Common Types of Phishing Attacks to Watch in 2025
Phishing attacks remain one of the most dangerous cyber threats facing internet users today. With an estimated 3.4 billion spam emails sent daily, cybercriminals continue to evolve their tactics. We will explore the most common types of phishing attacks and practical steps to protect your personal data.
What is Email Phishing?

Email phishing is the most widespread form of phishing, where cybercriminals send fraudulent emails that appear to come from trusted sources like banks, Amazon, PayPal, or streaming platforms. These messages contain malicious links or attachments designed to steal your credentials.
Red Flags to Watch For
- Generic greetings like “Dear Customer”
- Urgent or threatening language
- Suspicious sender addresses with misspellings
- Unexpected attachments or links
- Requests for passwords or sensitive information
Spear Phishing: Personalized Attacks
Spear phishing involves highly targeted attacks using information from your social media and online activity. Attackers craft convincing messages referencing your actual purchases, subscriptions, or interests, making these attacks significantly more dangerous than generic phishing emails.
Smishing: SMS Text Message Phishing
Smishing uses text messages to deceive victims. Common examples include fake package delivery notifications, banking alerts claiming suspicious activity, tax messages, and prize notifications. Be wary of unexpected texts with shortened links or urgent requests.
Whaling: Attacking Executives

Whaling is a specialized form of spear phishing that targets high-level executives, managers, or individuals with financial authority. Attackers impersonate CEOs or CFOs to authorize fake wire transfers or gain access to sensitive corporate information.
Vishing: Voice Call Phishing
Vishing attacks involve phone calls from scammers pretending to be tech support, banks, or government agencies. Voice phishing rose 442% in late 2024 as AI deepfakes bypass detection tools. Attackers now use AI-powered voice cloning to impersonate family members in emergency scams. Never provide sensitive information over unsolicited calls.
Smishing: SMS Text Phishing
Smishing uses SMS messages to trick users. Common tactics include fake banking alerts, package delivery notifications, tax refund scams, or prize winnings. Shortened URLs and urgent wording are key signs of smishing attempts.
HTTPS Phishing: Fake Secure Websites

Cybercriminals now exploit the lock icon (HTTPS) to trick users. Just because a website shows HTTPS doesn’t mean it’s safe. Phishers buy cheap SSL certificates for fake sites, making them appear trustworthy.
Tip: Always double-check the domain name before entering login credentials.
Quishing: QR Code Phishing
Quishing exploits QR codes to deliver malicious links. These appear on fake parking notices, fraudulent payment requests, and malicious advertisements. Only scan QR codes from trusted sources and use apps that preview URLs before opening.
AI-Powered Phishing: The New Threat
Artificial intelligence has made phishing attacks smarter and more convincing. Cybercriminals use AI to generate grammatically perfect emails, create personalized content, and produce realistic deepfake videos and audio of people you know, making detection increasingly difficult.
Pharming: Redirecting Legitimate Traffic
Pharming manipulates DNS settings to redirect you to fake websites, even if you type the correct address. For example, typing www.yourbank.com may secretly lead you to a malicious site designed to steal your data.
Evil Twin Phishing: Rogue Wi-Fi

