Managing Quarantine and Viewing Security Reports with Fortect
The Quarantine List and Security Reports features within the Fortect Security Center empower users to efficiently manage suspicious files and gain insights into their security status. This article delves into these essential features, guiding you on how to effectively utilize them to enhance your digital protection.
Quarantine List: Managing Isolated Threats
Fortect’s Quarantine List is a secure holding area for suspicious files, acting as a buffer between potential threats and your system’s integrity. Understanding the need to manage these quarantined items effectively.

To review and manage files that have been quarantined by Fortect:
- Navigate to Dashboard > Security
- Click View Quarantine List
- Select the desired action on the button at the button of the page.
Quarantine actions:
- Delete Selected Items – This action will delete the files from the computer completely.
- Exclude and Restore Selected – This option will add the selected files to exception list and will restore them to the original location.
- Restore Selected Items – This option will restore the files to the original location, but they will be detected again.

Security Reports
Fortect’s Security Reports are dedicated to showcasing the vigilance and effectiveness of your security measures. These reports provide an overview of all protection activities, including detected threats, blocked attacks, and security scans.
To view your security reports:
- Navigate to Settings > Security > View Security Reports

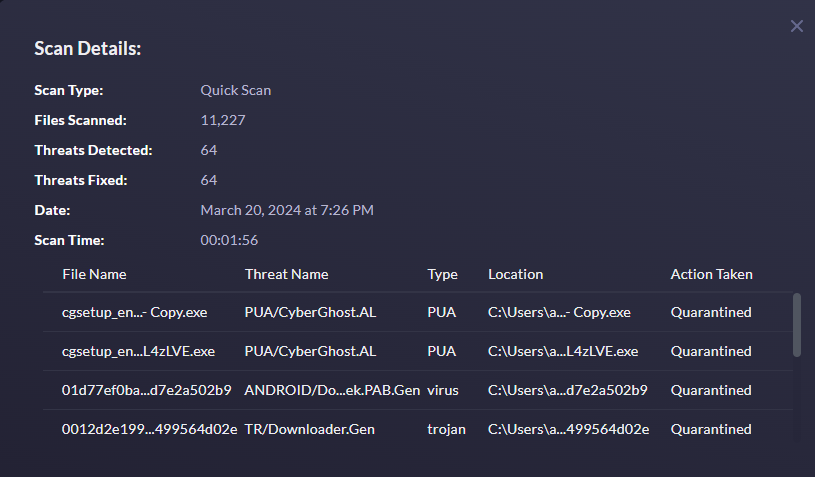
To view the full scan report:
- Navigate to Settings > Security > View Security Reports
- Click View Report
- You can now review the full details of the scan
Real-Time Security Reports
Explore comprehensive insights into your system’s defenses with Fortect. These reports are dedicated to showcasing the vigilance and effectiveness of your security measures.
- Real-Time Protection Report – This report shows your real-time defense log, tracking Fortect’s continuous protection against threats.

- Browsing Shield – This is a crucial feature that ensures safe internet usage by blocking access to malicious websites. This report provides detailed insights into the URLs that were blocked, the specific actions taken to neutralize potential threats, and other pertinent details.

Effectively managing isolated threats and understanding your security status are critical components of maintaining robust digital protection. Fortect’s Quarantine List and Security Reports offer comprehensive tools to handle suspicious files and gain valuable insights into your security measures.
By utilizing these features within the Fortect, you can enhance your system’s defense and ensure a secure digital environment. For additional support, please contact our customer service team at [email protected].
