How to Use Sysinternals Tools to Hunt Malware in Windows
Malware threats on Windows 10 and Windows 11 continue to evolve, often hiding deep within processes and system files. While traditional antivirus software is essential, advanced users and IT professionals often rely on Sysinternals tools from Microsoft to investigate suspicious activity. These tools provide deep visibility into processes, file activity, and network connections, making them invaluable for malware hunting.
What Are Sysinternals Tools?

Sysinternals is a suite of free tools developed by Microsoft to help IT administrators and advanced users manage, diagnose, and troubleshoot Windows systems. Several of these tools are especially effective for detecting and analyzing malware.
Key tools for malware hunting include:
- Process Explorer – Displays detailed information about running processes and their loaded DLLs.
- Autoruns – Shows which programs and services start automatically with Windows.
- TCPView – Reveals all active TCP/UDP connections.
- Process Monitor (ProcMon) – Tracks file system, registry, and process/thread activity in real time.
Why Use Sysinternals Tools for Malware Hunting?
Unlike traditional antivirus tools that rely on signatures, Sysinternals tools give you manual insight into how processes behave. This helps in detecting suspicious processes running in the background, identifying malicious DLL injections or unusual startup entries, monitoring suspicious network connections, and tracing registry or file system changes caused by malware.
How to Use Sysinternals Tools to Detect Malware
Process Explorer: Investigate Running Processes
Process Explorer lets you identify which files and DLLs a process is using.
Steps:
- Download Process Explorer from the Microsoft Sysinternals website.
- Run it as Administrator.
- Look for unfamiliar processes with no verified publisher.
- Right-click a suspicious process and choose Properties to check its path and digital signature.
- Use VirusTotal integration (built-in) to scan processes online.
Restrict User Privileges
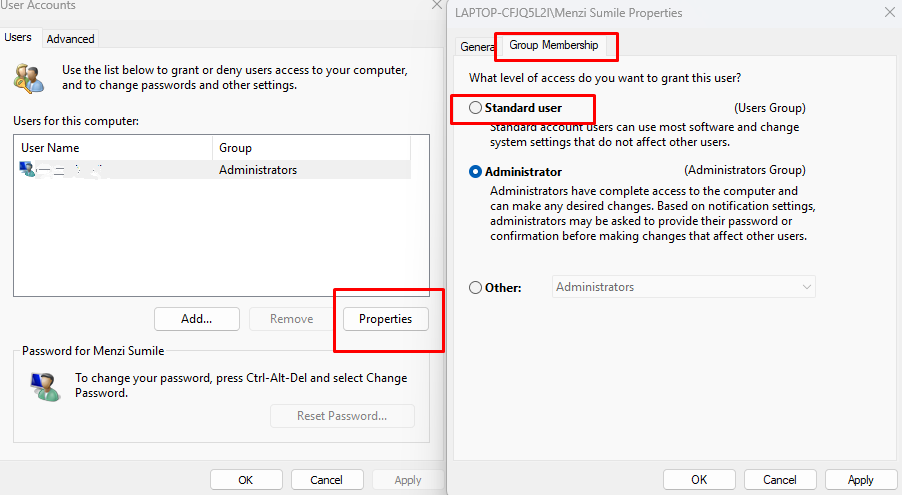
Limit admin rights to prevent unauthorized software installation.
- Press Windows + R, type netplwiz, and press Enter.
- Select a user account and click Properties.
- Under Group Membership, select Standard User.
- Click Apply and OK.
Autoruns: Check Startup Entries
Malware often adds itself to startup programs. Autoruns helps you review all startup locations.
Steps:
- Download Autoruns and run it as Administrator.
- Go to the Logon tab to check apps that launch with Windows.
- Disable or delete entries that look suspicious or lack valid publishers.
- Use the Everything tab for a full overview of autostart entries.
TCPView: Monitor Network Connections
Malware frequently connects to remote servers. TCPView helps identify abnormal network activity.
Steps:
- Download and open TCPView.
- Watch for unknown processes making outbound connections.
- Right-click a suspicious process and choose End Process to terminate it.
- Note the IP addresses and investigate them further online.
Process Monitor: Track File and Registry Activity
ProcMon provides detailed logs of what processes are doing in real time.
Steps:
- Run Process Monitor as Administrator.
- Use filters (Ctrl + L) to only show suspicious processes.
- Monitor file writes, registry edits, or DLL loads.
- Export suspicious activity logs for further analysis.
How to Prevent Malware on Windows 10/11
While Sysinternals tools are excellent for malware detection, prevention is just as critical.
Keep Windows Updated
Microsoft frequently patches vulnerabilities used by malware.
- Press Windows + I to open Settings.
- Go to Update & Security (Windows 10) or Windows Update (Windows 11).
- Click Check for updates and install available patches.
Enable Windows Defender Firewall
Always keep the firewall active to block malicious traffic.
Using Fortect for Robust Malware Protection
While Sysinternals tools help detect suspicious activity, they require manual monitoring and technical knowledge. For automated protection, Fortect offers a powerful antivirus engine with real-time malware defense.
How Fortect Helps
- Scans for hidden threats such as rootkits, spyware, and malicious processes.
- Repairs system damage caused by malware infections.
- Optimizes your PC by cleaning junk files and fixing corrupted system files.
- Provides real-time monitoring to stop malware before it spreads.
Steps to Use Fortect:
- Download and install Fortect on your Windows PC.
- Launch the app and run a Full System Scan.
- Review detected threats, including malware hidden in processes.
- Click Repair All to remove threats and restore performance.
Conclusion
Sysinternals tools like Process Explorer, Autoruns, TCPView, and ProcMon provide unmatched visibility for advanced users to manually track down malware. However, prevention is equally important. By keeping Windows updated, limiting admin rights, and running robust security software like Fortect, you can stay protected from even the most sophisticated malware threats.




