10 Top Dangerous Computer Viruses & Malware in 2025
As we progress through 2025, the landscape of cybersecurity threats continues to evolve at an alarming rate. Cybercriminals are leveraging advanced tactics, including artificial intelligence and sophisticated malware strategies, to exploit vulnerabilities in computer systems. Whether you’re a home user or managing enterprise-level infrastructure, understanding these threats is crucial to safeguarding your digital environment.
How Are They Dangerous in 2025
In 2025, malware attacks have become more targeted and complex. Ransomware-as-a-Service (RaaS) platforms have democratized cybercrime, allowing even novice hackers to launch devastating attacks. Fileless malware and AI-driven threats are increasingly bypassing traditional security measures, making detection and prevention more challenging. Additionally, the rise of remote work and cloud services has expanded the attack surface, providing cybercriminals with more entry points into systems.
Top 10 Dangerous Viruses for 2025
Phobos Ransomware
Phobos continues to be a significant threat in 2025, known for its rapid encryption capabilities and targeted attacks on enterprises. It often spreads through phishing emails and vulnerable Remote Desktop Protocol (RDP) connections.
Mobile Malware
As mobile devices become central to both work and personal life, mobile malware is on the rise. These malicious programs can steal sensitive information, monitor user activity, and even take control of devices remotely. A recent example ( 2025 ) is the SparkKitty Trojan, which specifically targets Android and iOS devices, highlighting the growing threat to mobile security.
Lumma
Lumma is a new variant of ransomware that emerged in 2025. It uses advanced encryption techniques and often targets healthcare and financial sectors, demanding high ransoms for data decryption.
Fileless Malware
Fileless malware operates entirely in memory; fileless malware avoids detection by traditional antivirus software. It exploits system vulnerabilities and can remain undetected for extended periods, causing significant damage.
Ransomware-as-a-Service (RaaS)
RaaS platforms have proliferated, enabling cybercriminals to rent ransomware tools and launch attacks without deep technical knowledge. This has led to an increase in ransomware attacks across various industries.
Windows Update Ransomware (Cyborg)
This malware disguises itself as a legitimate Windows update, tricking users into installing it. Once activated, it encrypts files and demands a ransom for decryption.
Phishing Improves with AI
Phishing attacks have become more sophisticated with the integration of AI. Cybercriminals use AI to craft convincing emails and messages that mimic legitimate sources, increasing the likelihood of successful attacks.
Remcos

Remcos is a Remote Access Trojan (RAT) that allows attackers to control infected systems remotely. It is often distributed through malicious email attachments and can be used for data theft and espionage.
LockBit
LockBit 5.0, the latest iteration, has enhanced capabilities, including compatibility with Windows, Linux, and VMware ESXi platforms. It employs advanced obfuscation techniques to evade detection and is distributed through SEO poisoning and malvertising.
AsyncRAT
First appearing in 2019, AsyncRAT spread through spam emails and even used COVID-19 as a lure. Over the years, it has become a favorite tool for cybercriminals thanks to its powerful features. This trojan can record screens, log keystrokes, steal files, disable security tools, and install other malware while maintaining persistence on infected devices. By 2024, it was still active, often hidden in pirated software and even used in AI-assisted cyberattacks, making it one of the most dangerous RATs still in circulation.
How to Protect Your System from These Viruses
For Windows 10/11 Users
- Update Regularly
Ensure your system is up to date by navigating to Settings > Update & Security > Windows Update and clicking Check for updates. - Restrict User Permissions
Limit user privileges by going to Control Panel > User Accounts > Manage User Accounts and setting appropriate permissions. - Enable Real-Time Protection
Activate Windows Defender Antivirus by going to Settings > Privacy & Security > Windows Security and turning on Real-time protection. - Use Strong Passwords and MFA
Implement complex passwords and enable Multi-Factor Authentication (MFA) for added security. - Regular Backups
Use tools like File History or third-party software to back up important data regularly.
