AI-Driven Brute Force Attacks on Windows PC
AI has drastically reshaped the formation of cyberattacks. One of the most alarming advancements is the rise of AI-driven brute force attacks. These attacks no longer rely on blind guessing. Instead, they use machine learning to predict and adapt, making them faster, more accurate, and harder to stop. For Windows 10 and 11 users, understanding and defending against this threat is more crucial than ever.
What Are AI-Driven Brute Force Attacks?

AI-driven brute force attacks use artificial intelligence to automate and refine the process of guessing credentials like usernames and passwords. Unlike traditional methods that try millions of combinations without logic, AI leverages patterns, leaked data, and behavioral trends to increase its success rate. These attacks can target login pages, remote desktop services, cloud accounts, and even encrypted files.
Why They’re More Dangerous?
AI enables attackers to bypass basic protections by adapting in real-time. It can identify the most likely password structures based on user demographics, common trends, and previous breaches. These attacks are not only faster but harder to detect because the AI knows how to avoid triggering standard security alerts.
How to Protect Your Windows 10/11 PC from AI-Driven Brute Force Attacks?
Here are effective steps to block, detect, and reduce the risk of AI brute force attacks on your PC.
Keep Windows and Drivers Up to Date
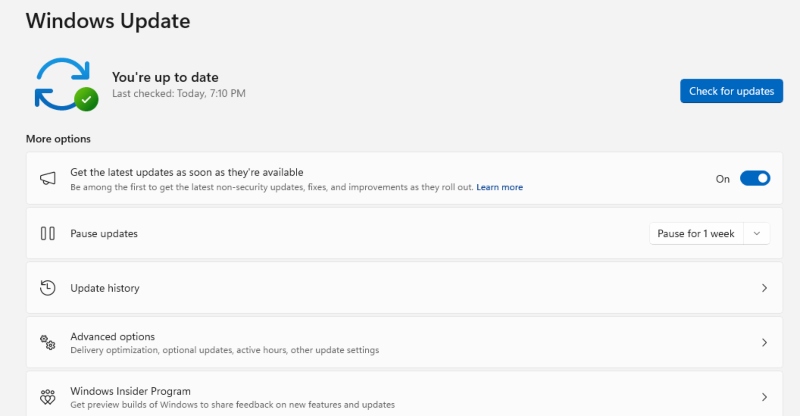
Outdated systems are easier to exploit. Attackers often combine brute force with known vulnerabilities.
To update Windows:
- Go to Settings > Update & Security > Windows Update
- Click Check for updates and install if available
Use Strong and Unique Passwords
Avoid dictionary-based or common passwords. Use complex passphrases or a password manager that generates unique logins for every service.
Enable Account Lockout Policy
This prevents attackers from endlessly guessing credentials.
To enable this:
- Press Windows + R, type secpol.msc, then hit Enter
- Go to Account Policies > Account Lockout Policy
- Set Account lockout threshold (e.g., 5 invalid attempts)
- Set the lockout duration and reset time accordingly
Disable Remote Desktop if Not Needed
RDP is a common target. Disable it if you don’t need it.
To disable:
- Go to Settings > System > Remote Desktop
- Turn Remote Desktop off
- Confirm your choice
How to Fix Brute Force Exploits and Optimize Your PC with Fortect
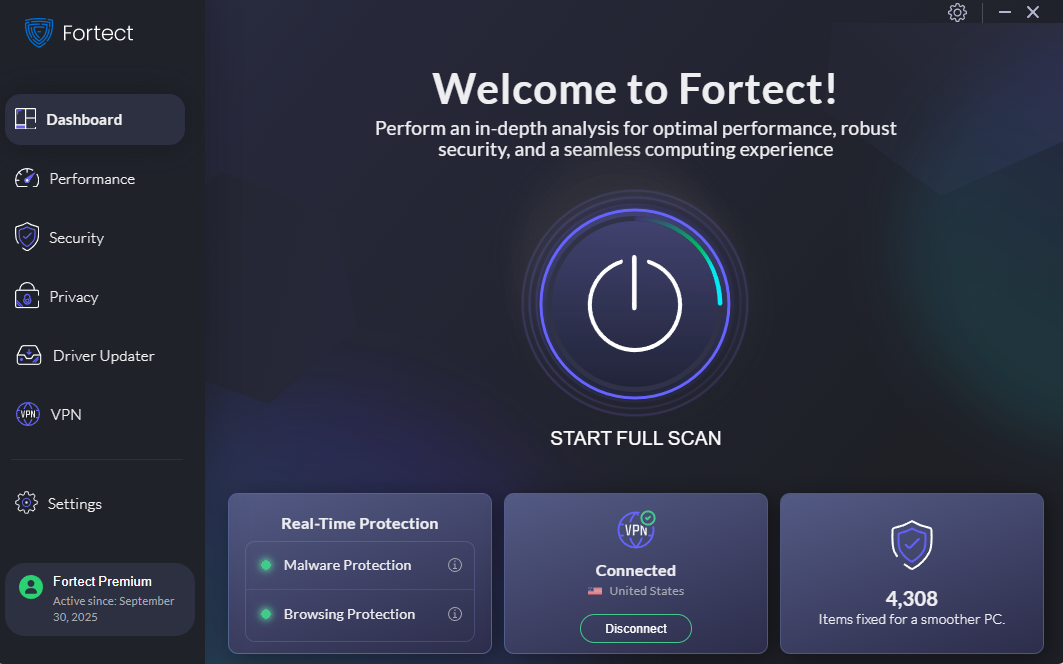
Fortect is a powerful and out-of-the-box optimization and malware defense tool that protects against the aftermath of AI-driven brute force attacks. If your system has already been affected, whether through corrupted files, performance drops, or failed login scripts, Fortect automatically scans your Windows PC, identifies the threat, fixes affected files, and restores system stability.
