How to Protect Your Windows PC from Ransomware-as-a-Service (RaaS) Attacks
Ransomware-as-a-Service (RaaS) has transformed cybercrime into a subscription-based business model, enabling even those with minimal technical expertise to launch sophisticated attacks. This evolution has led to a surge in ransomware incidents, particularly targeting Windows PCs. In this guide, we’ll explore how RaaS operates and provide actionable steps to fortify your Windows 10 or 11 system against these threats.
What Is Ransomware-as-a-Service (RaaS)?

RaaS is a cybercrime business model where developers create and sell or lease ransomware software to affiliates. These affiliates, often with minimal technical skills, can deploy the ransomware to infect systems and demand ransom payments, typically in cryptocurrency. The RaaS model has lowered the barrier to entry for cybercriminals, leading to an increase in ransomware attacks targeting individuals and organizations alike.
How RaaS Attacks Work?
RaaS attacks typically follow these steps:
- Initial Access: Affiliates gain access to a victim’s system through methods like phishing emails, exploiting vulnerabilities, or using stolen credentials.
- Deployment: The ransomware is delivered and executed on the victim’s system.
- Encryption: Files on the system are encrypted, rendering them inaccessible to the user.
- Ransom Demand: The attacker demands payment, usually in cryptocurrency, in exchange for the decryption key.
- Data Exfiltration: Some RaaS variants also steal sensitive data, threatening to release it if the ransom isn’t paid.
How to Protect Your Windows PC from RaaS Attacks
1. Keep Your System and Software Updated
Regular updates patch known vulnerabilities that attackers exploit to gain unauthorized access.
Steps to Update Windows 10/11:
- Open Settings: Press Windows + I.
- Navigate to Update & Security: Click on “Windows Update.”
- Check for Updates: Click “Check for updates” and install any available updates.
2. Use a Robust Antivirus Solution
A reputable antivirus program can detect and block ransomware before it executes.
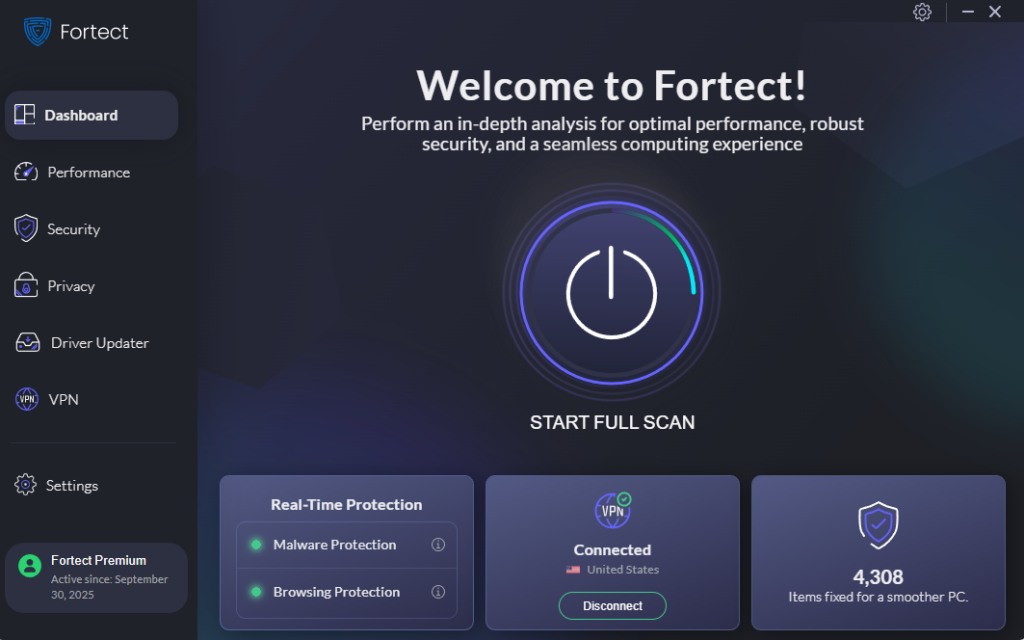
Fortect is a leading, advanced antivirus solution for Windows users offering real-time malware protection. It automatically scans your Windows PC for threats like ransomware, trojans, and other malicious software, then removes them while optimizing your system for peak performance. Recognized by TechRadar as a top-tier security tool, Fortect is praised for its real-time malware protection and built-in driver updater. With Fortect Premium, corrupted or outdated drivers are safely updated, enhancing system stability and minimizing vulnerabilities that cybercriminals often exploit.
Download and install Fortect for Windows
The good news is, Fortect now extends its protection to macOS with the Fortect Mac Suite, addressing the fact that cybercriminals are increasingly targeting Macs. Fortect Mac Suite offers real-time scanning, cloud-powered intelligence, and a robust antivirus engine to detect and block evolving threats. From quick smart scans to full system checks, it ensures comprehensive protection against malware, ransomware, and other sophisticated attacks.
