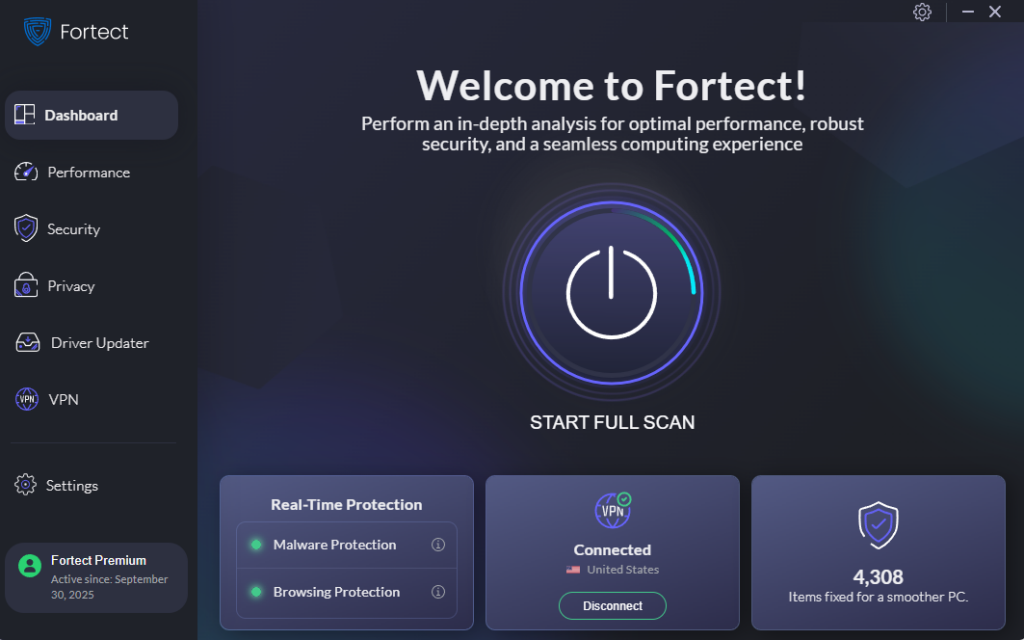
For comprehensive protection against whale phishing and other advanced threats, consider using Fortect, a powerful and advanced anti-virus solution with real-time malware protection. Fortect automatically scans your Windows PC for any threats, including those delivered through whale phishing attacks, then fixes them and optimizes your computer for peak performance.
Fortect Premium comes with a built-in Driver Updater that automatically scans your Windows PC for outdated or corrupted drivers and updates them safely from trusted sources. Corrupted or outdated drivers are more than just a performance issue; hackers can exploit them to inject malware into your system. Because drivers communicate directly with the system kernel, any compromise can lead to serious instability or even a complete system takeover.
By keeping your drivers updated, Fortect not only closes these security gaps but also ensures your PC runs smoothly. Once the updates are applied, your computer is optimized for cleaner, faster, and more reliable performance.
Download Fortect today and experience world-class security.
Recognizing Whale Phishing Red Flags
Stay alert for these warning signs:
- Generic greetings despite supposedly knowing you personally
- Requests for passwords, social security numbers, or financial information
- Unusual sender email addresses or domains
- Poor grammar or formatting inconsistencies
- Mismatched URLs when hovering over links
- Unsolicited attachments, especially executable files
What to Do If You’ve Been Targeted
If you suspect you’ve received a whale phishing attempt, don’t panic. Delete the email immediately without clicking anything. If you accidentally clicked a link or downloaded an attachment, disconnect from the internet, run a full Windows Defender scan, and change passwords for important accounts from a different device.
Report suspicious emails to your email provider and consider notifying relevant authorities if sensitive information was compromised.
Stay Vigilant, Stay Safe
Whale phishing attacks exploit human psychology more than technical vulnerabilities. By staying informed, maintaining updated security measures on your Windows device, and approaching unexpected communications with healthy skepticism, you can protect yourself from these sophisticated threats. Remember: when something feels off, trust your instincts and verify before taking action.