To use Fortect:
- Download and install Fortect on your Windows PC
- Launch the app and allow the initial system scan to complete
- Review the scan results, which include corrupted files, vulnerabilities, and performance issues
- Click Start Repair to automatically fix problems and optimize your system
Fortect acts as both a repair tool and a proactive optimizer, removing junk files, fixing crashes, and restoring performance degraded by brute force attacks or other malware.
Three Fortect Features That Strengthen Your Security
Fortect Browsing Protection
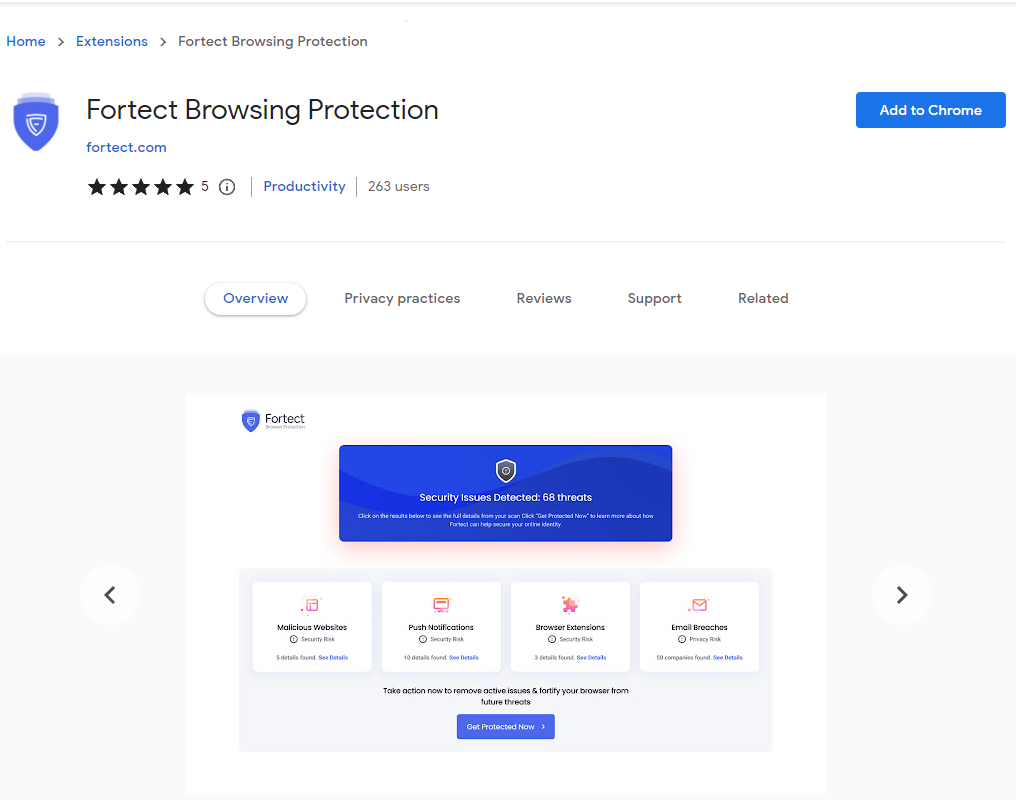
This extension offers real-time protection while you browse by blocking malicious websites and phishing pages. It’s lightweight, installs in seconds, and integrates seamlessly with Chrome.
To install it on Chrome:
- Go to the Chrome Web Store
- Search for Fortect Browsing Protection
- Click Add to Chrome, then confirm the installation
Fortect Browsing Protection also supports Android if you’re using a Fortect Premium plan.
Fortect Driver Updater
Brute force attacks sometimes exploit outdated drivers to bypass protections. Fortect Driver Updater scans for corrupted or outdated drivers and updates them automatically, preventing performance issues and minimizing security gaps.
Fortect Mobile Security
Fortect Mobile Security protects Android and iOS devices with real-time scanning, scheduled scans, cloud-based malware detection, and automated issue resolution. With a Fortect Premium account, you can extend protection from your Windows PC to your mobile device effortlessly.
Download and install Fortect now and experience utmost security with cross-platform functionality.
How AI Brute Force Targets Windows Systems
Windows PCs are often targeted due to features like Remote Desktop Protocol (RDP), local admin access, and Microsoft accounts. AI tools scan for open ports and login prompts, then begin an automated assault. Systems with weak or reused passwords, outdated defenses, or inactive account protections are prime targets.
Common Entry Points
- Remote Desktop access
- Microsoft login credentials
- Local admin accounts
- Unprotected network drives and folders
Warning Signs of a Brute Force Attack
If you’re using Windows and notice the following, you might be under attack:
- Multiple failed login attempts in a short time
- Unexpected account lockouts or password reset emails
- Unrecognized devices or IP addresses in the login history
- High CPU or network usage even when idle
Conclusion
AI-driven brute force attacks are a sophisticated threat that targets vulnerabilities in both security and system performance. Windows 10 and 11 users must be proactive by strengthening passwords, disabling unused access points, enabling lockout policies, and keeping systems updated. For ongoing protection and recovery, Fortect provides a reliable solution that surpasses traditional antivirus software. It scans for threats, fixes system errors, and keeps your PC running at peak performance, all while guarding you against advanced attacks, not AI-powered brute force methods, but other AI-driven malware as well.



