DLL Sideloading: Detection and Prevention
DLL sideloading is a stealthy attack method cybercriminals use to trick Windows into loading a malicious Dynamic Link Library (DLL) file instead of a legitimate one. This technique has been increasingly used in malware campaigns, ransomware attacks, and advanced persistent threats (APTs). If you’re a Windows 10 or Windows 11 user, understanding how DLL sideloading works and knowing how to prevent it can help protect your system from compromise.
What Is DLL Sideloading?
DLL sideloading (also called DLL hijacking) is when attackers place a malicious DLL file in the same folder as a legitimate application. Since Windows applications often search for required DLLs in their local directory first, the program may end up loading the attacker’s DLL instead of the trusted one. This gives the malicious DLL the same level of privilege as the original application, allowing attackers to execute malware silently in the background, steal sensitive information, install backdoors for remote access, and disable antivirus or security tools.
How to Detect DLL Sideloading on Windows
Detecting DLL sideloading can be tricky because attackers use legitimate applications to execute their code. However, there are ways to identify suspicious activity.
1. Monitor Running Processes
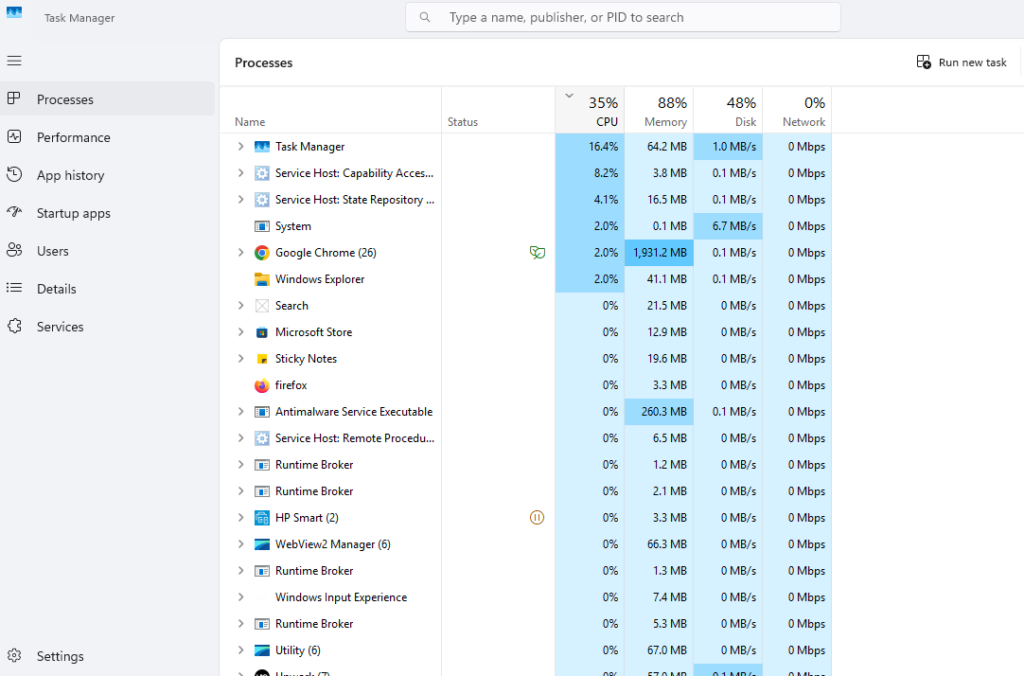
Open Task Manager (Ctrl + Shift + Esc) and check unfamiliar processes. Look for applications running from unusual directories (e.g., temp folders).
2. Check DLL File Paths
Use Process Explorer from Microsoft Sysinternals. Identify which DLLs are loaded by a process and investigate DLLs loaded from non-standard paths.
3. Enable Windows Event Logging
Enable Audit Process Creation in Local Security Policy. Logs will help track DLL loads from unauthorized folders.
4. Use Antivirus and Threat Detection Tools
Keep your antivirus updated. Utilize advanced tools such as Windows Defender Advanced Threat Protection (ATP) or third-party security software to receive real-time alerts.
How to Prevent DLL Sideloading on Windows 10/11
Preventing DLL sideloading requires a combination of good security practices and system hardening.
1. Keep Windows Updated
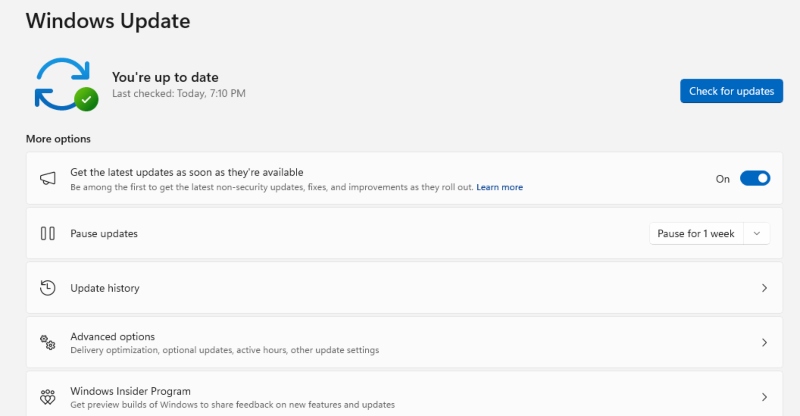
Microsoft regularly patches vulnerabilities exploited in DLL sideloading attacks.
