Email Spoofing: Definition, Identification, and Prevention
Email spoofing has become one of the most prevalent cyber threats targeting everyday internet users. If you’ve ever received a suspicious email that appears to be from someone you know, but something feels off, you may have encountered a spoofed message. Understanding this threat is your first line of defense against potential scams, identity theft, and malware infections.
What is Email Spoofing?

Email spoofing is a deceptive technique where cybercriminals forge the sender’s email address to make a message appear as though it’s coming from a trusted source. Think of it as digital forgery, similar to someone writing a fake return address on a physical letter.
How Email Spoofing Works?
Attackers exploit vulnerabilities in email protocols, particularly the Simple Mail Transfer Protocol (SMTP), which doesn’t verify the sender’s identity by default. Using specialized software or scripts, scammers can manipulate email headers to display any sender address they choose. This means a fraudulent email could appear to come from your bank, a family member, or even your own email address.
The primary goal? To trick you into revealing sensitive information, clicking malicious links, or downloading harmful attachments.
How to Identify Spoofed Emails
Recognizing fake emails requires attention to detail. Here are the telltale signs:
Sender Address Discrepancies
Hover your mouse over the sender’s name without clicking. The actual email address often reveals inconsistencies, like “[email protected]” instead of the legitimate “[email protected].” Notice the subtle dash? That’s a red flag.
Suspicious Email Content
Spoofed messages typically create urgency: “Your account will be suspended!” or “Verify your information immediately!” Legitimate organizations rarely demand immediate action through unsolicited emails. Poor grammar, generic greetings like “Dear Customer,” and threatening language are common indicators.
Unexpected Attachments or Links
If you receive an unexpected attachment or link from a known contact, verify directly with them using a different communication method before opening anything. Phishing links often lead to fake websites designed to steal your credentials.
Mismatched URLs
Before clicking any link, hover over it to preview the destination URL. If the displayed text says “microsoft.com” but the actual link points to “micros0ft-security.ru,” you’re looking at a spoofed email.
How to Protect Yourself from Email Spoofing on Windows
Taking proactive measures significantly reduces your vulnerability to email spoofing attacks.
Enable Email Authentication Settings
For Windows Mail App:
- Open the Windows Mail app from your Start menu