For macOS Users
- Keep macOS Updated
Go to Apple Menu > System Preferences > Software Update to check for and install updates. - Use Gatekeeper
Ensure Gatekeeper is enabled by navigating to System Preferences > Security & Privacy > General and selecting App Store and identified developers. - Install Antivirus Software
Consider reputable antivirus software to add an extra layer of protection. - Limit Application Permissions
Review and adjust app permissions in System Preferences > Security & Privacy > Privacy. - Regular Backups with Time Machine
Set up Time Machine by going to System Preferences > Time Machine and selecting a backup disk.
How Fortect Can Help
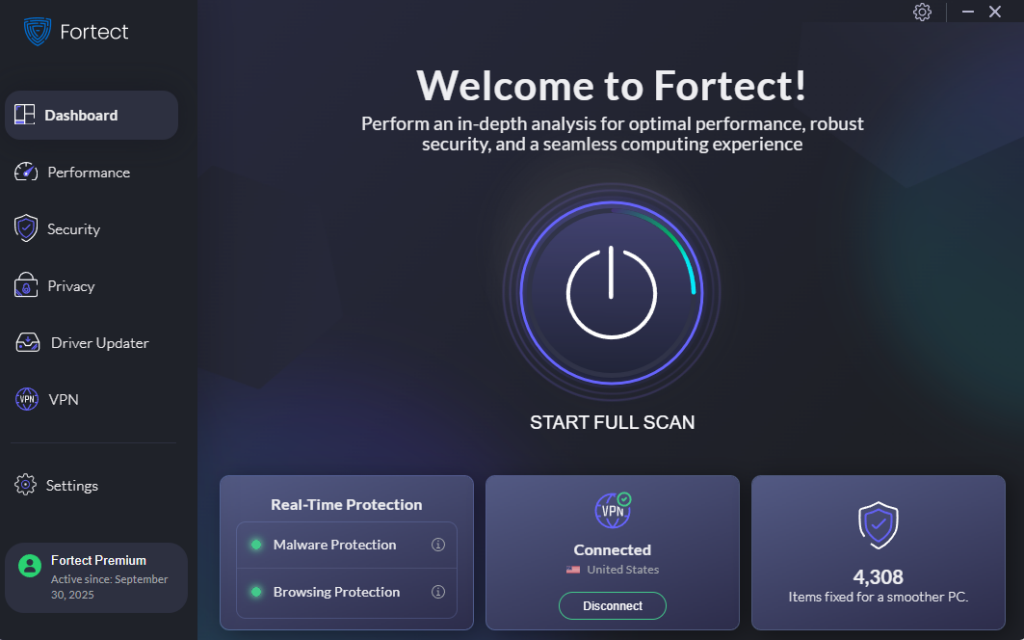
Fortect offers advanced real-time malware defense for Windows. It scans and removes threats like ransomware, trojans, and malware before they cause damage. With Fortect Premium, users benefit from a built-in driver updater that automatically repairs corrupted or outdated drivers.
Keeping drivers up to date is crucial, as cybercriminals increasingly exploit vulnerabilities in old or unpatched drivers to install ransomware, trojans, or fileless malware. Updating drivers not only improves system performance but also strengthens your defenses against emerging threats. To protect your PC, simply download Fortect, run a full system scan, repair any detected threats, enable real-time protection, and safely update all drivers using the driver updater feature.
Cybercriminals are also shifting focus to macOS as its popularity grows. Built-in defenses are no longer enough, with ransomware and malware bypassing Apple’s protections. This is where Fortect Mac Suite comes in. It offers real-time malware defense, cloud-based updates, quick smart scans, and full system scans to ensure your Mac remains safe and optimized. Whether you want fast detection or thorough deep scans, Fortect provides the balance between security and performance.
Conclusion
Cybersecurity in 2025 presents a myriad of challenges, with increasingly sophisticated malware and cyber threats. By staying informed and implementing robust security measures, you can protect your systems from these evolving dangers. Utilizing tools like Fortect can provide an added layer of defense, ensuring your digital environment remains secure.




