Ghost Ransomware: How It Works and How to Stop It
Ghost ransomware has emerged as a dangerous threat that can lock your personal files and demand payment for their release. Understanding how this malware operates and implementing proper protection measures can save you from losing precious photos, documents, and memories stored on your Windows computer.
What Is Ghost Ransomware?
Ghost ransomware is a type of malicious software that encrypts files on your computer, making them completely inaccessible. Once infected, you’ll find your documents, images, videos, and other personal files scrambled with strong encryption. The attackers then display a ransom note demanding cryptocurrency payment in exchange for the decryption key.
This particular ransomware variant targets Windows users specifically, exploiting system vulnerabilities and user behavior to gain access to your device. Unlike simple viruses, Ghost ransomware focuses on extortion rather than system damage, holding your data hostage until you pay.
How Ghost Ransomware Infects Your Computer
Common Distribution Methods
Ghost ransomware typically spreads through phishing emails containing infected attachments or malicious links. You might receive what appears to be a legitimate invoice, delivery notification, or urgent message from a trusted company. Opening these attachments or clicking embedded links can trigger the infection.
Other distribution methods include:
- Fake software downloads: Cracked programs, illegal game downloads, or counterfeit software updates often contain ransomware payloads.
- Compromised websites: Visiting infected websites can automatically download malware through exploit kits that target outdated browsers or plugins.
- Removable media: USB drives and external hard drives from unknown sources may carry the infection.
- Remote Desktop Protocol attacks: If you’ve enabled remote access without proper security, attackers can exploit weak passwords to install ransomware directly.
The Encryption Process
Once Ghost ransomware executes on your system, it works quickly. The malware scans your hard drive for specific file types, documents, spreadsheets, photos, videos, and databases. It then encrypts these files using military-grade encryption algorithms, making them unreadable without the unique decryption key held by the attackers.
How to Protect Your Windows Computer from Ghost Ransomware
Use Advanced Protection with Fortect
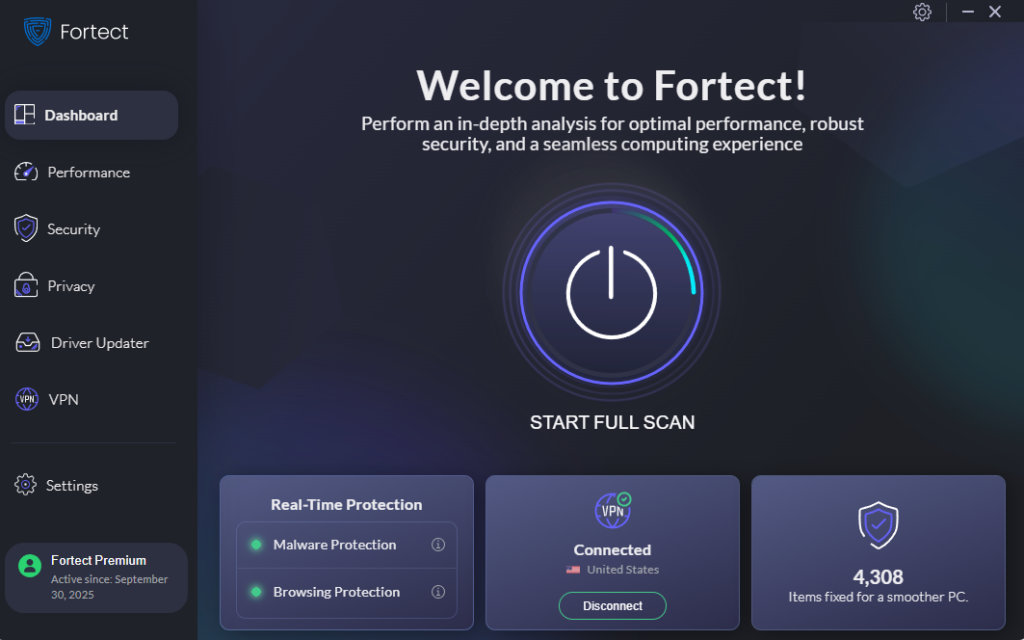
For comprehensive defense against Ghost ransomware and other malware threats, consider using Fortect, a powerful and advanced anti-virus solution with real-time malware protection. Fortect automatically scans your Windows PC for any threats, including Ghost ransomware, then fixes them and optimizes your computer for peak performance.