- Click the Settings icon (gear symbol) at the bottom left
- Select “Manage Accounts” and choose your email account
- Click “Change mailbox sync settings”
- Scroll down and enable “Download images automatically” to OFF (prevents tracking pixels)
- Under advanced settings, ensure SSL is enabled for both incoming and outgoing servers
Update Your Windows System Regularly
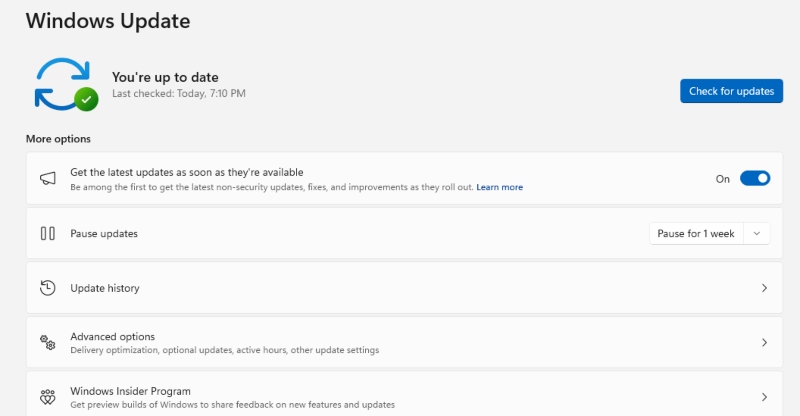
Keeping Windows updated ensures you have the latest security patches:
- Press Windows Key + I to open Settings
- Click “Windows Update” in the left sidebar
- Click “Check for updates”
- If updates are available, click “Download & install”
- Restart your computer when prompted
- Enable automatic updates by clicking “Advanced options” and ensuring “Receive updates for other Microsoft products” is toggled ON
Configure Advanced Email Security
Set up spam filters in Outlook:
- Open Outlook desktop application
- Go to Home tab > Junk > Junk E-mail Options
- Select the “Safe Lists Only” option for maximum protection
- Add trusted contacts to your Safe Senders list
- Enable “Permanently delete suspected junk e-mail” if desired
Install Reliable Antivirus Software
Windows Defender provides baseline protection, but ensure it’s properly configured:
- Press Windows Key + I for Settings
- Navigate to “Privacy & security” > “Windows Security”
- Click “Virus & threat protection”
- Ensure “Real-time protection” is turned ON
- Click “Manage settings” and enable “Cloud-delivered protection”
- Run regular scans by clicking “Scan options” > “Full scan”
Enhance Protection with Fortect
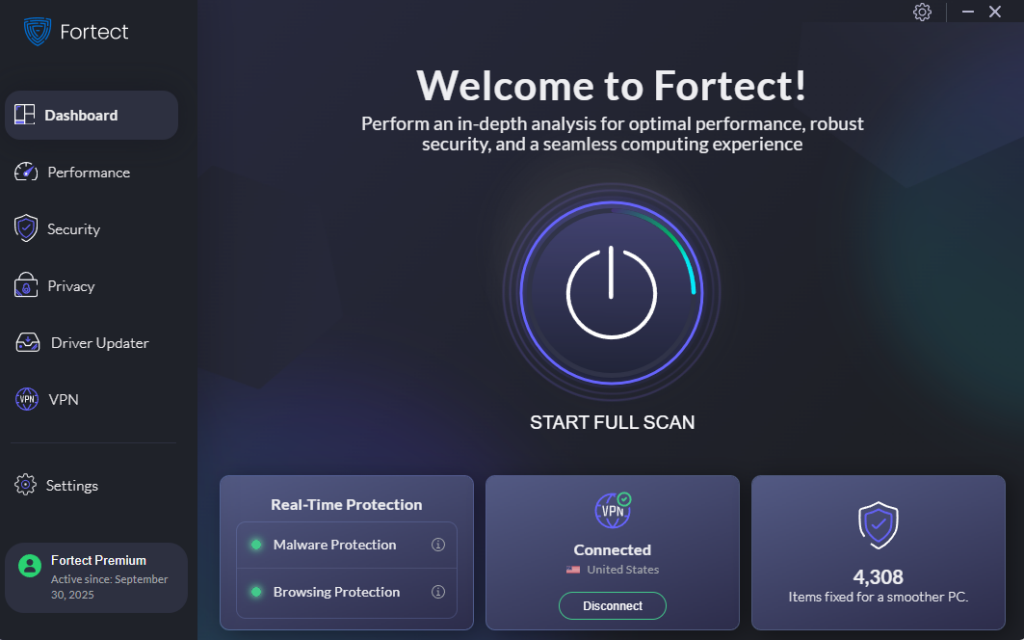
For comprehensive defense against email spoofing and related threats, consider upgrading to Fortect, a powerful and advanced anti-virus solution with real-time malware protection. Fortect automatically scans your Windows PC for any threats, including those delivered through spoofed emails, then fixes them and optimizes your computer for peak performance.
Fortect Premium includes a built-in Driver Updater that automatically scans your Windows PC for outdated or corrupted drivers and updates them safely from trusted sources. This feature is crucial for security: corrupted or outdated drivers aren’t just performance issues; hackers can exploit them to inject malware into your system. Because drivers communicate directly with the system kernel, any compromise can lead to serious instability or even a complete system takeover.
By keeping your drivers updated, Fortect closes these critical security gaps while ensuring your PC runs smoothly. Once the updates are applied, your computer is optimized for cleaner, faster, and more reliable performance, giving you comprehensive protection against email spoofing attacks and other cyber threats.
