Understanding Data Exfiltration and Ways to Prevent It
Data exfiltration is one of the most dangerous cyber threats facing Windows users today. Whether it’s through phishing attacks, malware, or insider threats, unauthorized data transfers can lead to serious consequences—including identity theft, corporate espionage, and legal repercussions.
We will break down data exfiltration, how it works, and the most effective strategies to prevent it—especially for users running Windows 10.
What Is Data Exfiltration?

Data exfiltration, also known as data theft or data extrusion, is the unauthorized transfer of data from a computer or network. It’s typically carried out by malicious actors who gain access to sensitive information and send it to an external destination—often without the user noticing.
While a data leak occurs when sensitive information is accidentally exposed—often due to misconfigurations, weak security settings, or human error—data exfiltration is a very different threat.
How Data Exfiltration Happens
- Phishing attacks trick users into providing access credentials.
- Malware infections quietly collect and send data to attackers.
- Remote access tools can be abused to export files undetected.
- USB devices or storage used by insiders to copy sensitive files.
- Compromised software may serve as a backdoor for data leaks.
Common Targets of Data Theft
- Financial records
- Personal identity data
- Customer databases
- Intellectual property
- Login credentials
How to Prevent Data Exfiltration on Windows 10
Protecting your system involves a layered approach. Below are practical, actionable steps to secure your Windows 10 PC.
1. Keep Your Windows Updated
Microsoft regularly releases security patches to fix known vulnerabilities. Keeping Windows 10 up-to-date is a critical first step.
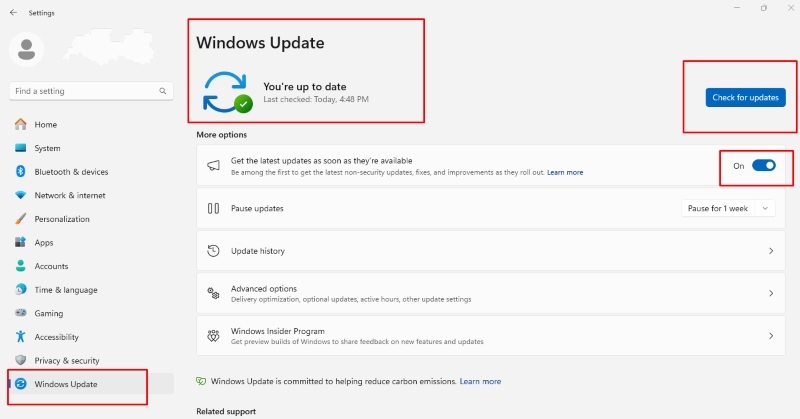
How to Update Windows 10:
- Press Windows + I to open Settings
- Click on Update & Security
- Select Windows Update
- Click Check for updates
- Install available updates and restart if prompted
2. Restrict User Permissions
Limit account privileges to reduce the risk of internal data leaks or compromised accounts.
How to Create a Standard Account:
- Open Settings > Accounts > Family & other users
- Click Add someone else to this PC
- Follow the prompts to add the user
- Select the user, click Change account type
- Set it to Standard User
3. Monitor Network Activity
Unexpected data transfers can indicate exfiltration in progress. Tools like Wireshark, GlassWire, or Windows Resource Monitor help you track outgoing traffic.