Fortect Premium includes a built-in Driver Updater that automatically scans your Windows PC for outdated or corrupted drivers and updates them safely from trusted sources. This feature is crucial for security because corrupted or outdated drivers are more than just a performance issue; hackers can exploit them to inject malware into your system. Because drivers communicate directly with the system kernel, any compromise can lead to serious instability or even a complete system takeover.
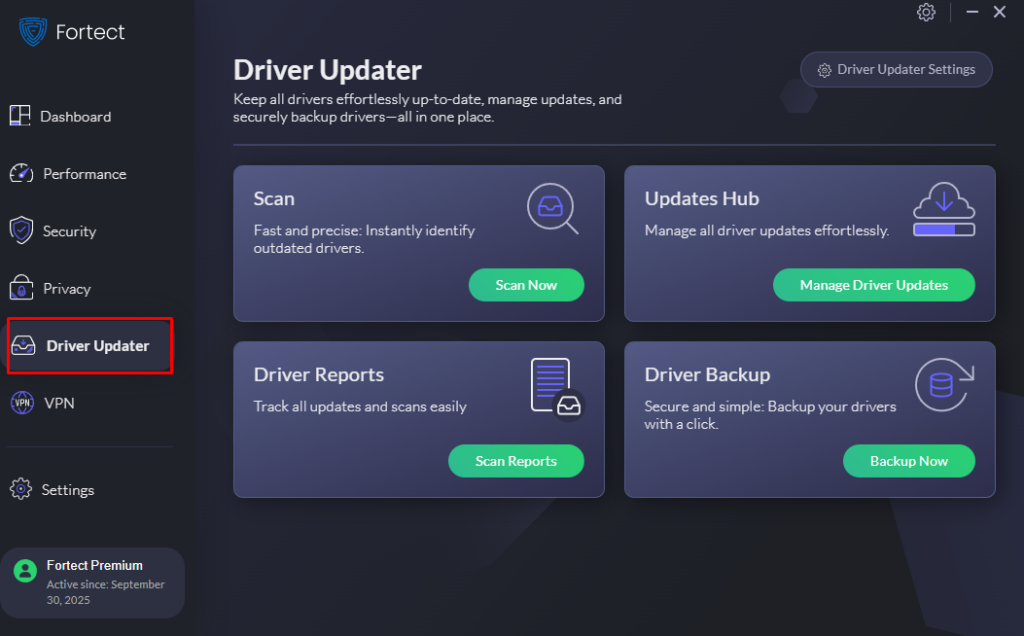
By keeping your drivers updated, Fortect not only closes these security gaps but also ensures your PC runs smoothly. Once the updates are applied, your computer is optimized for cleaner, faster, and more reliable performance, giving you peace of mind against ransomware attacks.
Download and install Fortect now and be securely protected.
Keep Windows Updated
Regular system updates patch security vulnerabilities that ransomware exploits.
