Prevent Breaches: Detect Malicious AI Extensions
Malicious AI-powered browser extensions are fast becoming a hidden entry point for cybercriminals. These extensions, often disguised as helpful add-ons, can track your data, hijack browser sessions, and even expose your personal and financial information to third parties.
If you’re using Google Chrome, Microsoft Edge, or any Chromium-based browser on a Windows 10/11 PC, it’s essential to know how to detect these threats and stop them before they lead to breaches.
How to Remove Malicious AI Extensions on Windows 10/11
Step 1: Audit Installed Extensions
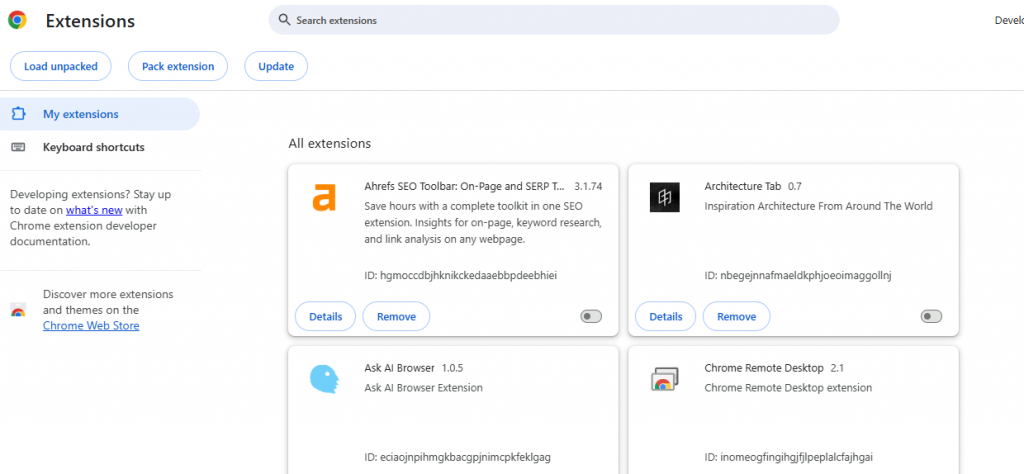
Chrome/Edge Instructions:
- Go to chrome://extensions/ or edge://extensions/.
- Identify extensions you don’t recognize.
- Click Remove on any that seem suspicious.
Step 2: Reset Your Browser
This clears lingering settings or injected scripts.
- In Chrome:
Go to Settings > Reset settings > Restore to default - In Edge:
Navigate to Settings > Reset settings > Restore settings
Step 3: Strengthen Windows Protection with Fortect
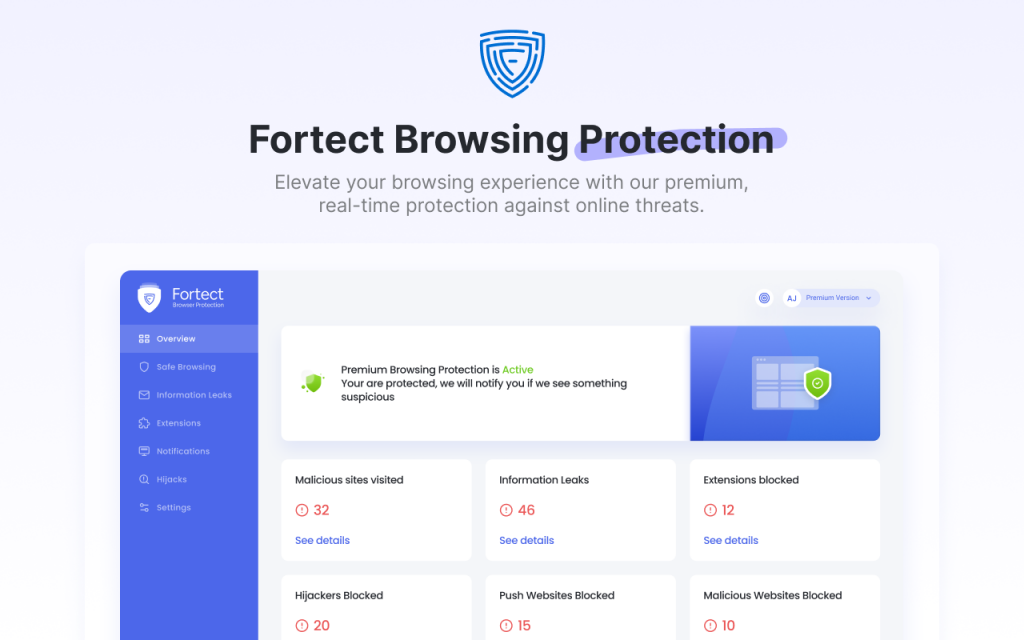
Manual removal is helpful, but not enough. Some extensions leave behind malicious scripts or redirect mechanisms. That’s where Fortect is your strongest line of defense against malicious AI extensions. Its Browsing Protection scans extensions in real time, flags suspicious behavior, and blocks threats, silently and without slowing your browser. As AI threats evolve, Fortect evolves with them.
