How to Prevent Windows Remote Code Execution Vulnerabilities
Remote Code Execution (RCE) vulnerabilities severely threaten Windows users, allowing attackers to execute malicious code on a target system remotely. Exploiting such vulnerabilities can lead to data breaches, malware infections, or complete system compromise. We will help you understand RCE vulnerabilities and how to prevent them effectively.
What Is a Remote Code Execution (RCE) Vulnerability?
A Remote Code Execution (RCE) vulnerability is a security flaw that allows an attacker to execute arbitrary code on a victim’s machine without physical access. These vulnerabilities often arise from unpatched software, insecure network configurations, or flaws in applications running on Windows.
Common Causes of RCE Vulnerabilities
- Unpatched Software – Attackers exploit outdated software with known security flaws.
- Weak Network Security – Poorly configured firewalls and open ports can be entry points.
- Malicious Files & Links – Phishing emails and compromised downloads can introduce RCE threats.
- Insecure Remote Desktop Services – Hackers can exploit Exposed RDP connections.
- Buffer Overflow & Injection Attacks – Poor application input validation can allow code execution.
How to Prevent RCE Vulnerabilities in Windows
1. Keep Windows and Software Updated
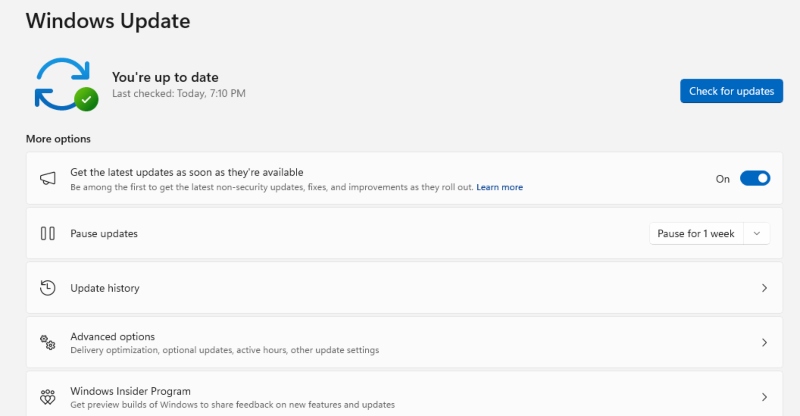
Microsoft frequently releases security patches to address RCE vulnerabilities. Keeping your System updated ensures that known exploits are patched.
Steps to Update Windows:
- Press Win + I to open Settings.
- Go to Update & Security > Windows Update.
- Click Check for updates and install any available updates.
2. Enable Windows Defender Firewall
A properly configured firewall helps prevent unauthorized access and reduces the risk of RCE attacks.
Steps to Enable Windows Defender Firewall:
- Open the Control Panel and navigate to System and Security.
- Click Windows Defender Firewall.
- Select Turn Windows Defender Firewall on or off.
- Enable it for both Private and Public networks.
3. Disable Unused Remote Services
RDP (Remote Desktop Protocol) is a common attack vector for RCE vulnerabilities. Disable it if you don’t use it.
