Self-Mutating Malware: Examples, Removal, and Prevention
Self-mutating malware, often referred to as polymorphic or metamorphic malware, is one of the most deceptive and difficult-to-remove threats targeting Windows devices. These threats don’t just hide; they constantly change their internal structure to avoid detection by traditional antivirus programs.
We’ll explain what self-mutating malware is, how it behaves, how to remove it from Windows 10/11, and how to prevent future infections with strong system practices and tools like Fortect.
What Is Self-Mutating Malware?
Self-mutating malware is a category of malicious software that alters its code automatically every time it replicates or executes. Unlike traditional malware that stays the same, these programs evolve continuously, making them harder to track and remove.
There are two key types of self-mutating malware:
Polymorphic Malware
Polymorphic malware modifies parts of its code each time it runs, but its core function stays the same. It uses encryption to generate fresh-looking versions of itself, making detection difficult. For instance, a polymorphic keylogger may arrive via a fake PDF. Once opened, it installs quietly and logs your keystrokes. When it replicates, it reshuffles code segments and encrypts its structure. Antivirus software sees each version as a new threat, even though it keeps logging data in the background.
Metamorphic Malware
Metamorphic malware fully rewrites its code every time it executes, changing not just appearance but internal logic. For example, a metamorphic worm might infect a media player, rewrite itself completely, and then move to another program. Every new version behaves differently at the code level while still corrupting files, disabling defenses, or opening system backdoors. Since no copy is ever the same, even advanced detection tools struggle to catch it.
These threats often disguise themselves as system processes and use deep obfuscation to hide. Because they bypass traditional antivirus, only behavior-based tools can detect and remove them effectively.
How to Remove Self-Mutating Malware on Windows 10/11?
- Boot into Safe Mode. Press Windows + R, type msconfig, then hit Enter. In the Boot tab, check “Safe boot”, click OK, and restart your PC.
- Run Microsoft Defender Offline Scan. Go to Settings > Update & Security > Windows Security > Virus & threat protection > Scan options. Select Microsoft Defender Offline Scan and click Scan now. Your system will reboot and run a deep scan offline.
- Uninstall suspicious programs. Open Control Panel > Programs > Uninstall a program. Review recently installed applications and remove anything unknown or unauthorized.
- Clean leftover malware in AppData. Press Windows + R, type %appdata%, and open the Roaming, Local, and LocalLow folders. Delete strange or newly created folders that don’t belong to trusted apps.
- Reset browser settings. In Chrome, go to Settings > Reset and clean up > Restore settings to their original defaults. Click Reset Settings.
- Return to normal boot. Open msconfig, uncheck Safe boot from the Boot tab, and restart your system normally.
Automatically Remove Self-Mutating Malware with Fortect
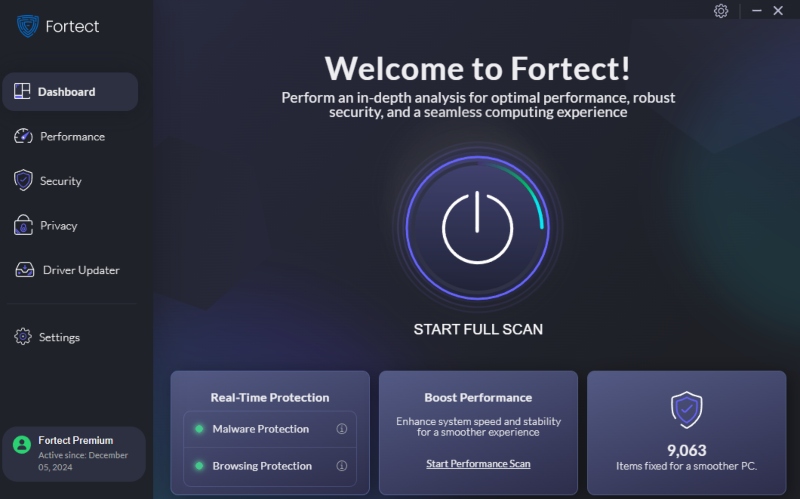
Fortect is a powerful repair and protection solution built to fight advanced malware threats, including polymorphic and87 metamorphic infections. It doesn’t rely on outdated virus signatures; instead, it uses behavior-based detection to catch malware that changes form on the fly. Once detected, Fortect removes the threat, repairs any corrupted system files, and restores missing Windows components.
It also fixes damaged settings and improves overall performance by cleaning up junk, crashing software, and broken registries. If malware has already affected system stability, Fortect repairs the damage and restores full functionality, without requiring manual cleanup or advanced knowledge.