Fortect Mac Suite Features:
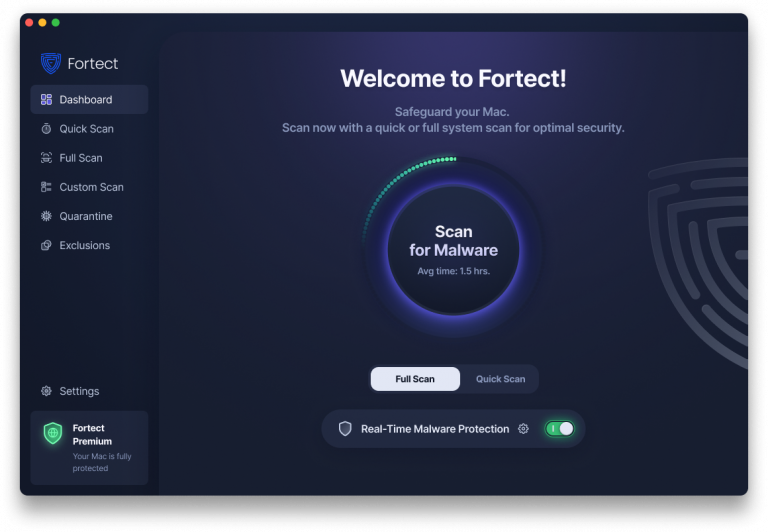
- Evolving Threats: macOS is increasingly targeted as its popularity grows.
- Ransomware and Malware Protection: Blocks advanced attacks that bypass built-in defenses.
- Gap-Filling Security: Provides real-time, advanced malware defense.
- Cloud-Based Intelligence: Uses cloud technology for real-time updates and improved threat detection.
- Quick Smart Scan: Fast scans to detect and fix issues promptly.
- Full System Scan: Comprehensive scans covering your entire system for maximum protection.
3. Enable Controlled Folder Access
This feature protects your important folders from unauthorized changes by malicious applications.
Steps to Enable Controlled Folder Access:
- Open Windows Security: Press Windows + I, go to “Privacy & Security,” then “Windows Security.”
- Navigate to Virus & Threat Protection: Click on “Manage settings” under “Virus & Threat Protection settings.”
- Enable Controlled Folder Access: Scroll down to “Controlled folder access,” click “Manage Controlled folder access,” and toggle it to “On.”
4. Implement Least Privilege Access
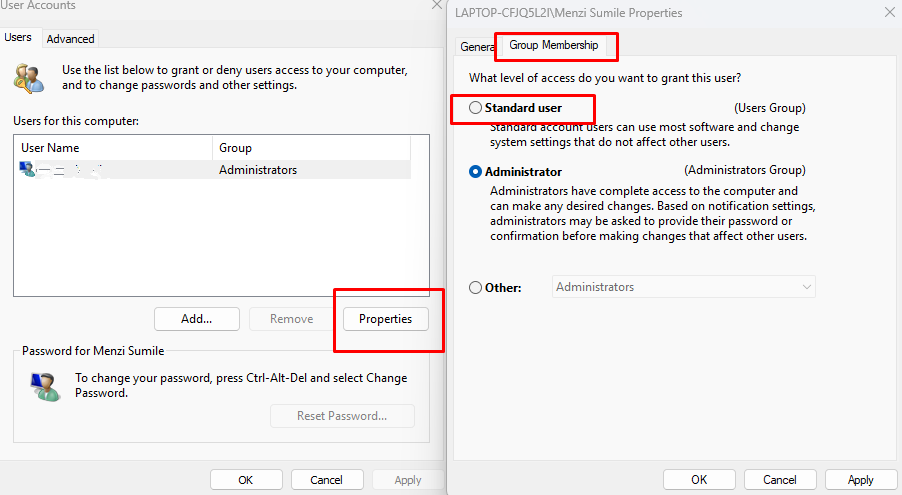
Restrict user permissions to minimize the impact of potential ransomware infections.
Steps to Restrict User Permissions:
- Open Local Users and Groups: Press Windows + R, type lusrmgr.msc, and press Enter.
- Modify User Roles: Under “Users,” right-click the user account, select “Properties,” go to the “Member Of” tab, and remove unnecessary groups like “Administrators.”
- Apply Changes: Click “Apply” and then “OK.”
5. Backup Your Data Regularly
Regular backups ensure you can restore your data in case of an attack.
Steps to Back Up Data:
- Open Settings: Press Windows + I.
- Navigate to Backup: Go to “System,” then “Storage.”
- Set Up Backup: Under “Advanced storage settings,” click “Backup options” and follow the prompts to set up File History or use OneDrive for cloud backups.
6. Educate Yourself and Others
Awareness is crucial in preventing RaaS attacks. Be cautious of unsolicited emails, suspicious links, and unknown attachments.
Training Tips:
- Recognize Phishing Attempts: Be wary of emails with urgent requests or unfamiliar senders.
- Verify Links: Hover over links to check their destination before clicking.
- Avoid Suspicious Downloads: Only download software from trusted sources.
Conclusion
Ransomware-as-a-Service has democratized cybercrime, making it accessible to a broader range of attackers. By implementing the steps outlined above, you can significantly reduce the risk of falling victim to these attacks. Remember, proactive defense is the best strategy against ransomware threats.




