12 Common Cyberattacks and How to Prevent Them
Cyberattacks have become more sophisticated, more frequent, and more damaging. Whether you’re an individual or a business using Windows 10 or 11, understanding the most common cyber threats and how to prevent them is key to staying secure. Below, we’ll explore the top 12 cyberattacks and give you actionable prevention tips.
1. Phishing Attacks are a Common Cyberattack

Phishing tricks users into revealing sensitive information, such as passwords, credit card numbers, or personal data, through fake emails, websites, or text messages.
How to Prevent It
- Never click on suspicious links.
- Use email filters and spam blockers.
- Enable two-factor authentication (2FA).
- Regularly update your security software.
2. Ransomware
Ransomware encrypts your files and demands payment in exchange for decryption.
How to Prevent It
- Backup important files regularly.
- Avoid downloading unknown attachments.
- Use robust antivirus software with real-time protection.
3. Malware Attacks
Malware is malicious software designed to disrupt, damage, or gain unauthorized access to a system.
How to Prevent It
- Keep your OS and apps updated.
- Avoid pirated software.
- Use a trusted antivirus solution.
4. Man-in-the-Middle (MitM) Attacks
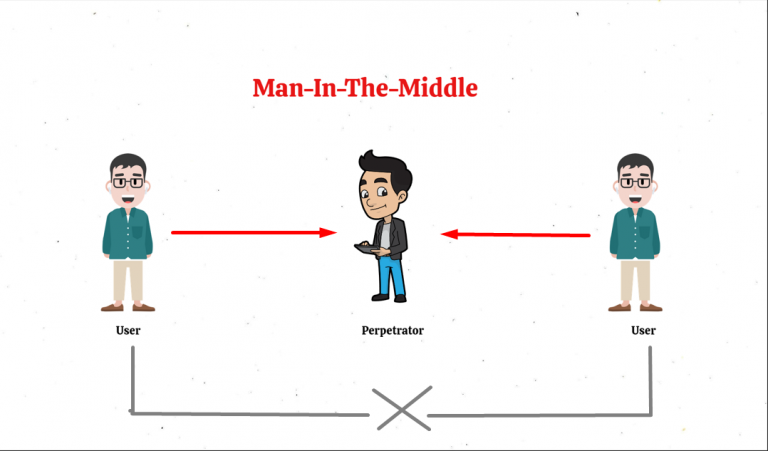
Man-in-the-Middle attacks intercept communications between two parties to steal or manipulate data.
How to Prevent It
- Avoid using public Wi-Fi without a VPN.
- Always ensure websites use HTTPS.
- Use strong encryption protocols.
5. Denial-of-Service (DoS) Attacks
Attackers flood a system with traffic, making it inaccessible to users.
How to Prevent It
- Use firewalls and intrusion detection systems.
- Implement network traffic monitoring.
- Keep all software patched and updated.
6. SQL Injection
A code injection technique that can destroy your database by inserting malicious SQL statements into input fields.
How to Prevent It
- Use parameterized queries.
- Regularly test your database for vulnerabilities.
- Limit database permissions.
7. Zero-Day Exploits
Zero-day attacks occur on the same day a vulnerability is discovered and before a patch is released.
How to Prevent It
- Keep your OS and software updated.
- Use advanced threat detection tools.
- Apply patches as soon as they’re released.
8. Credential Stuffing
Hackers use leaked username-password pairs from previous breaches to gain access to new accounts.
How to Prevent It
- Never reuse passwords.
- Use a password manager.
- Enable 2FA wherever possible.
9. Spyware
Spyware secretly monitors user activity and collects information without consent.
How to Prevent It
- Use anti-spyware tools.
- Avoid installing software from unverified sources.
- Keep your system updated.
10. Cross-Site Scripting (XSS)
Attackers inject malicious scripts into websites, affecting site visitors.
How to Prevent It
- Validate and sanitize user inputs.
- Use security headers like Content Security Policy (CSP).
- Keep your web applications up to date.
11. Drive-by Downloads
Malicious code is downloaded onto your device without your knowledge when visiting a compromised website.
How to Prevent It
- Keep your browser updated.
- Enable pop-up blockers.
- Use a web security solution like Fortect Browsing Protection.
12. Rootkits
Rootkits are deeply embedded in a system, allowing attackers to control it remotely.
How to Prevent It
- Use a powerful antivirus.
- Monitor unusual system behavior.
- Regularly scan and clean your system.