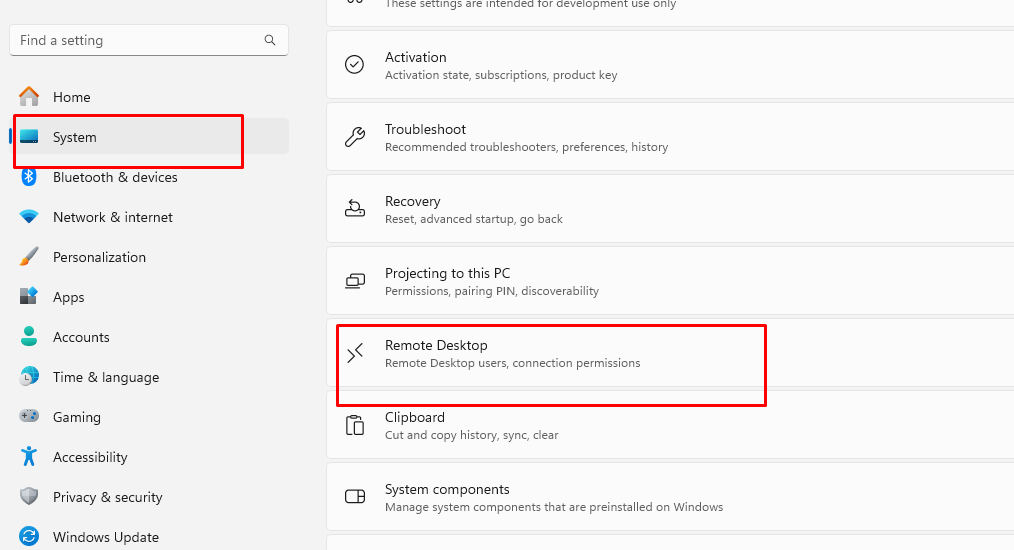
Steps to Disable Remote Desktop:
- Press Win + I and select System.
- Click Remote Desktop.
- Toggle Off under Enable Remote Desktop.
4. Use Strong Network Security Practices
Securing your network is crucial to preventing unauthorized access.
Best Practices:
- Use strong passwords and two-factor authentication (2FA) for remote access.
- Disable unnecessary ports and services.
- Enable Network Level Authentication (NLA) for RDP.
- Configure your router to block suspicious IPs.
5. Install an Advanced Security Solution
A robust security tool can detect and block RCE threats in real time. Fortect provides:
- Real-time malware protection against known and emerging threats.
- Repair corrupted system files to close security gaps.
- Performance optimization to reduce vulnerabilities.
Using Fortect, you can enhance your Windows security and prevent RCE exploits.
Download Fortect now to safeguard your system.
6. Avoid Suspicious Downloads & Email Attachments
Attackers often use malicious email attachments and downloads to inject RCE exploits.
Steps to Stay Safe:
- Do not open attachments from unknown senders.
- Verify software downloads from official websites.
- Use Microsoft Defender SmartScreen to block malicious sites.
7. Restrict User Privileges
Minimizing user permissions reduces the risk of attackers executing code with administrative access.
Steps to Restrict Privileges:
- Open Control Panel > User Accounts.
- Click Manage another account.
- Select an account and choose Change the account type.
- Set non-administrator accounts for daily use.
8. Enable Windows Exploit Protection
Windows includes built-in security features to mitigate exploits before they can cause harm.
Steps to Enable Exploit Protection:
- Open Windows Security via the Start Menu.
- Click App & Browser Control.
- Select Exploit Protection Settings.
- Ensure that settings like DEP (Data Execution Prevention) are enabled.
9. Microsoft Defender for Endpoint and Third-Party Antivirus Compatibility
If you have both Microsoft Defender for Endpoint and a third-party antivirus installed, Windows adjusts Defender Antivirus behavior based on your security configuration:
- Defender Disabled – If Defender for Endpoint isn’t used, Microsoft Defender Antivirus turns off when a third-party antivirus is active.
- Passive Mode – If Defender for Endpoint is enabled with another antivirus, Microsoft Defender Antivirus enters passive mode, meaning it won’t perform real-time threat remediation.
- EDR in Block Mode – With Endpoint Detection and Response (EDR) in block mode, Defender for Endpoint can still detect and block threats, even if another antivirus is active.
For non-persistent VDI machines, Microsoft recommends keeping Turn off Microsoft Defender Antivirus set to Not Configured. This allows Defender to enter passive mode automatically when a third-party antivirus is registered, ensuring critical security functions remain active.
Final Thoughts
Preventing Windows Remote Code Execution (RCE) vulnerabilities requires proactive security measures, including keeping your System updated, configuring your firewall, turning off unnecessary remote services, and using security software. Implementing these steps can significantly reduce your risk of an RCE attack, ensuring your Windows PC remains secure and stable.
By staying vigilant and utilizing tools like Fortect for real-time malware protection and system optimization, you can further enhance your defense against evolving cyber threats.




