How to Prevent Firmware-Level Attacks
Firmware-level attacks are among the most insidious threats in cybersecurity today. Unlike traditional malware that targets your operating system, these attacks infiltrate the firmware, the low-level software that controls your hardware. Once compromised, they can persist undetected, even after reinstalling your OS or replacing your hard drive.
This makes them particularly challenging to detect and remove. We will take a look at effective strategies to prevent firmware-level attacks, focusing on Windows 10 and 11 systems.
Understanding Firmware-Level Attacks
Firmware-level attacks exploit vulnerabilities in the firmware of devices, such as the BIOS or UEFI, to gain persistent and often undetectable control over a system. These attacks can be initiated through various vectors, including malicious updates, physical access, or compromised hardware components.
Why Are Firmware Attacks Dangerous?
Firmware operates below the operating system, granting attackers deep access to system resources. This level of access allows them to:
- Maintain persistence even after system reboots or OS reinstalls.
- Bypass traditional security measures like antivirus software.
- Potentially damage hardware components or steal sensitive data.
Given these risks, it’s crucial to implement robust security measures to protect your system’s firmware.
Best Practices to Prevent Firmware-Level Attacks
1. Keep Firmware Updated
Regularly updating your system’s firmware ensures that known vulnerabilities are patched, reducing the risk of exploitation.
Steps to Update Firmware on Windows 10/11:
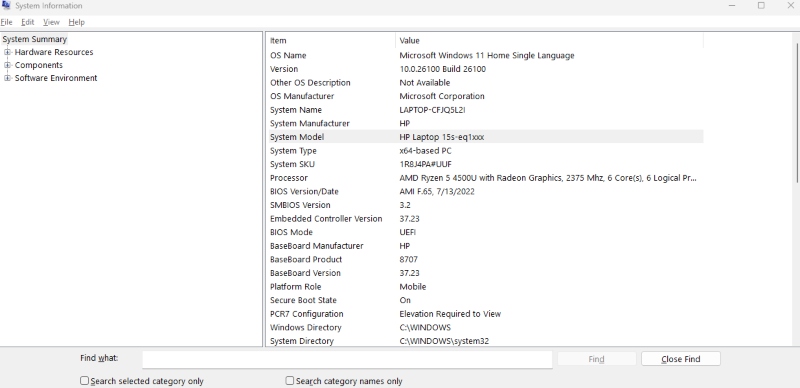
- Identify Your System Manufacturer and Model:
- Press Windows + R, type msinfo32, and press Enter.
- Note the “System Manufacturer” and “System Model”.
- Press Windows + R, type msinfo32, and press Enter.
- Visit the Manufacturer’s Support Website:
- Navigate to the official website of your system’s manufacturer.
- Locate the support or downloads section.
- Navigate to the official website of your system’s manufacturer.
- Download the Latest Firmware Update:
- Search for your specific model.
- Download the latest BIOS or UEFI firmware update.
- Search for your specific model.
- Install the Firmware Update:
- Follow the manufacturer’s instructions carefully.
- Ensure your device is connected to a reliable power source during the update.
- Follow the manufacturer’s instructions carefully.
Note: Always download firmware updates directly from the manufacturer’s official website to avoid malicious versions.
2. Enable Secure Boot
Secure Boot is a security standard developed to ensure that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM).
Steps to Enable Secure Boot:
- Access UEFI Firmware Settings:
- Press Windows + I to open Settings.
- Navigate to Update & Security > Recovery.
- Under “Advanced startup”, click Restart now.
- After the system restarts, select Troubleshoot > Advanced options > UEFI Firmware Settings.
- Click Restart.
- Press Windows + I to open Settings.
- Enable Secure Boot in UEFI Settings:
- Once in the UEFI settings, look for the Secure Boot option.
- Set it to “Enabled”.
- Save changes and exit.
- Once in the UEFI settings, look for the Secure Boot option.
Note: The exact steps may vary depending on your system’s manufacturer. Consult your device’s manual for specific instructions.
3. Utilize Windows Defender System Guard
Windows Defender System Guard provides additional protection against firmware attacks by ensuring the integrity of the system during the boot process.
Steps to Enable System Guard:
- Open Windows Security:
- Press Windows + I to open Settings.
- Navigate to Update & Security > Windows Security.
- Click on Device Security
- Press Windows + I to open Settings.
- Enable Core Isolation:
- Under “Core isolation”, click on Core isolation details.
- Toggle the switch for “Memory integrity” to “On”.
- Under “Core isolation”, click on Core isolation details.