Fortect Best Features
Fortect Browsing Protection
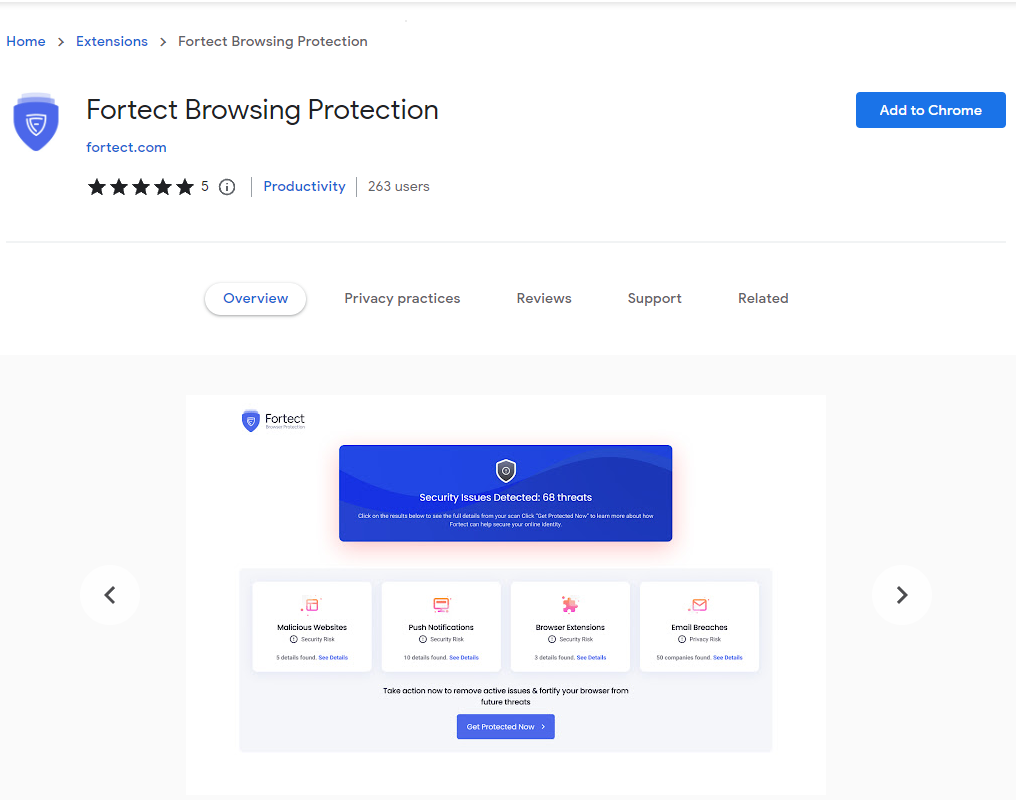
Fortect Browsing Protection is a Chrome extension that blocks malicious websites, phishing attempts, and infected scripts in real time. It helps prevent the initial entry point of many polymorphic and metamorphic threats, your web browser. To install, go to the Chrome Web Store, search “Fortect Browsing Protection,” and click Add to Chrome. If you’re using Fortect Premium, this feature also syncs with your Android device for cross-platform protection.
Fortect Driver Updater
Self-mutating malware often exploits vulnerable or outdated drivers to gain deeper access to your system. Fortect’s built-in Driver Updater scans your entire system, detects outdated or corrupted drivers, and installs the latest safe versions automatically. This reduces crash risk and improves system defense by closing common security gaps that malware uses to escalate privileges or spread through hardware-level access.
Fortect Mobile Security: Protection Without Compromise

If you’re using Fortect Premium on your Windows PC, you also gain access to Fortect Mobile Security for Android devices. It includes real-time protection, cloud-based scanning, automated threat resolution, and instant alerts for mobile-based malware and app risks. It also offers scheduled scans to ensure your Android stays clean and responsive. Fortect Mobile Security protects your mobile data without draining battery or slowing down performance, giving you seamless security across devices.
How to Prevent Self-Mutating Malware?
- Update Windows regularly: Go to Settings > Update & Security > Windows Update > Check for updates
- Use a standard user account for daily tasks: Open Control Panel > User Accounts > Manage another account, and downgrade any admin access that isn’t necessary
- Disable macros in Microsoft Office: Launch any Office app, click File > Options > Trust Center > Trust Center Settings > Macro Settings, then select Disable all macros with notification
- Install Fortect to enable real-time malware monitoring, system repair, driver updates, and full optimization in one security platform
Download and install Fortect today for complete security and peace of mind.
Conclusion
Self-mutating malware is not your average virus. It’s designed to hide, evolve, and attack from within, dodging every basic security measure you throw at it. By constantly rewriting its code, it breaks signature-based detection and outsmarts traditional antivirus. The only way to beat it is with advanced behavior-based tools and a layered approach. Fortect gives you that. It doesn’t just detect and remove these threats, it repairs the damage, strengthens your system, protects your browsing, updates your drivers, and extends its defense to your Android device. If you want full protection against modern threats, Fortect is built for exactly this kind of battle.