To Protect Your System From Common Cyberattacks, Use Fortect
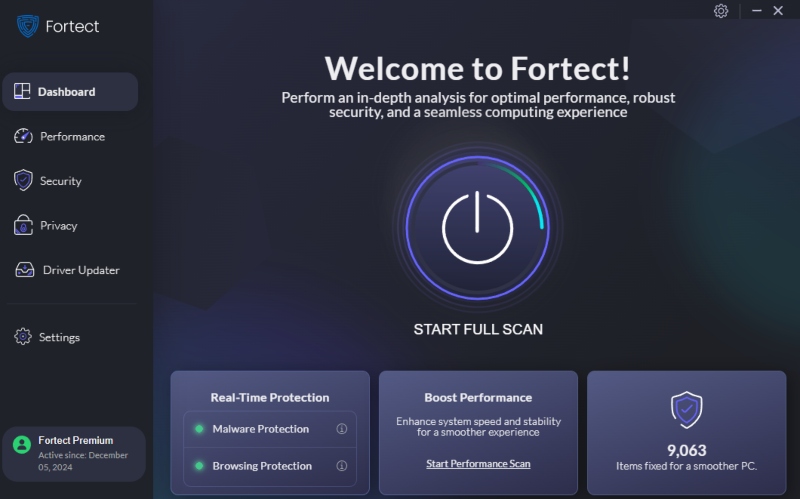
Fortect is a powerful antivirus and system optimizer with real-time malware protection. It automatically scans your Windows 10/11 PC for threats like malware, spyware, and corrupted system files, then repairs and optimizes your system for peak performance.
How to Use Fortect on Windows 10/11:
- Download and install Fortect from the official website
- Launch the app and run a full scan.
- Let Fortect detect and remove malware, fix corrupted files, and clean junk.
- Enable real-time protection for continuous defense.
Other Key Features of Fortect
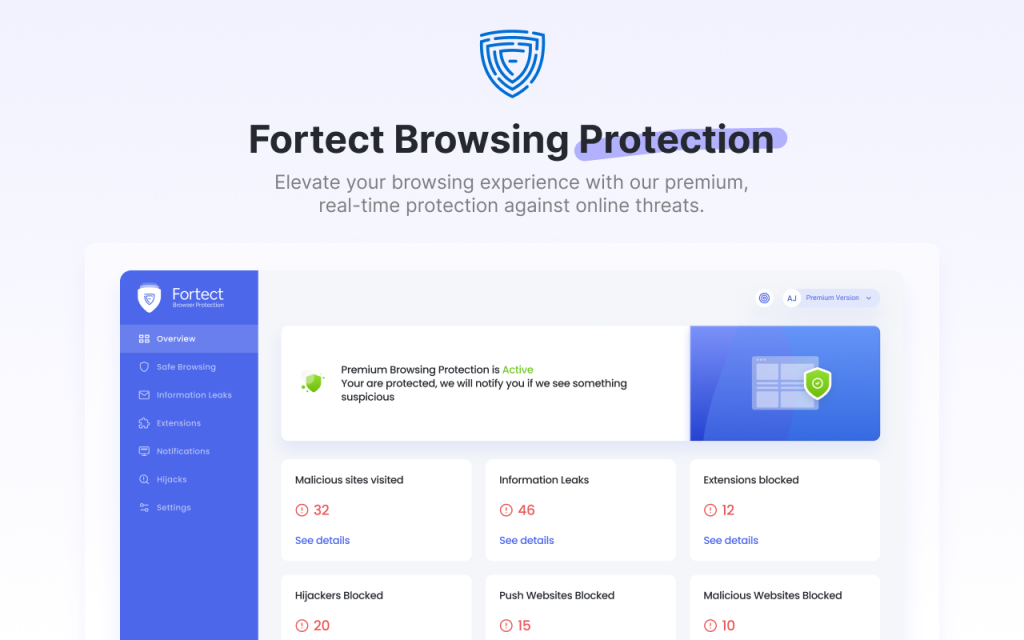
- Fortect Browsing Protection for Chrome: A powerful extension that offers real-time protection against malicious websites and phishing attacks.
- Cross-Platform Functionality: Fortect Premium users can extend protection to Android devices.
- Fortect Mobile Security: Stay secure on Android with features like: Real-Time Threat Blocking, Malware Detection & Removal and more
Conclusion
Cyberattacks can target anyone, but they’re preventable. By understanding common threats, investing in cybersecurity training, and using tools like Fortect, you can stay one step ahead. Don’t wait for a breach, start protecting your data and devices today.