Download and install Fortect for your Windows devices today!
Additional Prevention Best Practices
Beyond technical measures, smart email habits are essential. Never share personal information via email, even if the request seems legitimate. Use two-factor authentication wherever possible; this adds an extra layer of security, even if your password is compromised.
Create strong, unique passwords for each account using a password manager. Consider using email aliases for online registrations to limit exposure of your primary email address. When in doubt, contact the supposed sender through official channels listed on their verified website, not through information provided in the suspicious email.
Email Spoofing on macOS and Prevention
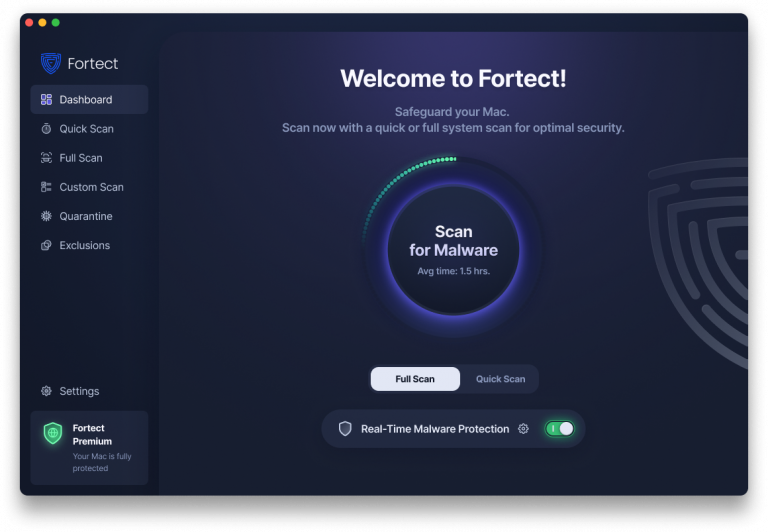
Fortect Mac Suite is now available on macOS. As macOS grows in popularity, it’s increasingly targeted by email spoofing, ransomware, and malware. Fortect Mac Suite bridges that security gap with advanced, real-time protection and cloud-based threat detection to keep your system safe.
- Smart Scan: Quickly detects and fixes issues.
- Full System Scan: Performs deep scans for complete security.
- Cloud-Based Defense: Ensures up-to-date protection against evolving threats.
Stay ahead of attackers with Fortect’s powerful, all-in-one protection for macOS. Download Fortect Mac Suite now.
Prevention:

Keep macOS Updated: Regularly install system updates via Apple Menu > System Settings > General > Software Update to patch security flaws.
Use Apple Mail’s Junk Filter: Enable and train Apple Mail’s junk mail filter to automatically detect suspicious or spoofed messages.
Check Sender Details Carefully: Hover over or tap the sender’s name to reveal the real email address. Spoofed emails often have misspelled or strange domains.
Avoid Clicking Unknown Links: Hover over links before clicking to ensure they lead to legitimate websites.
Enable Two-Factor Authentication (2FA): Add an extra layer of security to your Apple ID and email accounts to prevent unauthorized access.
Use a Reputable Antivirus (like Fortect Mac Suite): Protect your Mac against malware or phishing payloads that may arrive through spoofed emails.
Disable Remote Content in Emails: Go to Mail > Settings > Privacy and check Protect Mail Activity to block email tracking and remote content loading.
Use a Secure DNS Service: Services like Cloudflare DNS (1.1.1.1) or Quad9 (9.9.9.9) help block malicious email links and phishing domains.
Conclusion
Email spoofing preys on trust and urgency. By understanding what spoofed emails look like, keeping your Windows system updated, and implementing proper security measures, you can significantly reduce your risk. Remember: legitimate organizations will never pressure you to act immediately via email or request sensitive information through unsecured channels.
Stay vigilant, verify before you trust, and when something feels wrong, it probably is. Your digital safety depends on your awareness and proactive security habits.