Steps to Update Windows 10/11:
- Click the Start button and select Settings (gear icon)
- Navigate to Update & Security (Windows 10) or Windows Update (Windows 11)
- Click Check for updates
- If updates are available, click Download and install
- Restart your computer when prompted
- Enable Automatic updates by clicking Advanced options and ensuring updates install automatically
Enable Windows Security Features
Steps to Configure Windows Defender:
- Open Settings and select Privacy & Security (Windows 11) or Update & Security (Windows 10)
- Click Windows Security, then Open Windows Security
- Select Virus & threat protection
- Click Manage settings under Virus & threat protection settings
- Turn ON Real-time protection, Cloud-delivered protection, and Automatic sample submission
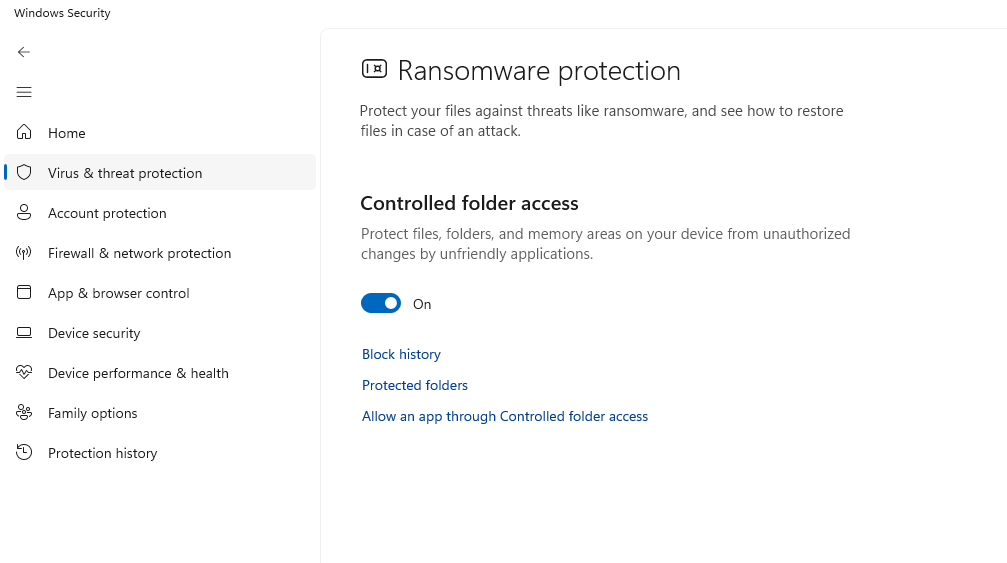
- Enable Ransomware protection and click Manage ransomware protection
- Turn ON Controlled folder access to protect important folders from unauthorized changes
Create Regular Backups
Backing up your files renders ransomware ineffective; you can simply restore your data without paying.
Steps to Set Up Windows Backup:
- Connect an external hard drive to your computer
- Open Settings and go to Update & Security (Windows 10) or System > Storage (Windows 11)
- Click Backup and select Add a drive
- Choose your external drive from the list
- Click More options to customize which folders to back up
- Set backup frequency and how long to keep backups
- Store the backup drive disconnected from your computer when not in use
Practice Safe Browsing Habits
Avoid downloading software from untrusted sources and never open email attachments from unknown senders. Verify the authenticity of emails before clicking links, especially those creating urgency or requesting immediate action. Hover over links to preview URLs before clicking, and be suspicious of unexpected file extensions like .exe, .scr, or .zip in email attachments.
Use Strong Passwords and Enable User Account Control

Steps to Enable UAC:
- Type UAC in the Windows search bar
- Select Change User Account Control settings
- Move the slider to Always notify or at least the second level
- Click OK and restart if prompted
What to Do If You’re Infected
If Ghost ransomware has encrypted your files, disconnect from the internet immediately to prevent further spread. Do not pay the ransom; there’s no guarantee you’ll receive the decryption key, and paying the ransom funds criminal operations.
Run a full system scan with Windows Defender or reputable antivirus software. Consider using specialized ransomware removal tools from trusted security companies. If you have recent backups, wipe your system and restore your files after confirming the malware is completely removed.
Stay Protected with Vigilance
Ghost ransomware prevention requires consistent security practices. By keeping your system updated, maintaining offline backups, and exercising caution online, you can protect your valuable personal data from this devastating threat.