Steps to Update Windows 10/11: Press Windows + I to open Settings. Go to Update & Security (Windows 10) or Windows Update (Windows 11). Click Check for updates. Install all available updates and restart your computer.
2. Restrict User Privileges
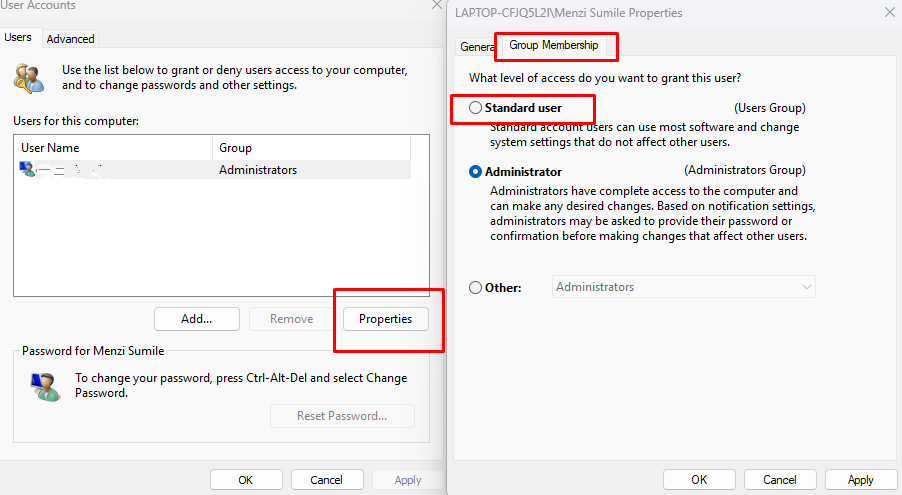
Limit user permissions so malware can’t exploit DLL sideloading easily.
Steps to Restrict Users in Windows 10/11: Press Windows + R, type netplwiz, and press Enter. Select the user account and click Properties. Under Group Membership, choose Standard User instead of Administrator. Click Apply > OK.
3. Use Application Whitelisting
Configure Windows Defender Application Control or third-party tools to only allow approved apps and DLLs.
4. Harden Directory Permissions
Restrict write access to folders where applications are stored. Ensure that only trusted administrators can place DLLs in system directories.
5. Regular Malware Scans
Run full system scans to catch malicious DLLs before they execute.
How to Detect Dylib (DLL Equivalent) Sideloading on macOS
Although DLL sideloading is Windows-specific, macOS faces similar risks through dylib sideloading. Attackers can trick apps into loading malicious dynamic libraries, leading to privilege escalation or data theft. To detect this on macOS:
- Monitor Loaded Libraries
Use tools like otool -L <application> or dyldinfo to check which libraries an app loads. Unexpected or unsigned libraries may indicate tampering. - Enable System Integrity Protection (SIP)
Ensures critical system files and directories cannot be altered by malicious code. - Check Code Signing
Verify apps and libraries are signed by trusted developers using codesign -v <file>. Unsigned or improperly signed libraries can be a red flag. - Use Endpoint Security Tools
Advanced security tools can monitor library load events in real time and alert you to suspicious activity.
How to Protect Against DLL Sideloading with Fortect
Fortect is a powerful antivirus with real-time malware protection that can detect and stop DLL sideloading attempts. It automatically scans your Windows PC for malicious DLLs, unsafe processes, and hidden threats, then fixes them to keep your system secure.
With its automated repair tools, Fortect not only eliminates malware but also restores damaged system files, keeping Windows running smoothly.
Download and install Fortect now for your Windows and macOS.
DLL Sideloading vs. DLL Hijacking
While often confused, these two attacks differ in scope. DLL sideloading occurs when a trusted program loads a malicious DLL that is placed in its own folder. DLL hijacking, on the other hand, exploits Windows’ DLL search order to trick the system into loading a rogue DLL from an unintended location. In short, all sideloading is hijacking, but not all hijacking is sideloading.
Conclusion
DLL sideloading is a dangerous but preventable attack technique. By keeping Windows updated, restricting user privileges, monitoring suspicious processes, and using advanced security tools, you can reduce the risk of falling victim to DLL hijacking. For extra protection, security software like Fortect provides real-time defense against DLL sideloading and other malware threats, helping you maintain a safe and optimized Windows environment.