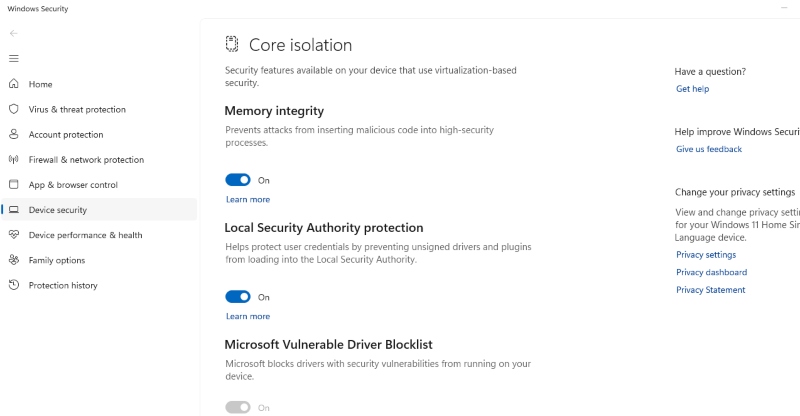
Note: Enabling Core Isolation may require a system restart. Ensure all work is saved before proceeding.
4. Restrict User Access to Firmware Settings
Limiting access to firmware settings can prevent unauthorized changes that might compromise system security.
Steps to Restrict Access:
- Set a UEFI/BIOS Password:
- Access the UEFI/BIOS settings during system startup (usually by pressing a key like F2, F10, or Delete).
- Navigate to the security settings.
- Set a strong administrator password.
- Save changes and exit.
- Access the UEFI/BIOS settings during system startup (usually by pressing a key like F2, F10, or Delete).
- Limit Physical Access:
- Ensure that only authorized personnel have physical access to the device.
- Consider using locks or secure enclosures for critical systems.
- Ensure that only authorized personnel have physical access to the device.
Note: Remember to document and securely store any passwords set to avoid being locked out of your system.
Additional Measures for Enhanced Protection
1. Use Trusted Platform Module (TPM)
TPM is a hardware-based security feature that can help protect encryption keys and prevent unauthorized firmware modifications.
2. Regularly Scan for Threats
Implementing regular system scans can help detect and mitigate potential threats before they cause significant harm.
Recommendation: Consider using third-party antivirus solutions that offer real-time protection and advanced scanning capabilities.
3. Fortify Your System with Fortect
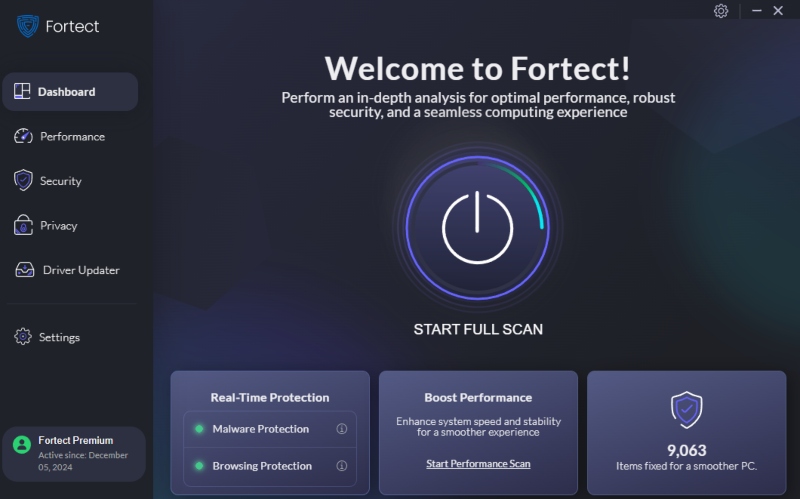
To bolster your defense against firmware-level attacks, consider using Fortect. Fortect is an antivirus solution that provides real-time malware protection. It automatically scans your Windows PC for threats, including those targeting firmware, and offers automated fixes to optimize your computer’s performance.
Key Features of Fortect:
- Real-time malware detection and removal.
- Automatic system optimization.
- User-friendly interface for easy navigation.
By integrating Fortect into your security strategy, you add an extra layer of protection against sophisticated threats that traditional antivirus solutions might miss.
Download and install Fortect today.
Conclusion
Firmware-level attacks represent a significant threat due to their stealthy nature and potential for persistent control over systems. By staying proactive, keeping firmware updated, enabling security features like Secure Boot and System Guard, restricting unauthorized access, and employing robust antivirus solutions like Fortect, you can significantly reduce the risk of such attacks. Remember, in cybersecurity, prevention is always better than a cure.