Install Fortect Browsing Protection from the Chrome Web Store and take control of your browser’s security.
More than just protection, Fortect also repairs system files, removes malware, and optimizes performance, making it a complete solution for Windows users.
Fortect Other Features:
- Real-Time Malware Protection: Blocks AI injectors, hijackers, and adware
- File Repair: Fixes corrupted system files used by malware
- Performance Boost: Removes junk, crashed programs, and lag-causing clutter
- Fortect Mobile Security
Fortect Premium extends protection to Android devices with:
✅ Instant threat blocking
✅ Smart malware detection
✅ Real-time alerts
✅ Cloud-based, fast scanning
✅ Scheduled scans & auto-fixes
One solution. Cross-platform protection. Total peace of mind.
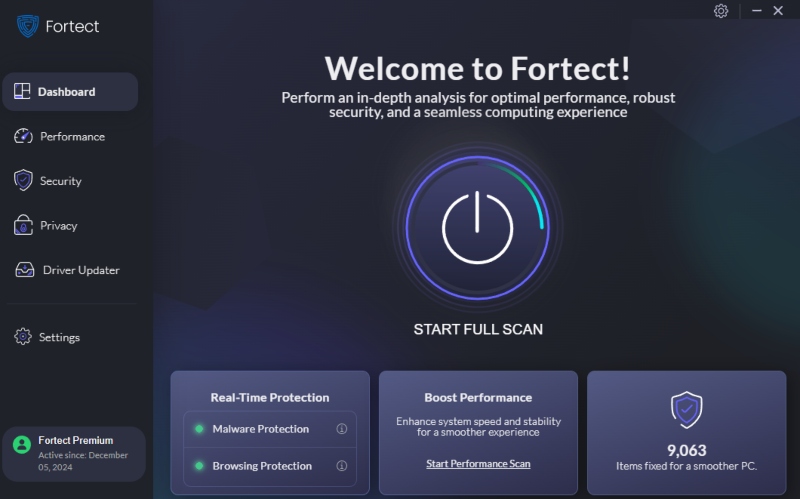
How to Use Fortect:
- Download and install Fortect for Windows.
- Click Start Scan.
- Fortect scans your PC, browser, and core files.
- Click Repair All to resolve issues and optimize your device.
Why AI Extensions Can Be Risky
While artificial intelligence enhances many browser features, it also introduces new security challenges. A malicious AI extension may:
- Log keystrokes (keylogging)
- Capture browsing data and login credentials
- Redirect you to phishing or infected websites
- Install adware or run background scripts without your knowledge
These threats often bypass basic antivirus tools and disguise themselves well, especially in newer AI-integrated plugins or extensions that seem legitimate.
Warning Signs: Is Your Browser Extension Malicious?
1. Suspicious Permissions
An extension asking for full access to all your data on every site? That’s a red flag.
2. Unusual Browser Behavior
- Random redirects to spammy websites
- Pop-ups appearing outside of trusted pages
- New tabs are opening automatically
These are typical signs of a hijacked browser.
3. Fake Reviews or New Publishers
Many harmful extensions are posted by new developers and filled with vague, copy-paste reviews.
Conclusion
AI-based browser extensions aren’t just tools; they’re potential threats hiding in plain sight. With more extensions leveraging artificial intelligence, the likelihood of data leaks, session hijacking, and phishing increases each day.
Don’t rely solely on manual detection. Fortect’s powerful suite, especially its Browsing Protection, makes it easier to detect, block, and eliminate malicious AI extensions before they compromise your browser or personal data. Start protecting your browser and system today with Fortect. It’s more than just antivirus, it’s total defense for your digital life.