Attackers set up a fake Wi-Fi hotspot with a familiar name (e.g., “CoffeeShop Wi-Fi”). Once you connect, they intercept your internet traffic, capturing passwords and financial details.
Clone Phishing: Copying Legitimate Emails
In clone phishing, attackers duplicate a legitimate email (like a shipping confirmation) but replace the original links with malicious ones. Since the email looks familiar, victims are more likely to click.
Social Engineering
Phishing is often successful because of social engineering, the psychological manipulation of victims. Attackers exploit trust, urgency, and fear to pressure users into acting without thinking.
Man-in-the-Middle (MiTM) Attacks
In MiTM phishing attacks, hackers secretly intercept communications between you and a trusted website. For example, while logging into your bank account on a compromised network, an attacker may capture your credentials in real time.
Search Engine and Pop-up Phishing
Search engine phishing involves malicious websites ranking high for customer service numbers or software downloads. Pop-up phishing displays fake security warnings claiming your computer has viruses. Always verify URLs before clicking and never call numbers displayed in pop-ups.
Social Media Phishing
Social media phishing targets platforms like Facebook, Instagram, LinkedIn, and X (Twitter). Attackers create fake profiles, hijack legitimate accounts, or send malicious links through direct messages. They often lure victims with free giveaways, fake promotions, or urgent account recovery notices. Since many users trust messages coming from friends or official-looking accounts, these attacks are especially effective.
Tip: Always verify profiles, avoid clicking unknown links in DMs, and enable two-factor authentication on your social accounts.
How to Protect Your Windows 10/11 System from Phishing
Enable Windows Security Features
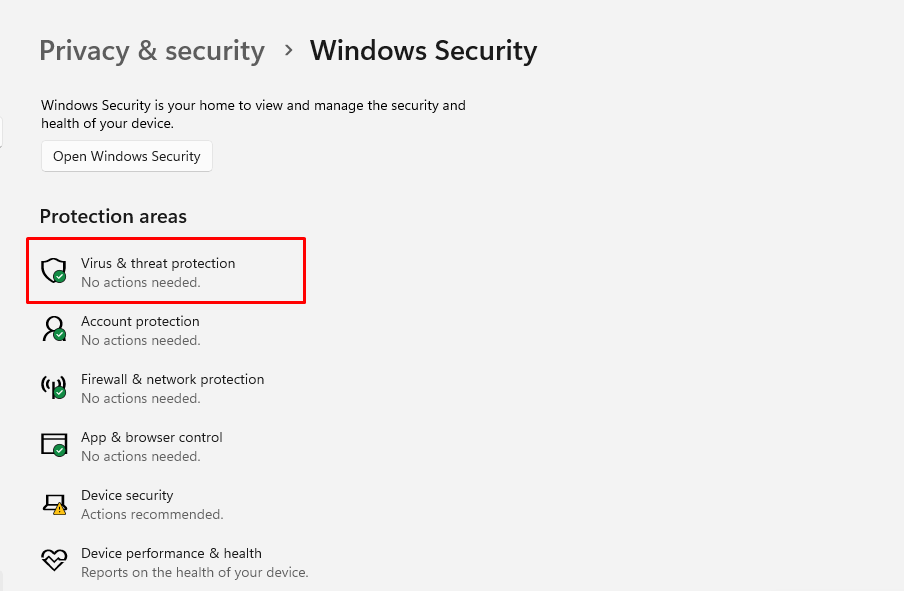
- Open Settings > Update & Security > Windows Security
- Click Virus & threat protection and enable Real-time protection
- In Microsoft Edge, go to Settings > Privacy, search, and services
- Enable Microsoft Defender SmartScreen and Block potentially unwanted apps
Keep Windows Updated
- Open Settings > Update & Security > Windows Update
- Enable automatic updates in Advanced options
- Click Check for updates and install all available updates
Set Up Multi-Factor Authentication
- Open Settings > Accounts > Sign-in options
- Set up Windows Hello (PIN, Face, or Fingerprint)
- Visit account.microsoft.com and enable Two-step verification
Configure Browser Security
- In Edge, enable SmartScreen and password breach warnings
- Block pop-ups under Website permissions
- Clear browsing data regularly (Ctrl + Shift + Delete)
- Remove suspicious browser extensions
Enhanced Protection with Fortect
For comprehensive protection against types of phishing attacks and their consequences, consider using Fortect, a powerful and advanced anti-virus solution with real-time malware protection. Fortect automatically scans your Windows PC for any threats, including phishing-related malware, then fixes them and optimizes your computer.
Fortect Premium includes a DRIVER Updater feature that automatically scans your Windows PC for any corrupt or outdated drivers and updates them from a safe source. Corrupted drivers are often exploited as entry points for malware infiltration from phishing attacks. Once Fortect updates your system, it optimizes your PC for clean and faster performance, ensuring your defenses stay strong against evolving phishing threats.
Download and install Fortect today.
Use Strong Passwords and Enable Protection
- Use unique passwords for every account (minimum 12 characters)
- Enable two-factor authentication on all accounts
- Use Edge’s built-in password generator
- Open Windows Security > Virus & threat protection
- Enable Controlled folder access for ransomware protection
Best Practices for Personal Protection
- Never click links in unsolicited emails or texts
- Hover over links to preview URLs before clicking
- Manually type website URLs instead of clicking email links
- Use HTTPS-secured websites for shopping and banking
- Keep devices updated and limit social media information
- Review app permissions before installing
Responding to a Phishing Attack
If You Clicked a Phishing Link
- Disconnect from the internet immediately
- Run a full Windows Security scan
- Change passwords for all accounts
- Enable two-factor authentication
- Monitor accounts for unauthorized activity
If You Provided Information
- Contact your bank and credit card companies immediately
- Place fraud alerts with credit bureaus
- File an identity theft report at IdentityTheft.gov
- Change all passwords and security questions
Where to Report Phishing
- Forward phishing emails to [email protected]
- Report to the FTC at reportfraud.ftc.gov
- Text 7726 (SPAM) to report phishing texts
Conclusion: Stay Vigilant Against Phishing
Understanding the various types of phishing attacks is crucial for protecting yourself in 2025. From traditional email phishing to sophisticated AI-powered deepfakes, cybercriminals continue to evolve their tactics. By implementing robust security measures on your Windows system and maintaining skepticism toward unsolicited communications, you can significantly reduce your risk. Remember: when in doubt, verify. Stay alert, stay educated, and stay secure.