How to Use Windows Resource Monitor:
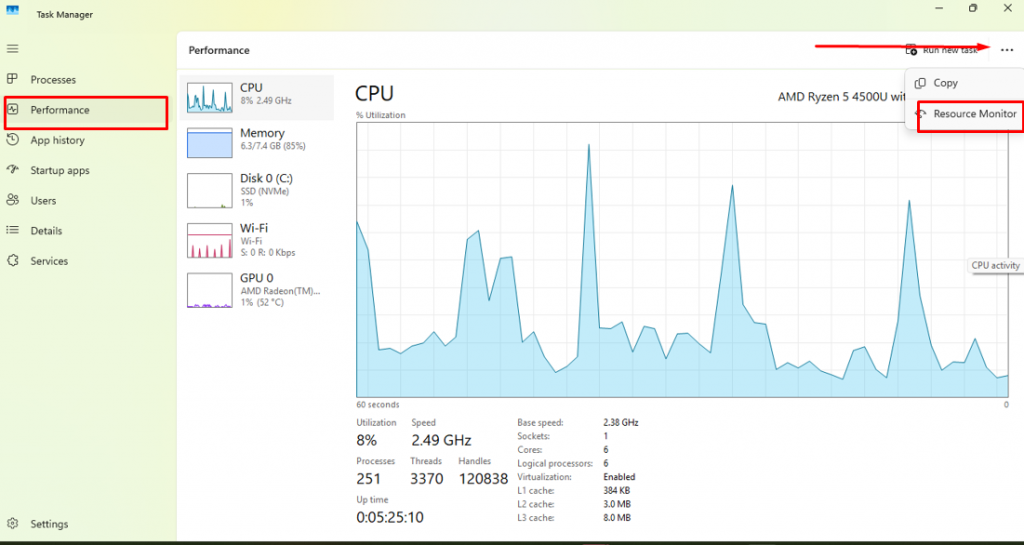
- Press Ctrl + Shift + Esc to open Task Manager
- Go to Performance > Open Resource Monitor
- Click the Network tab
- Check the Processes with Network Activity and Network Activity sections
4. Enable Windows Defender Firewall and Antivirus
Windows Defender offers decent built-in protection. Ensure both antivirus and firewall are enabled.
How to Turn It On:
- Open Settings > Update & Security
- Click Windows Security > Firewall & network protection
- Choose your network profile
- Ensure Microsoft Defender Firewall is turned ON
5. Use Real-Time Malware Protection (Advanced Prevention)
Some threats, especially the modern and new ones bypass default protections. In those cases, a third-party tool with advanced malware detection is your best bet.
Fortect is an all-in-one PC repair tool that includes real-time malware protection, specifically designed to detect and prevent sophisticated data exfiltration attacks. It scans your system for active and hidden threats—even the complex or newly developed ones that traditional tools might miss.
Pro tip: Run a full system scan with Fortect to identify and block malicious software before it starts leaking data.
Download and install Fortect today.
BYOD (Bring Your Own Device)
When employees or household members use personal devices on your network, the risk of data exfiltration rises—especially if those devices are unsecured.
BYOD Prevention Tips:
- Use a separate Wi-Fi network for personal devices
- Require endpoint protection (antivirus, encryption) on all connected devices
- Restrict access to shared folders or drives unless necessary
- Educate users about phishing attacks and risky downloads
- Enforce strong passwords and screen locks on all BYODs
These BYOD best measures help prevent unmonitored devices from becoming weak points in your system’s security chain.
7. Disable USB Ports (Optional for Admins)
If you manage multiple systems, disabling USB access can help prevent insider threats.
How to Disable USB Ports:
- Press Windows + R, type devmgmt.msc, hit Enter
- Expand Universal Serial Bus controllers
- Right-click each USB Root Hub and choose Disable device
8. Use a VPN on Public or Shared Networks

A VPN encrypts traffic and makes it harder for attackers to intercept data. Look for one with no logs and strong encryption.
Why Data Exfiltration Is a Serious Threat
Data breaches aren’t just embarrassing—they can be catastrophic. For individuals, leaked data may lead to identity theft or financial loss. For businesses, it can mean regulatory fines, damaged reputation, and loss of competitive advantage. According to the IBM Cost of a Data Breach Report, the global average cost of a data breach in 2023 was $4.45 million.
That’s a serious hit—and often avoidable.
Signs Your Windows PC May Be Compromised
If you suspect data is being exfiltrated, look for:
- Unusual outgoing network traffic
- Frequent system slowdowns or crashes
- Unknown background processes
- Disabled antivirus or firewall settings
- Sudden file changes or missing documents
Conclusion
Data exfiltration may not always leave obvious signs, but the damage it causes can be massive. Understand how it works, and follow proven prevention strategies can protect you from both external attackers and internal risks. To maximize your security on Windows 10, regularly update your system, limit user access, monitor activity, and use real-time malware protection.
For added peace of mind, consider scanning your PC with Fortect to catch the threats that may be quietly siphoning off your data.




